
Kaspersky Labs has unveiled a sophisticated new ransomware variant named Elpaco, which has emerged as an evolution of the Mimic ransomware family. This advanced malware exhibits a plethora of customization features, targeting victims globally while exploiting known vulnerabilities and leveraging legitimate software tools to execute its operations stealthily.
Elpaco ransomware infiltrates systems through compromised Remote Desktop Protocol (RDP) connections, often achieved via brute force attacks. Once inside, attackers escalate their privileges by exploiting the infamous CVE-2020-1472 vulnerability, commonly referred to as Zerologon. This allows them to gain full control over the victim’s server, setting the stage for the ransomware’s deployment.
One of Elpaco’s standout features is its integration with the Everything library, a legitimate file search engine, to streamline its malicious activities. “The artifact abused this library in similar ways to the Mimic ransomware,” Kaspersky researchers noted, highlighting its use of legitimate Everything DLLs alongside malicious payloads.
Elpaco’s arsenal includes:
- Customizable Graphical User Interface (GUI): Operators can configure the ransomware’s behavior, such as altering ransom notes, selecting files and directories for encryption, and excluding specific formats.
- Sophisticated Encryption Algorithms: The malware employs the ChaCha20 stream cipher for file encryption, with its keys further secured using RSA-4096, rendering decryption nearly impossible without the private key.
- Stealth and Evasion Tactics: Elpaco deletes itself post-encryption, leveraging tools like the
fsutilcommand to securely erase its traces, ensuring minimal detection during forensic analysis.
Elpaco is distributed as a password-protected archive containing various components, including:
- Defender Control Tool (DC.exe): Used to disable Windows Defender.
- svhostss.exe: The main executable, mimicking legitimate processes to confuse analysts.
- session.tmp: A session key enabling encryption to resume if interrupted.
- gui40.exe: A GUI for operators to manage and customize ransomware parameters.
The ransomware encrypts files using a multi-threaded approach, enhancing its speed and efficiency. During its execution, detailed logs are maintained, such as the MIMIC_LOG.txt, documenting its actions for the attacker’s review.
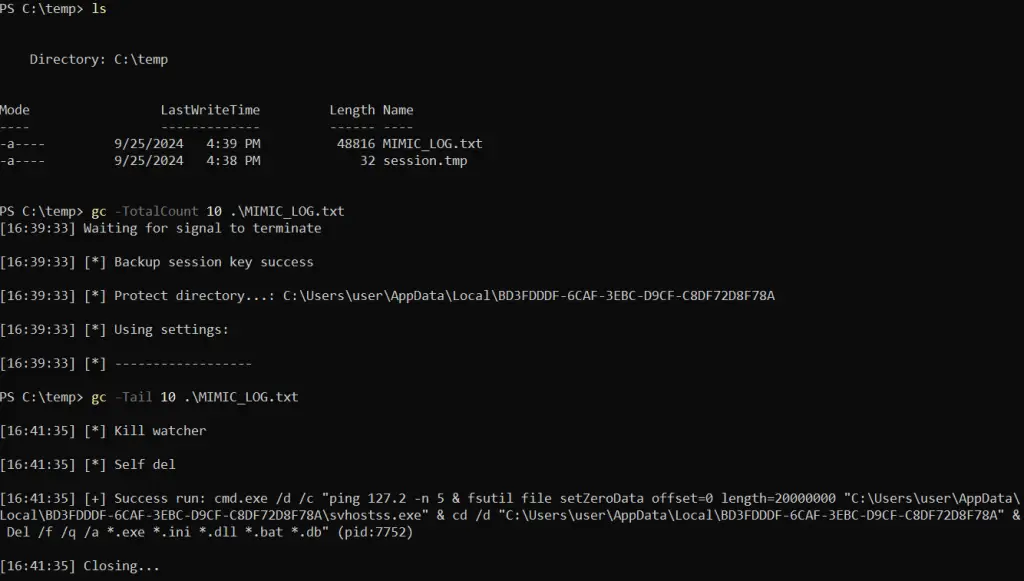
Elpaco has been linked to attacks across multiple continents, including the United States, Russia, Germany, and South Korea, with its reach extending to countries like Canada, Romania, and the UK. Evidence suggests that Mimic variants, including Elpaco, have been in use since August 2023.
Kaspersky’s researchers emphasized the significance of Elpaco’s adaptability and the threat it poses. “The artifact presented an interesting user interface for customizing its attributes, while allowing the operator to export the parameters to a configuration file,” they observed. This capability makes it highly versatile and attractive to threat actors.
Related Posts:
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware
- SambaSpy RAT Targets Italian Users in a Unique Malware Campaign
- Two New Variants of the Spectre Vulnerability were found by Security researchers