Attack flow in August and July 2024 | Image: FortiGuard Labs
Cybersecurity researchers at FortiGuard Labs have been tracking the activities of a persistent and adaptable Python-based infostealer dubbed “Emansrepo.” First observed in November 2023, Emansrepo has been distributed through phishing emails disguised as purchase orders and invoices, leading to a series of increasingly complex attack chains.
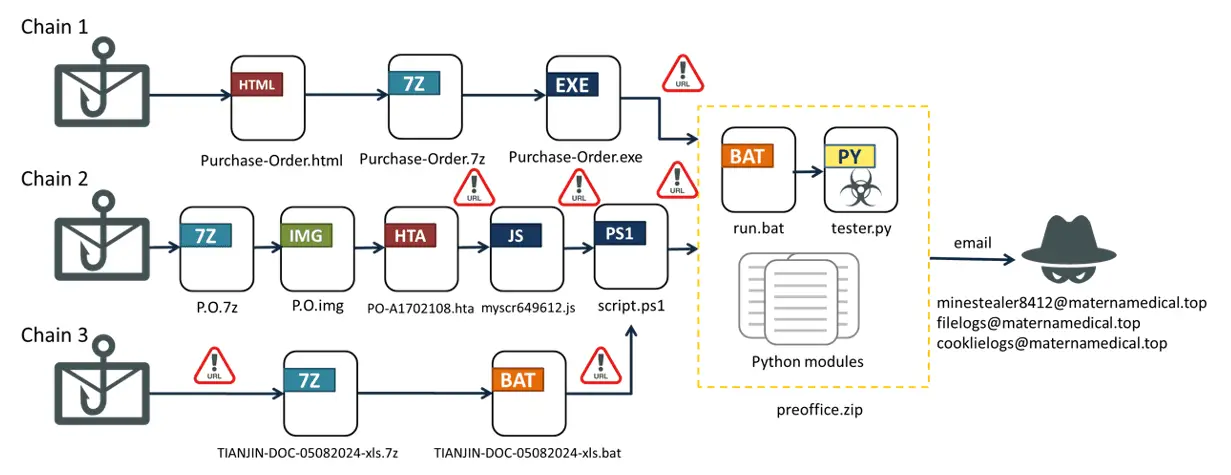
The researchers identified three distinct attack chains, each employing unique techniques to deliver the Emansrepo payload. These chains involve the use of AutoIt-compiled executables, HTA files, and BatchShield-obfuscated batch files to evade detection and ultimately execute the malicious Python script.
- Chain 1: AutoIt-Compiled Dropper The first attack chain begins with a dropper disguised as a download page. This dropper links to a file named “Purchase-Order.7z,” which contains an AutoIt-compiled executable. The AutoIt script within the executable, although obfuscated with numerous unused functions, ultimately downloads a malicious script—tester.py—to steal sensitive information from the victim’s system.
- Chain 2: HTA File Execution The second chain involves a more intricate method, where the embedded file is an HTA (HTML Application) that runs a hidden PowerShell Script Runner. This script downloads a PowerShell script (script.ps1) which, similar to the AutoIt script in Chain 1, extracts and executes the Emansrepo payload.
- Chain 3: Obfuscated Batch File The final chain utilizes a 7z file containing a batch script obfuscated by BatchShield. After deobfuscation, the script reveals its purpose: to download and run the same PowerShell script, leading to the execution of the Emansrepo infostealer.
Emansrepo itself has undergone significant development since its initial discovery. Early versions focused on collecting login credentials, credit card information, browsing history, and text files. However, newer variants have expanded their capabilities to include the exfiltration of PDF files, browser extensions, cryptocurrency wallets, game platform data, and cookies.
FortiGuard Labs has also observed a new campaign distributing Remcos malware, potentially linked to the same threat actor behind Emansrepo. This campaign utilizes a simpler attack flow, relying on DBatLoader to deliver the Remcos payload.
As attackers refine their techniques and diversify their malware arsenal, organizations must remain vigilant and adopt a proactive approach to cybersecurity.
Related Posts:
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
- Widespread WordPress Plugin Compromise in Active Supply Chain Attack
- North Korea Targets Governments, Banks, and Defense Firms in Supply Chain Attacks
- Hacker group Anonymous controls over 400 Russian cameras