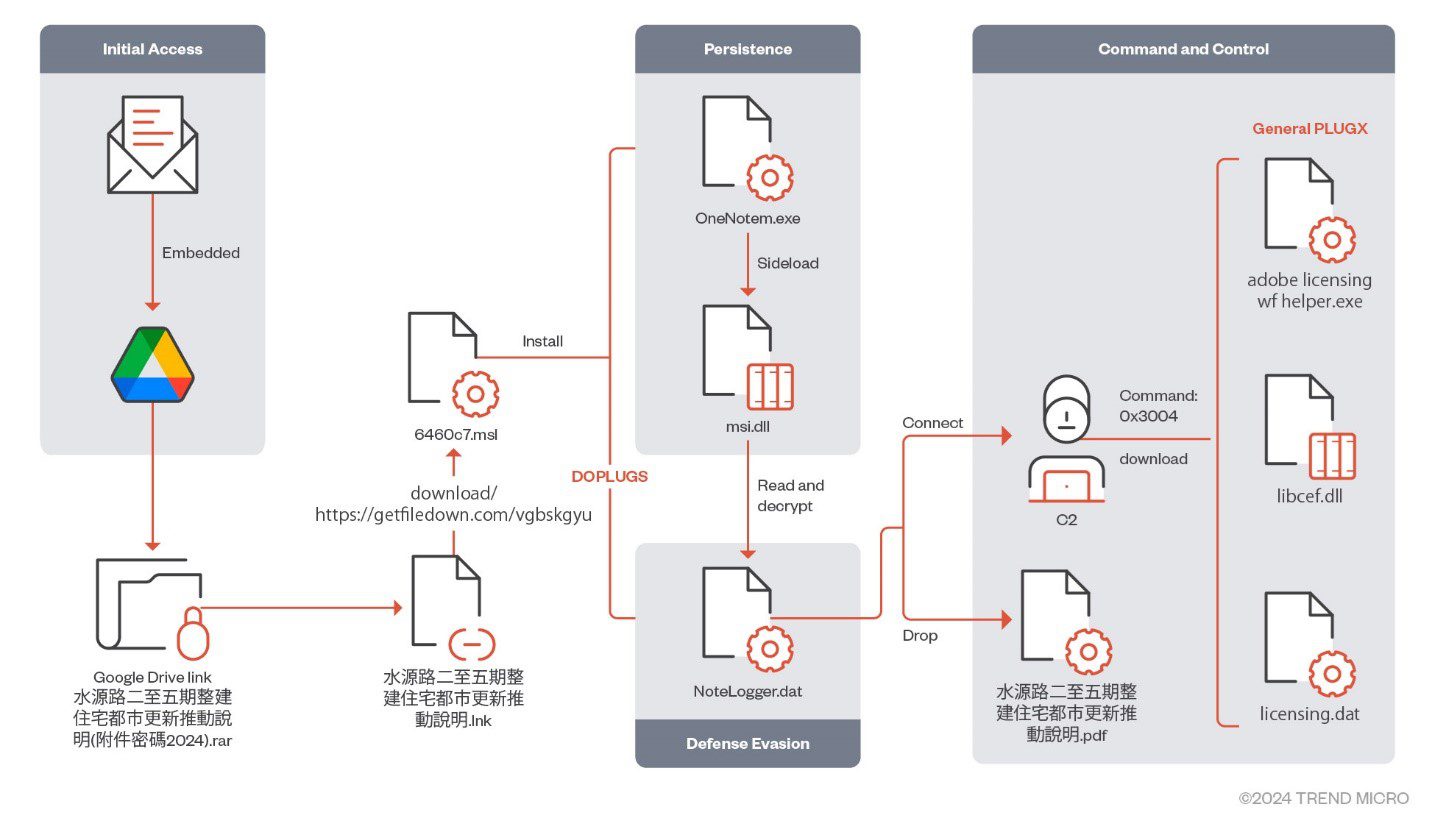
Infection flow of DOPLUGS | Image: Check Point
Check Point’s in-depth threat analysis illuminates the ongoing operations of the advanced persistent threat (APT) group Earth Preta. While extensively monitored for its European activity, a significant focus on Asian targets is undeniable. Key to this tailored strategy is a custom malware dubbed DOPLUGS, a critical tool leveraged in a range of recent intrusions.
The ‘SMUGX’ Connection: Deception and Geopolitical Targets
The discovery in 2023 of customized PlugX malware in European attacks (codename: SMUGX) and phishing campaigns directed at the Taiwanese government revealed a critical link. Check Point’s extensive research into SMUGX-related attacks identified similar operations targeting governmental, political, and diplomatic entities in Taiwan, Vietnam, Malaysia, and neighboring Asian nations.

Beyond PlugX: The Rise of DOPLUGS
Analysis revealed that this customized PlugX variant was far from typical. Check Point’s researchers recognized its unique attributes and dubbed it DOPLUGS. Unlike conventional PlugX malware with a full suite of backdoor commands, DOPLUGS exhibits a distinct specialization:
- The Downloader: Its primary function is retrieving the “full-powered” PlugX payload from command and control (C&C) servers. This multi-pronged approach aims to evade detection and maintain persistence.
KillSomeOne Connection: Lateral Worm-like Spread
Intriguingly, Check Point uncovered DOPLUGS variants capable of utilizing the ‘KillSomeOne’ USB worm (initially exposed in 2020). This added dimension facilitates swift movement throughout compromised networks, underscoring the threat group’s pursuit of wider infiltration.
The Anatomy of an Attack: Lures, Targets, and Execution
Check Point’s analysis exposes Earth Preta’s preferred techniques:
- Spear-phishing Onslaught: Highly targeted emails with password-protected archives hosted on Google Drive act as initial infection vectors, concealing DOPLUGS payloads
- Thematic Decoys: Documents tailored to resonate with geopolitical tensions within target nations increase successful infection rates. Recent themes have included Taiwanese elections and natural disasters.
- Victims: Taiwan and Vietnam emerged as primary targets, alongside attacks across China, Singapore, Hong Kong, Japan, India, Malaysia, and Mongolia.
The Evolution of DOPLUGS and Earth Preta
Through meticulous analysis, Check Point identified distinct modifications to DOPLUGS over time, reflecting the Earth Preta group’s relentless drive to stay ahead of defenses.
- Command Shifts: Since 2018, at least four generations of PlugX backdoor commands have been observed, demonstrating continuous tactical refinement
- Strategic Intent: Check Point’s investigations suggest specialized DOPLUGS versions prioritize stealth, allowing Earth Preta to operate under the radar and maximize success.
Key Takeaways and Call to Action
Check Point’s findings expose the scale and persistence of the Earth Preta threat. Their commitment to continuous analysis underscores the danger presented by this agile and determined actor. This discovery highlights several vital lessons for organizations within the group’s scope:
- Heightened Threat Awareness: Earth Preta’s unwavering focus on Asia demands unwavering vigilance from organizations in affected regions.
- User Education is Paramount: Comprehensive security awareness training should emphasize spotting sophisticated phishing tactics.
- Proactive Intelligence: Monitoring the latest attack trends and indicators of compromise (IoCs) associated with Earth Preta is crucial for keeping pace with their ever-changing methodologies.