EleKtra-Leak: The New Cryptojacking Menace from GitHub Repositories
Specialists from Palo Alto Networks’ Unit 42 division have identified and are closely monitoring the progression of a malevolent campaign dubbed EleKtra-Leak. This sinister initiative aims to exploit publicly posted Amazon Web Services (AWS) credentials in GitHub repositories to orchestrate cryptocurrency assaults.
Since December 2020, cybercriminals, under this campaign’s umbrella, have initiated 474 distinct instances of AWS Elastic Compute (EC2) to mine the cryptocurrency Monero, with activity documented from August 30th to October 6th, 2023.

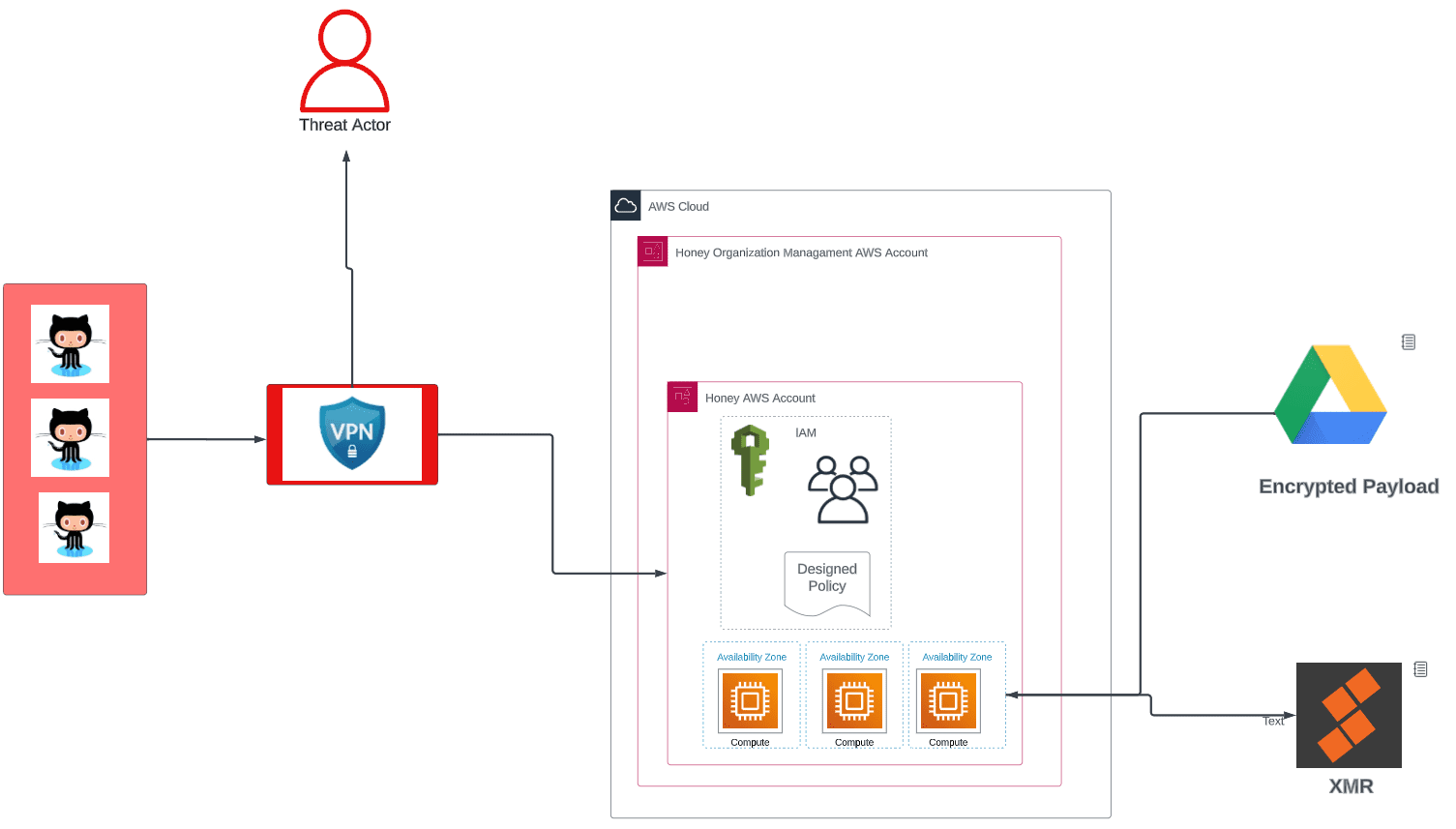
Operation CloudKeys architecture | Image: Palo Alto Networks
A striking feature of these attacks is the felons’ prowess to scan GitHub for AWS IAM keys within a mere four minutes of their disclosure. Merely five minutes thereafter, they possess the capability to configure malevolent crypto-mining operations utilizing AWS resources. Such rapidity suggests the malefactors’ employment of automated software techniques to surveil repositories and intercept information.
Parallels drawn with another crypto-jacking campaign, discerned by Intezer specialists in January 2021, led to suppositions of a nexus between the onslaughts. Both malevolent endeavors employed analogous mining software and targeted the vulnerable Docker services.
It’s noteworthy that the culprits exploit the blind spots of GitHub’s secret scanning function and AWS’s policy “AWSCompromisedKeyQuarantine” to misuse compromised IAM keys and initiate EC2 instances.
Despite AWS’s quarantine policy being implemented within two minutes of data exposure on GitHub, there are suspicions regarding the method of key leakage that clandestinely circumvents this protocol.
The miscreants pilfer AWS data to conduct reconnaissance on accounts, fabricate AWS security groups, and activate myriad EC2 instances via VPNs. The nefarious crypto-mining operations transpire on potent instances of the ilk c5a.24xlarge, facilitating an expedited accumulation of cryptocurrency.
The mining software, as researchers articulate, is fetched from URLs hosted on Google Drive, indicating malefactors’ inclinations to exploit the trust in renowned applications to obscure their undertakings.
To thwart analogous incidents, it’s imperative to promptly nullify API keys upon their breach, expunge them from GitHub repositories, and meticulously audit repository cloning events for any insidious activities.