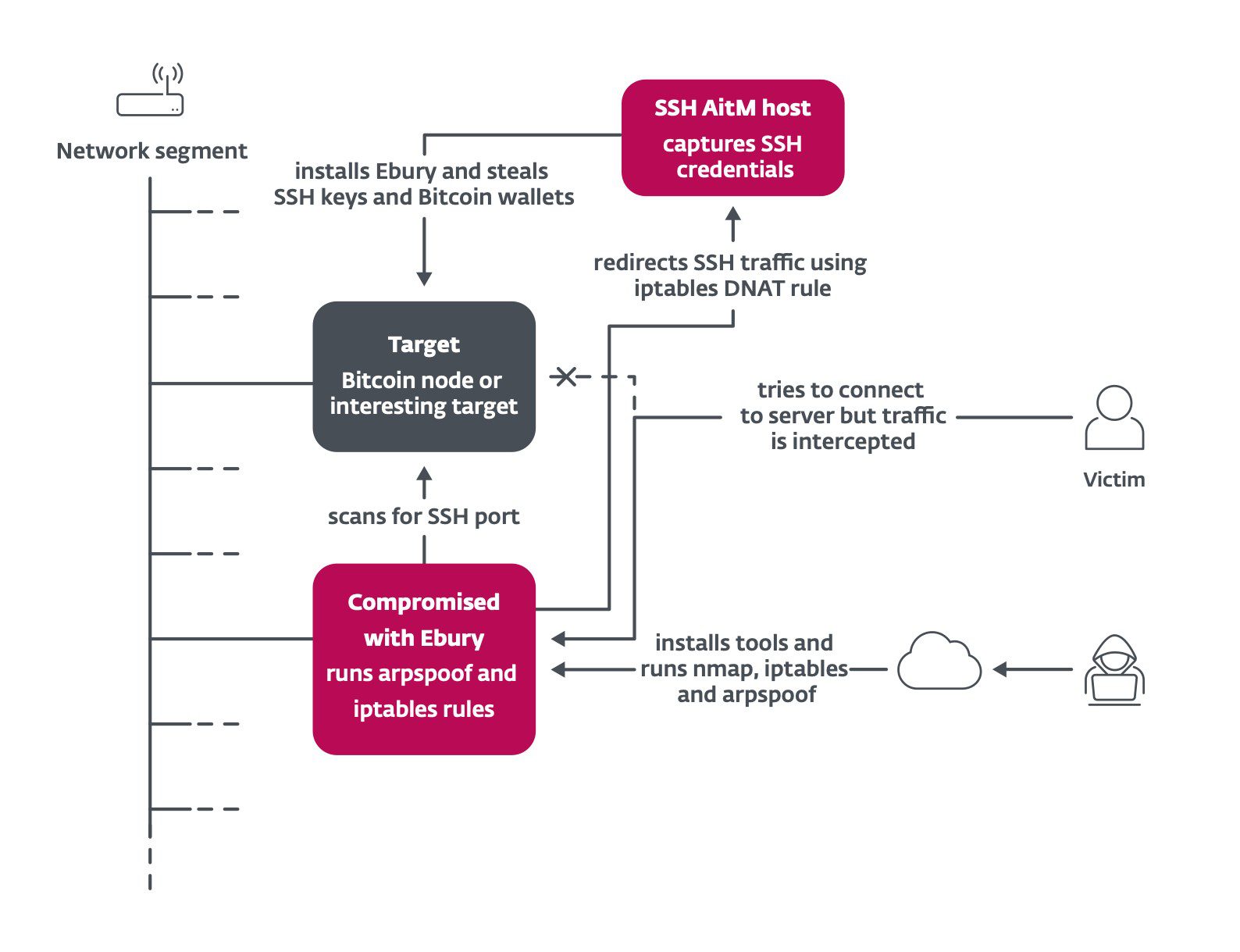
Overview of AitM attacks perpetrated by the Ebury gang | Image: ESET
In a new report, cybersecurity firm ESET has revealed the alarming scale of a decade-long cyber campaign compromising nearly 400,000 Linux servers. The report, titled “Ebury is alive but unseen,” exposes the nefarious activities of a sophisticated threat actor group leveraging the Ebury malware to steal cryptocurrency, financial data, and other sensitive information from servers worldwide.
The Ebury malware, an advanced OpenSSH backdoor, and credential stealer, has been active since at least 2009. Despite arrests and disruptions, the Ebury botnet has continued to evolve, with threat actors constantly updating their methods and expanding their reach. ESET’s collaboration with the Dutch National High Tech Crime Unit (NHTCU) has shed new light on the enduring threat posed by Ebury, revealing an extensive network of compromised servers and sophisticated monetization strategies.

Ebury propagates through various methods, including credential stuffing, exploitation of vulnerabilities, and compromising hosting providers. The malware requires root privileges to be installed, and the threat actors have developed multiple techniques to achieve this, such as exploiting zero-day vulnerabilities and using adversary-in-the-middle (AitM) attacks. Ebury is often deployed on servers via automated scripts that compromise entire infrastructures, from shared hosting environments to dedicated server providers.
Once installed, Ebury is used to deploy additional malware, including malicious Apache and nginx modules that facilitate web traffic redirection and server-side web skimming. The malware is capable of exfiltrating HTTP POST data, enabling attackers to steal credit card details and other sensitive information from e-commerce websites. Ebury operators have also been involved in cryptocurrency heists, leveraging their access to steal wallets and credentials.
The report highlights several high-profile compromises, including a large U.S.-based domain registrar and web hosting provider where 60,000 virtual servers were infected. Ebury was also found on critical infrastructure such as the Linux Foundation’s kernel.org servers and servers belonging to other threat actors, blurring attribution and complicating efforts to dismantle the botnet.
ESET provides detailed indicators of compromise (IoCs) and mitigation strategies to help system administrators detect and remove Ebury from their systems. Key recommendations include monitoring for unusual SSH activity, checking for modified libkeyutils.so files, and employing advanced endpoint detection and response (EDR) solutions to identify and block malicious activities.
The Ebury campaign represents one of the most persistent and damaging cyber threats targeting Linux servers. Despite significant efforts by law enforcement and cybersecurity professionals, the Ebury botnet remains a potent threat. Continuous vigilance and advanced security measures are essential to protect against this and other evolving cyber threats.
For a deeper dive into the Ebury malware and its implications, read the full ESET whitepaper “Ebury is alive but unseen: 400k Linux servers compromised for cryptocurrency theft and financial gain.”