High-level overview of the loader execution process | Image: Sophos
Sophos researchers have discovered a new threat: EDRKillShifter, a sophisticated tool designed to dismantle endpoint detection and response (EDR) systems, the very software designed to thwart ransomware attacks.
EDRKIllShifter is a sophisticated loader that delivers a variety of vulnerable drivers, enabling attackers to bypass endpoint security and execute malicious code with elevated privileges. The tool was recently observed in an attempted RansomHub ransomware attack, though it failed to disable Sophos protection on the target system.
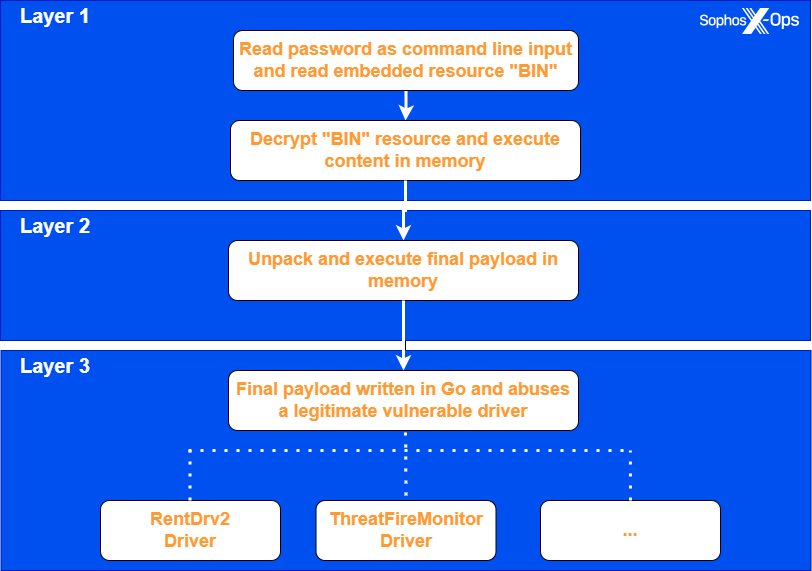
EDRKillShifter functions as a “loader” executable, a delivery mechanism for a legitimate yet vulnerable driver—a technique commonly referred to as “bring your own vulnerable driver” (BYOVD). The loader executes in three stages:
- Execution with a Password: The attacker must run EDRKillShifter with a command line that includes a specific 64-character password. If the correct password is provided, the executable decrypts an embedded resource named BIN and executes it in memory.
- Unpacking the Payload: The decrypted BIN code unpacks and executes the final payload, written in the Go programming language. This payload drops and exploits a vulnerable driver to gain the necessary privileges to unhook the EDR tool’s protection.
- Final Execution: The loader uses self-modifying code, altering its own instructions during runtime to obfuscate its behavior and make analysis difficult. The final payload is then dynamically loaded into memory and executed.
The EDRKillShifter tool employs advanced obfuscation techniques, making it challenging for security researchers to analyze its behavior. The use of self-modifying code means that the malware alters its instructions during execution, revealing its true behavior only in real-time. Additionally, the malware is written in Go and likely obfuscated using tools like gobfuscate, further complicating reverse engineering efforts.
Despite these challenges, Sophos researchers were able to extract valuable information using the GoReSym tool from Mandiant. The analysis revealed that all variants of the EDR killer embed a vulnerable driver in the .data section and behave similarly, though they exploit different drivers.
Sophos X-Ops suspects that the loader and the final payloads may be developed by different entities, indicating a possible collaboration between cybercriminal groups. While this hypothesis remains unconfirmed, it points to the increasing complexity and commercialization of cyber threats.
For more detailed analysis and insights on EDRKillShifter and its implications, visit the Sophos X-Ops blog.
Related Posts:
- HookChain: The Technique That Bypass Exposes EDR in 94% of Security Solutions
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- Unpatched Vulnerabilities: Ransomware’s Favorite Entry Point
- Critical 0-day Sophos Firewall RCE Vulnerability