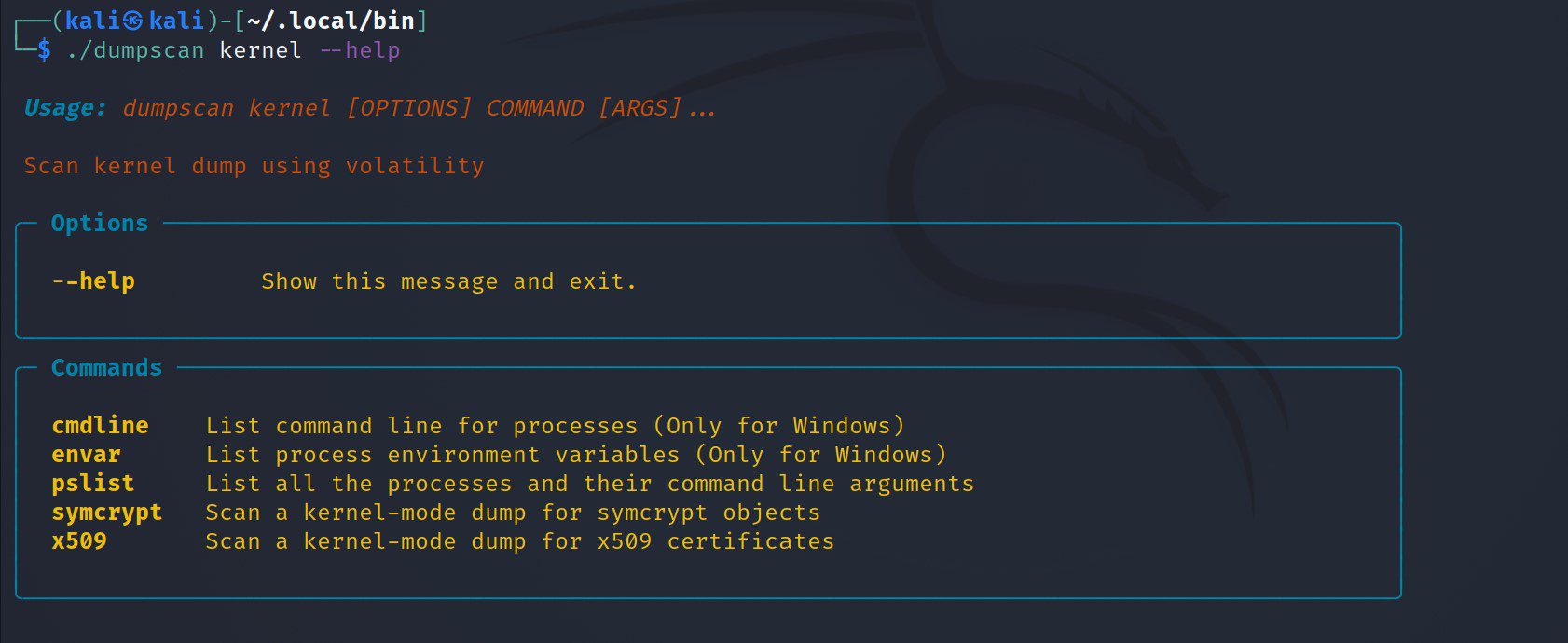
dumpscan: extract and dump secrets from kernel and Windows Minidump formats
dumpscan
Dumpscan is a command-line tool designed to extract and dump secrets from kernel and Windows Minidump formats. Kernel-dump parsing is provided by volatility3.
Features
- x509 Public and Private key (PKCS #8/PKCS #1) parsing
- SymCrypt parsing
- Supported structures
- SYMCRYPT_RSAKEY – Determines if the key structure also has a private key
- Matching to public certificates found in the same process
- More SymCrypt structures to come
- Supported structures
- Environment variables
- Command-line arguments
Note: Testing has only been performed on Windows 10 and 11 64-bit hosts and processes. Feel free to file an issue for additional versions. Linux testing TBD.
Install
As a command-line tool, installation is recommended using pipx. This allows for easy updates and well and ensuring it is installed in its own virtual environment.
pipx install dumpscan
pipx inject dumpscan git+https://github.com/volatilityfoundation/volatility3#39e812a
Use
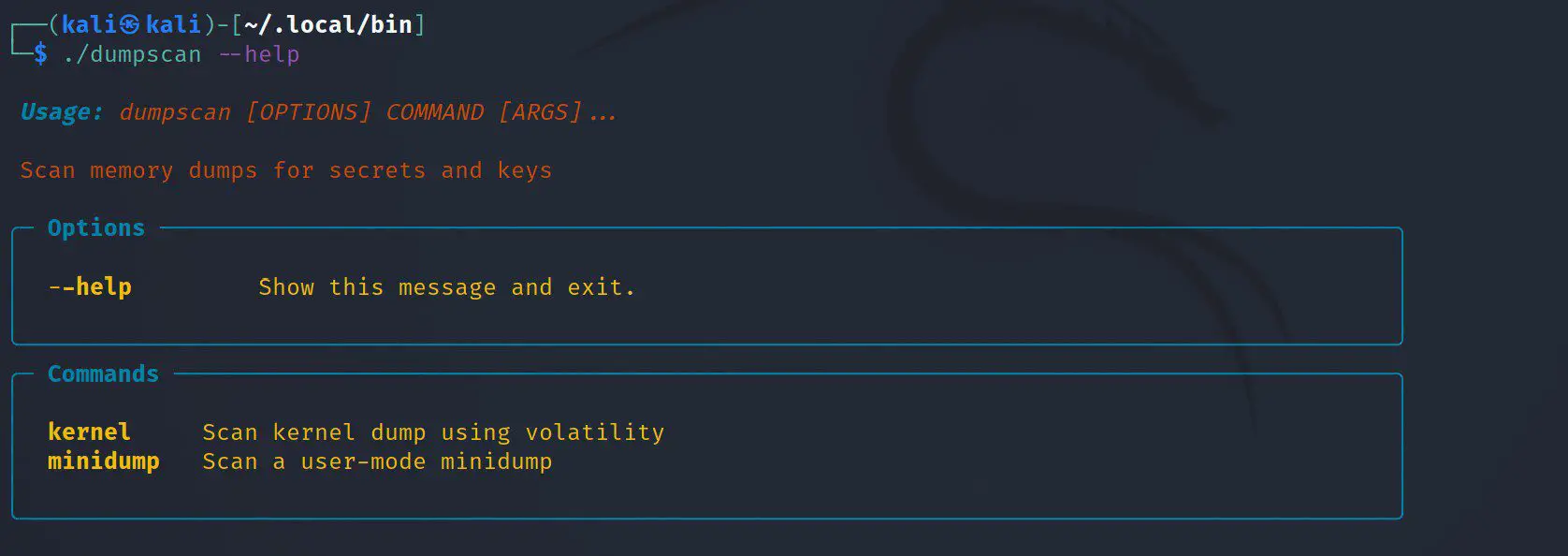
In the case of subcommands that extract certificates, you can provide –output/-o <dir> to output any discovered certificates to disk.
Kernel Mode
As mentioned, kernel analysis is performed by Volatility3. cmdline, envar, and pslist are direct calls to the Volatility3 plugins, while symcrypt and x509 are custom plugins.

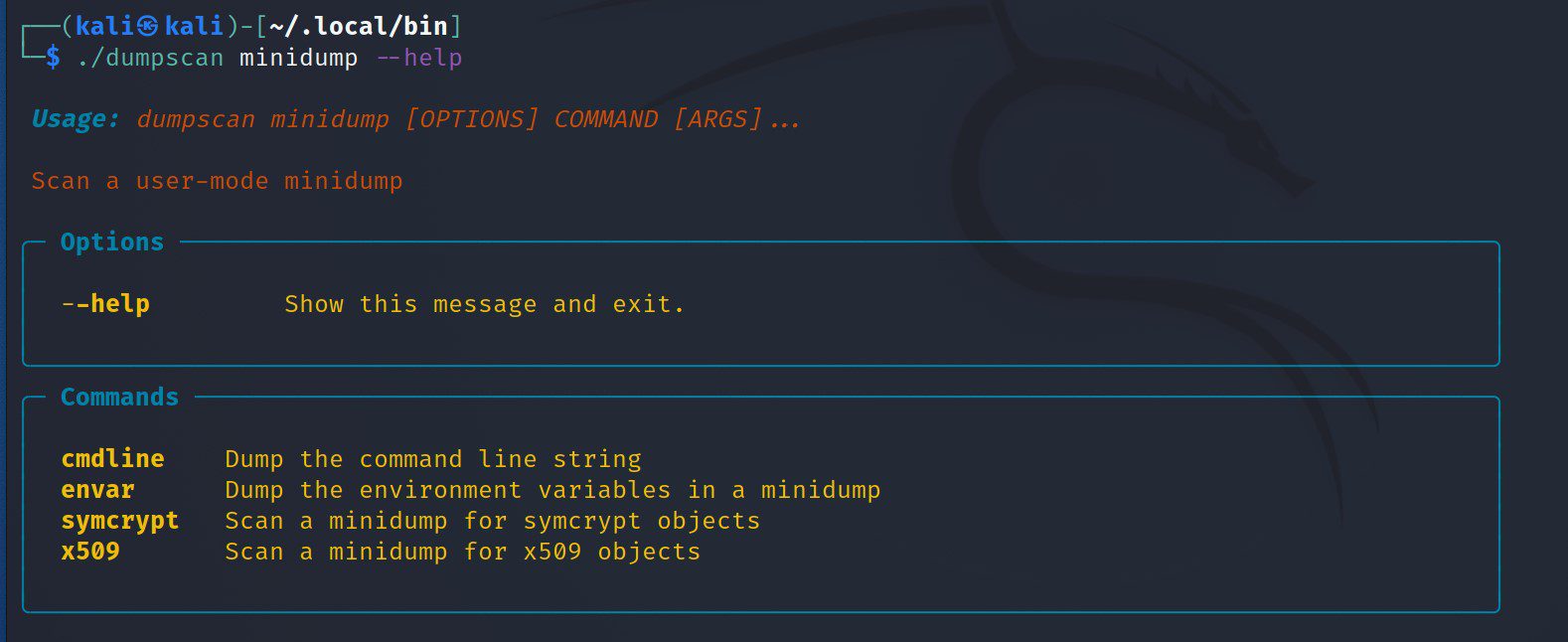
Minidump Mode
Supports Windows Minidump format.
Note: This has only been tested on 64-bit processes on Windows 10+. 32-bit processes require additional work but aren’t a priority.
Copyright (c) 2022 Leron Gray



