Earth Baku APT Group Expands Global Reach with Advanced Techniques
Cybersecurity researchers at Trend Micro have uncovered a significant expansion in the activities of Earth Baku, a sophisticated advanced persistent threat (APT) group. Previously focused on the Indo-Pacific region, Earth Baku has now broadened its reach to Europe, the Middle East, and Africa (EMEA), demonstrating a concerning evolution in their tactics and targets.
Earth Baku, initially known for its operations in the Indo-Pacific, has broadened its scope, targeting nations in Europe, the Middle East, and Africa. The group’s recent campaigns have zeroed in on a wide array of sectors, including government, media, telecommunications, technology, healthcare, and education. Countries such as Italy, Germany, the UAE, and Qatar have been particularly affected, with further evidence suggesting that Georgia and Romania may also be under threat.
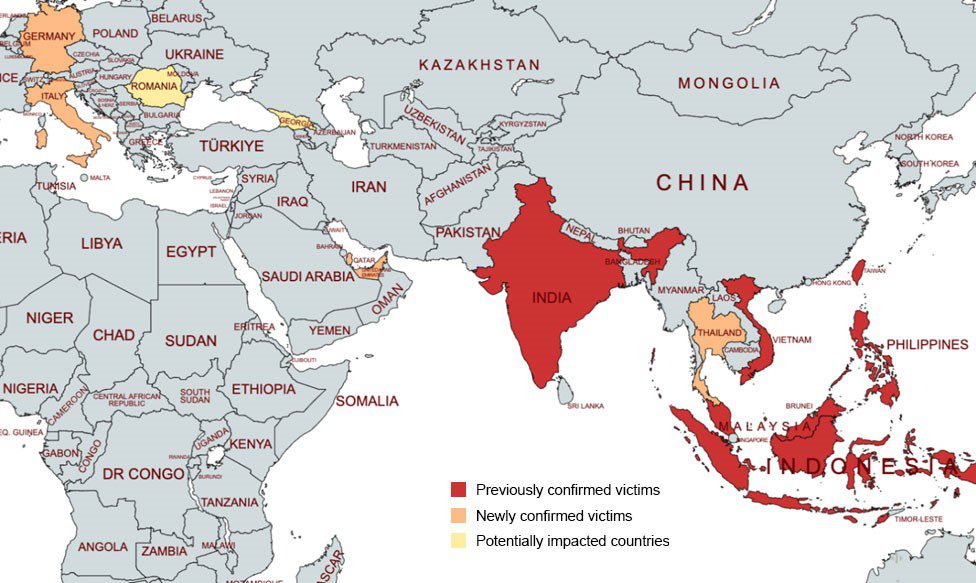
Map chart for Earth Baku’s scope of potential impact | Image: Trend Micro
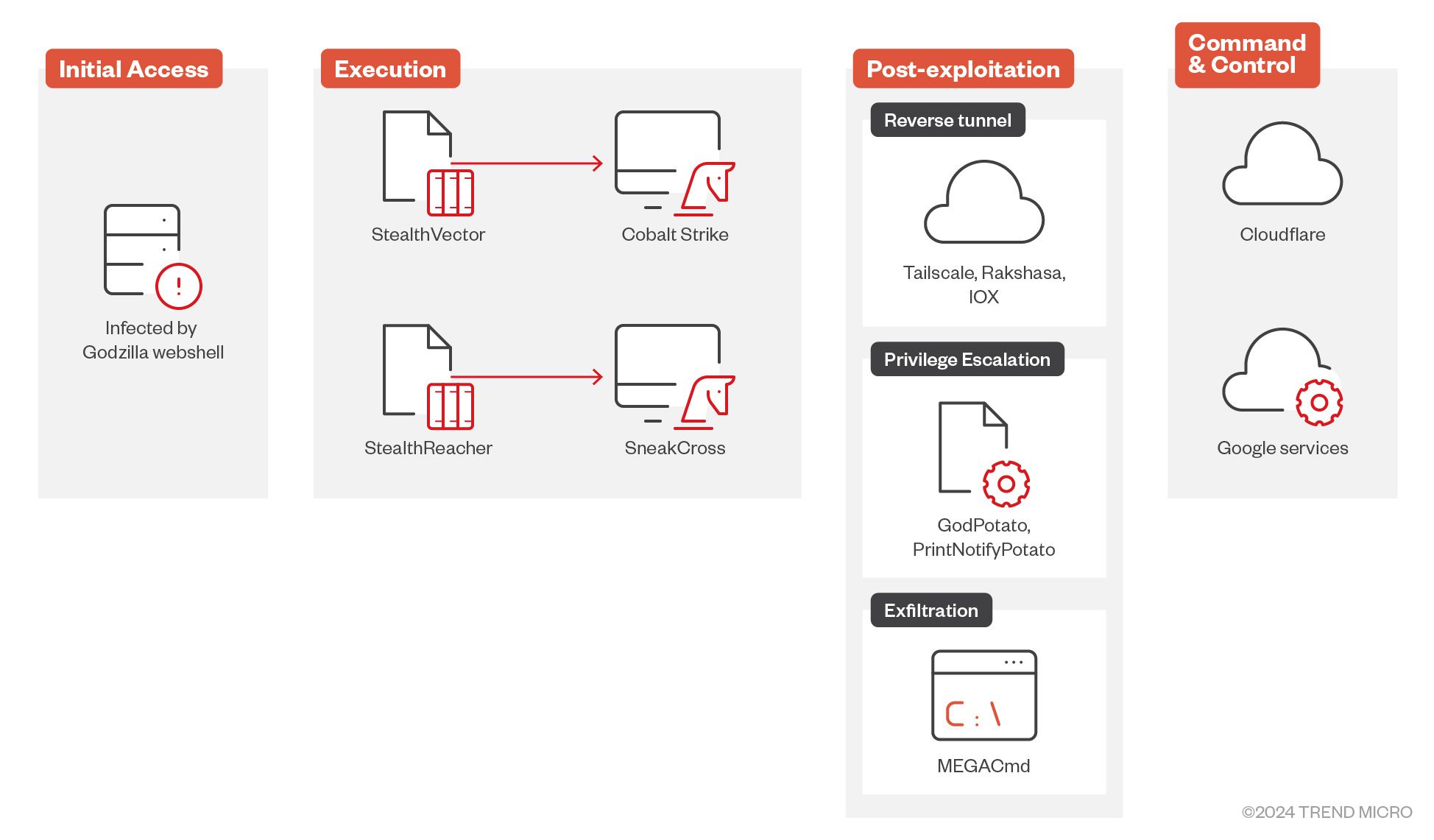
In their latest campaigns, Earth Baku has leveraged public-facing IIS servers as entry points. Upon gaining access, they deploy the Godzilla webshell, a powerful tool that allows the group to maintain control over compromised servers. Through Godzilla, Earth Baku launches a series of malicious components, including the shellcode loader StealthVector and its backdoor counterparts Cobalt Strike and the newly developed SneakCross.
These components are key to Earth Baku’s ability to move laterally within networks, maintain persistence, and execute sophisticated cyber espionage operations without detection.
StealthVector and StealthReacher are Earth Baku’s primary loaders, responsible for stealthily deploying backdoor components within victim environments. The latest iteration of StealthVector features enhanced encryption via the AES algorithm, replacing the older ChaCha20, and incorporates code virtualization for added obfuscation. It also disables critical Windows defenses like Event Tracing for Windows (ETW) and Control Flow Guard (CFG), making detection and analysis exceedingly difficult.
StealthReacher, an evolution of StealthVector, introduces additional obfuscation techniques, including FNV1-a hashing and XOR encryption, with the encryption key derived from the victim’s computer name. StealthReacher is specifically designed to deploy SneakCross, a new modular backdoor that communicates with its command-and-control (C&C) servers through Google services, effectively evading network detection tools.
SneakCross represents a significant leap in Earth Baku’s capabilities. Its modular design allows for easy updates and customization, enabling the attackers to tailor its functionality to specific targets. The backdoor’s features include everything from keylogging and file manipulation to network probing and RDP operations, making it a versatile tool for long-term espionage.
During the post-exploitation phase, Earth Baku employs a range of tools to maintain control over compromised environments and exfiltrate data. These include:
- Customized iox Tool: A modified version of the public iox tunneling tool, which Earth Baku uses for building reverse tunnels and maintaining persistent access to infected machines.
- Rakshasa: A multi-level proxy tool designed for internal network penetration, further complicating efforts to trace the attackers’ activities.
- Tailscale: A legitimate VPN service that Earth Baku has repurposed to integrate compromised systems into their virtual networks, adding another layer of obfuscation.
For data exfiltration, Earth Baku has turned to MEGAcmd, a command-line tool for interacting with MEGA cloud storage. This tool allows the attackers to efficiently upload large volumes of stolen data, exploiting MEGA’s capabilities for their malicious ends.
Related Posts:
- New China-Linked Threat Actor Earth Krahang Targets Government Entities Worldwide
- Earth Longzhi’s Cyber Attack: New Techniques Target Asia-Pacific Organizations
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- Earth Preta’s Targeted Asian Campaigns: The DOPLUGS Malware Threat
- Earth Freybug’s New Weapon: UNAPIMON Evades Detection





