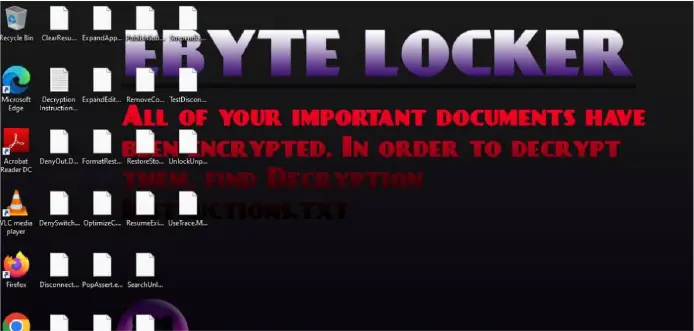
Screenshot of Wallpaper change | Image: CYFIRMA
CYFIRMA has identified a new ransomware variant, EByte Ransomware, written in Go Language and actively targeting Windows systems. This malware leverages advanced cryptographic methods, combining ChaCha20 for encryption and ECIES for secure key transmission, making file recovery nearly impossible without the attacker’s decryption tool.
The EByte Ransomware, developed by a threat actor known as EvilByteCode, has been made publicly available on GitHub. While purportedly intended for educational use, CYFIRMA warns: “Although claimed to be for educational purposes, its misuse could lead to severe legal consequences.”
The ransomware establishes persistence, executes unauthorized commands, and communicates via C2 infrastructure, posing significant cybersecurity risks to affected organizations.
EByte Ransomware is engineered to encrypt user data while avoiding critical system files, ensuring Windows remains operational while locking user files with the extension .EByteLocker. The malware:
- Scans all available drives (C:, D:, etc.) and recursively encrypts files.
- Sends a unique locker ID and a timestamp to a remote server for tracking infections.
- Modifies system wallpaper with a ransom demand using PowerShell and Windows API.
- Leaves behind a ransom note (Decryption Instructions.txt), instructing victims to contact the attackers via email for decryption.
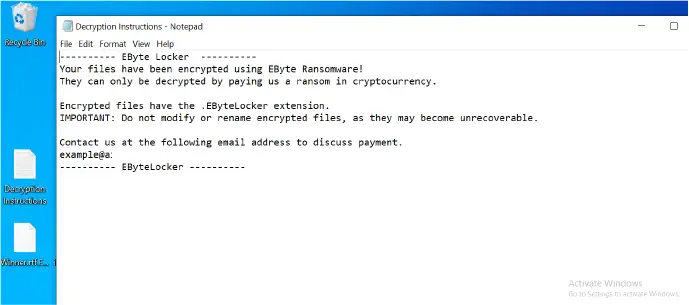
The ransomware maintains persistence using its Go-based web server: “The web server, once started, remains active and continuously processes incoming requests.”
It also allows attackers to:
- Deploy ransomware lockers via a web-based control panel.
- Maintain unauthorized access through persistent database connections.
- Exfiltrate victim data and communicate with command and control servers (C2).
EByte Ransomware is designed to evade detection by:
- Excluding system files (e.g., boot.ini, bootmgr, etc from encryption.
- Using standard HTTP traffic to blend in with legitimate network activity.
- Deleting or altering logs to prevent forensic analysis.
A decryption tool (EByte-Rware-Decryptor) is available but requires the attacker-controlled ECIES private key. Decryption involves:
- Extracting encrypted key and nonce from affected files.
- Using ECIES to decrypt the key and nonce.
- Applying ChaCha20 decryption to restore original file contents.
- Restoring system wallpaper to its default Windows state.
With EByte Ransomware publicly available on GitHub, organizations must act swiftly to bolster defenses and prevent exploitation.
Related Posts:
- Information Stealer Alert: Lumma Strikes Again with Go-Based Injector
- Bitdefender released GandCrab Ransomware decryption tool
- GoGra: New Go-Based Backdoor Targets South Asian Media
- Arctic Wolf Labs Exposes CherryLoader: A New Go-based Malware