DVS: DCOM Vulnerability scanner
D(COM) V(ulnerability) S(canner) AKA Devious swiss army knife – Lateral movement using DCOM Objects
Did you ever wonder how you can move laterally through internal networks? Interact with remote machines without alerting EDRs?
Assuming we have valid credentials/active session with access to a remote machine, without executing a process remotely in a known,
expected or a highly-monitored method (i.e. WMI, Task Scheduler, WinRM, PowerShell Remoting).
For these scenarios, the DVS framework comes to the rescue.
The DVS framework is a swiss army knife that allows you to enumerate vulnerable functions of remote DCOM objects, launch them, and even attack using them.
The framework is being developed with a “Red Team” mindset and uses stealth methods to compromise remote machines.
The DVS framework contains various ways to bypass remote hardening against DCOM by re-enabling DCOM access remotely and automatically grant the required permissions to the attacking user.
The framework can also revert changes on the remote machine to their original state, prior to the attack.
The huge idea is that the tool can also execute commands using non-vulnerable DCOM objects using an incredible technique (Read below about Invoke-RegisterRemoteSchema)
Compatible with PowerShell 2.0 and up
Remote Registry Access (MS-RRP) – how the DVS framework utilizes that protocol
- Remote Registry access
- Probe 445 port in order to interact with the remote registry.
- Check if the remote-registry is enabled.
- Interact with the remote registry.
- If AutoGrant mode is flagged, check to write permissions. otherwise, check read permissions.
- Standard Registry Provider (If remote-registry denied)
- Probe 135 port in order to interact with Standard Registry Provider” using WMI.
- Check if the StdRegProv is accessible.
- Interact with Standard Registry Provider.
- If AutoGrant mode is flagged, check write permissions. otherwise, check read permissions.
Why is this tool so stealthy?
The DVS tool first checks if principal-identity has access to the remote machine via the following steps:
- Basic actions
- Authentication operations (if NoAuth is not flagged).
- If credentials are provided, it creates a “net-only” session. otherwise, it will use the current-logged on session.
- Probe registry access.
- Check if DCOM feature is enabled.
- Allow DCOM Access (if AutoGrant flagged), otherwise fail.
- Check if the logged-on user/provided user and the groups the user is a member of (Via adsi/WindowsIdentity feature), are granted to interact with the DCOM (via remote registry queries).
- Grant permissions (if AutoGrant flagged), otherwise, fail.
- Resolve domain name from remote machine using NetBIOS over TCP, if it fails it will try using remote registry protocol (MS-RRP).
- Authentication operations (if NoAuth is not flagged).
- Invoke-DCOMObjectScan
- Interact with DCOM objects.
- Enumerate the DCOM object and find vulnerable functions.
- Validate exploitation possibility.
- Generate execution payloads.
- Fetch personal information about the vulnerable DCOM object.
- Get-ExecutionCommand
- Generate execution payloads.
- Invoke-ExecutionCommand
- Try to interact with DCOM objects.
- Execute the commands.
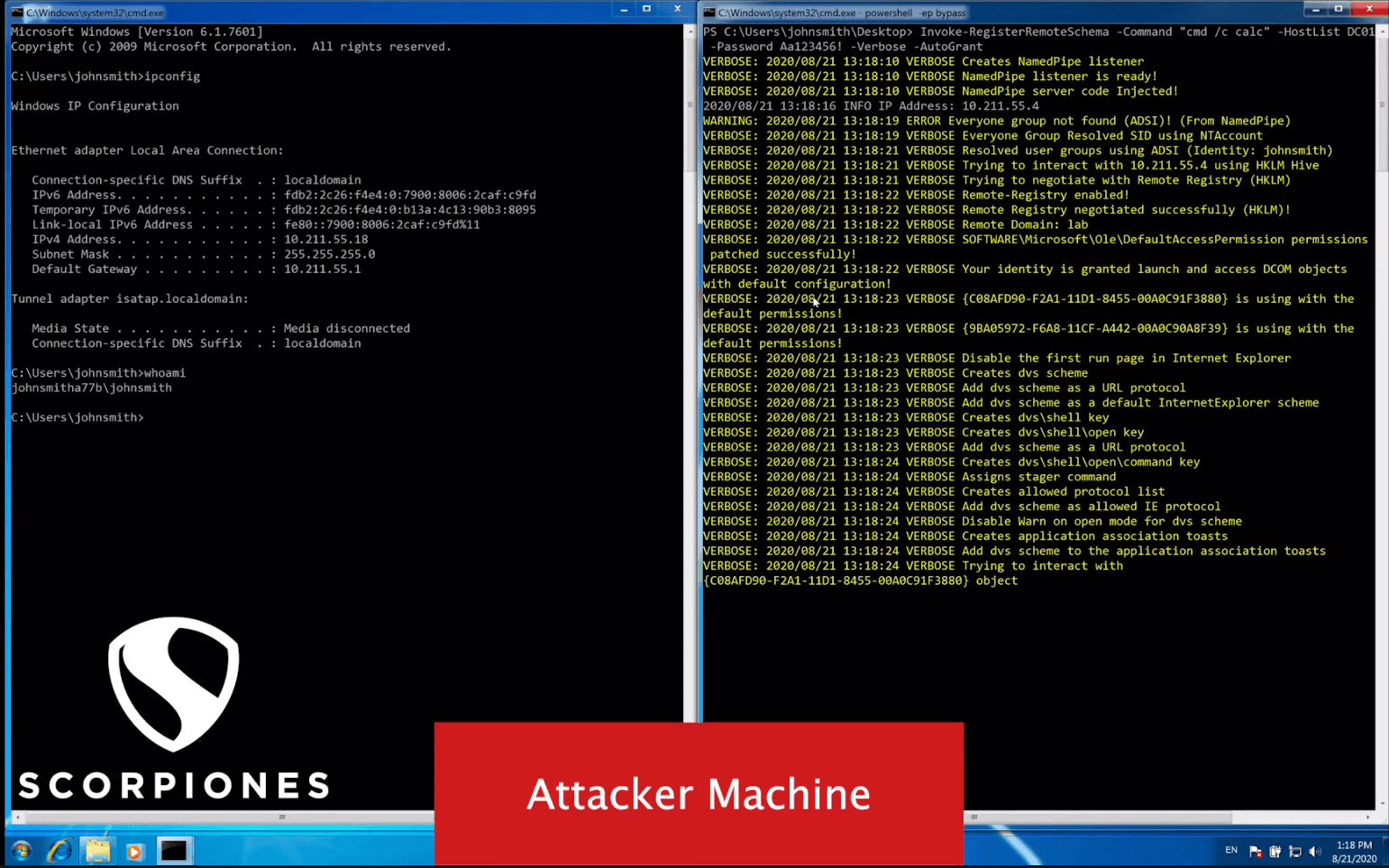
- Invoke-RegisterRemoteSchema
- Try to interact with one of the following DCOM Objects:
- InternetExplorer.Application – InternetExplorer COM Object
- {D5E8041D-920F-45e9-B8FB-B1DEB82C6E5E} – Another COMObjects belongs to Internet Explorer
- {C08AFD90-F2A1-11D1-8455-00A0C91F3880} – ShellBrowserWindow
- {9BA05972-F6A8-11CF-A442-00A0C90A8F39} – ShellWindows
- Register remote schema (e.g. http://)
- Configure the schema to execute commands from the schema content
- Execute the command
- Try to interact with one of the following DCOM Objects:
Tool components
- Security rights analyzer – Analyzing principal-identity rights to access the remote DCOM object.
- Remote grant access – Grants logged-on user permissions remotely (In case they were not already granted).
- DCOM Scanner – Scan and analyze remote/local DCOM objects for vulnerable functions that are provided (Patterns and function names must be specified). When the tool detects a vulnerable function, it will check what arguments the function includes and if the function has the ability to execute commands.
- DCOM command generator – Generates a PowerShell payload in order to execute on the remote machine.
- Report – Generates a CSV report with all the information about the vulnerable DCOM object.
- Command Execution – Execute commands through DCOM objects.
Install & Use
Demo
https://www.youtube.com/watch?v=FAjwybmFJAA
Copyright (C) 2020 Nimrod Levy





