emba v1.3.2 releases: analyzer for Linux-based firmware of embedded devices
emba, an analyzer for Linux-based firmware of embedded devices
Why?
emba is being developed as a firmware scanner that analyses already-extracted Linux-based firmware images. It should help you to identify and focus on the interesting areas of a huge firmware image. Although emba is optimized for offline firmware images, it can test both, live systems and extracted images. Additionally, it can also analyze kernel configurations. emba is designed to assist a penetration tester. It is not designed as a standalone tool without human interaction. emba is designed to give as much information as possible about the firmware. The tester can decide on the areas to focus on and is always responsible for verifying and interpreting the results.
How to use it?
Before starting, check that all dependencies are met and use the installer.sh script: ./emba.sh -d or ./emba.sh -d -F
Arguments:
Examples
Static firmware testing:
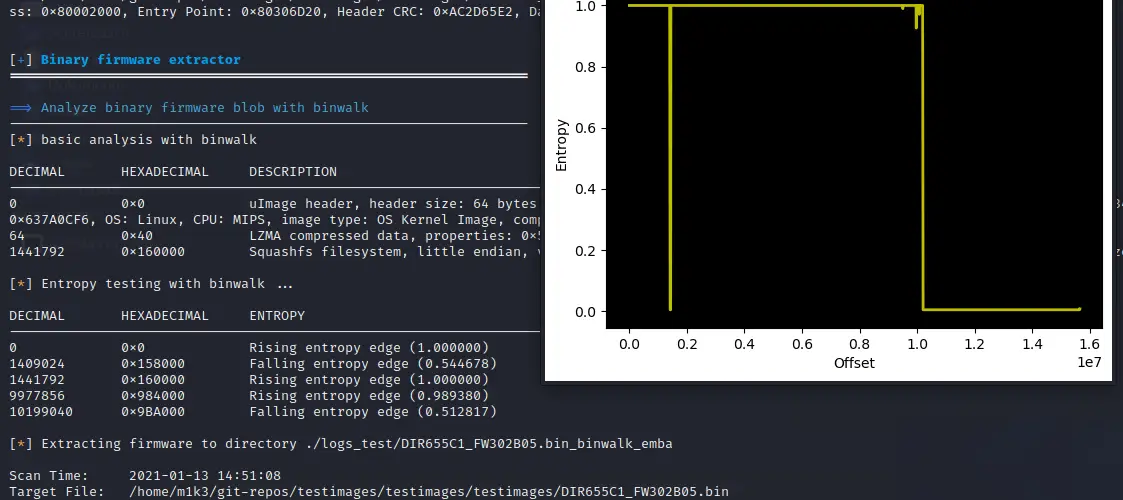
- Extract the firmware from an update file or from flash storage with binwalk or something else
- Execute emba with set parameters, e.g.
sudo ./emba.sh -l ./logs/arm_test -f ./firmware/arm_firmware/
- Path for logs and firmware path is necessary for testing successfully (WARNING: emba needs some free disk space for logging)
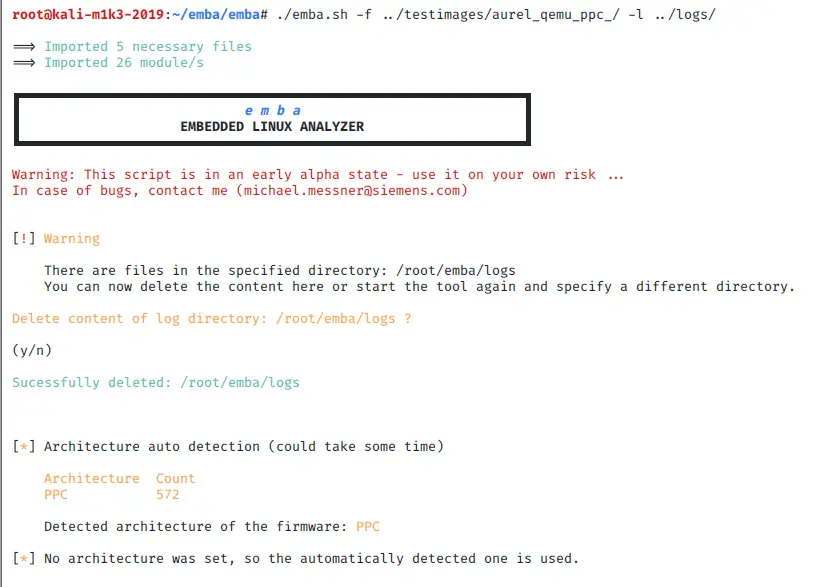
- The architecture will be detected automatically; you can overwrite it with -a [ARCH]
- Use
-A [ARCH]if you don’t want to use auto-detection for architecture - emba currently supports the following architectures: MIPS, ARM, PPC, x86, and x64
Live testing:
For testing live system with emba run it as if you were testing static firmware, but with / as firmware path:
sudo ./emba.sh -l ./logs/local_test -f /
- Path for logs and firmware path are necessary for testing successfully
- Architecture will be detected automatically; you can overwrite it with -a [ARCH]
- Use -A [ARCH] if you don’t want to use auto detection for architecture
- The paths /proc and /sys will be automatically excluded
- It improves output and performance, if you exclude docker
-e /var/lib/docker
Test kernel config:
Test only a kernel configuration with the kernel checker of checksec:
sudo ./emba.sh -l ./logs/kernel_conf -k ./kernel.config
- If you add -f ./firmware/x86_firmware/, it will ignore -k and search for a kernel config inside the firmware
Good to know:
- sudo is necessary for some modules to run properly
- Currently only tested on Kali Linux(2020.4)
- emba needs some free disk space for logging
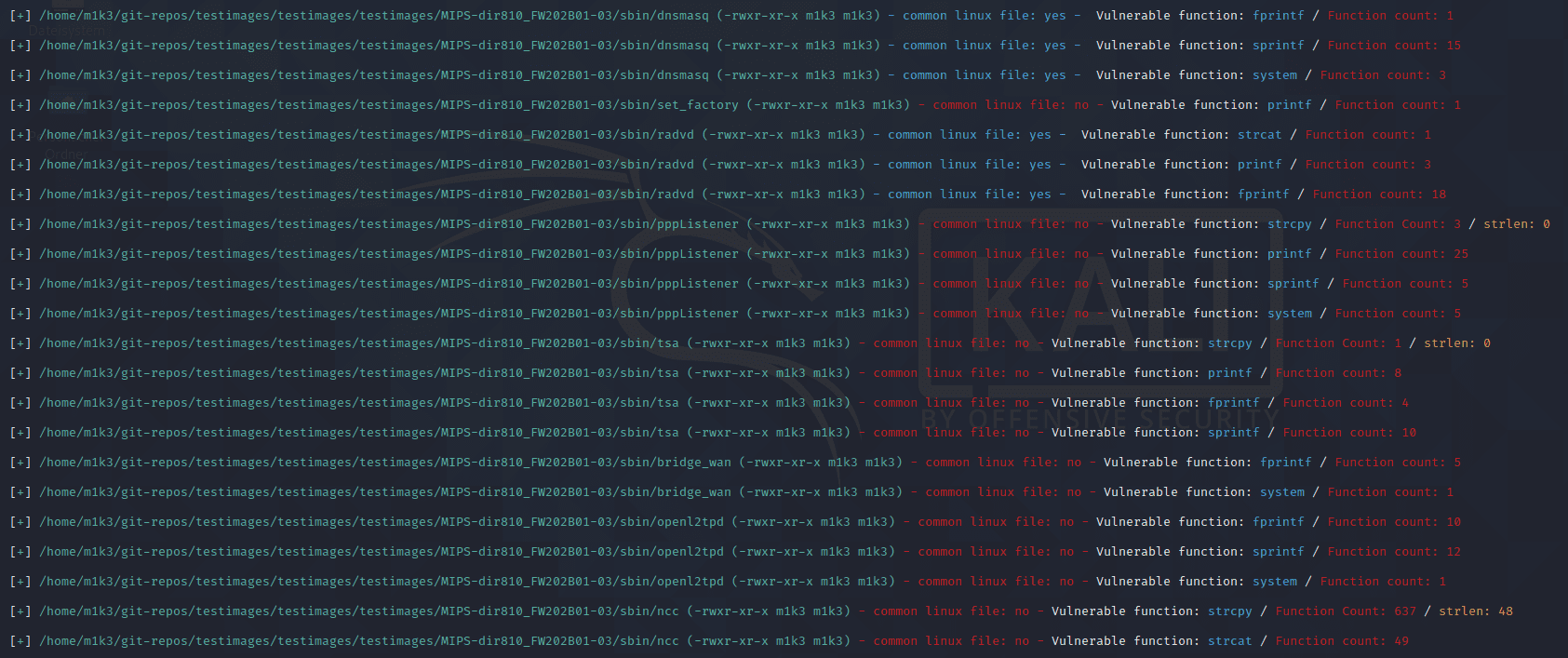
- emba uses well-known tools like objdump, LinEnum, checksec, linux-exploit-suggester.sh, cwe-checker
- emba includes multiple modules of the well known Linux analyser Lynis
Changelog v1.3.2
- As the NIST API is currently changing and we had some serious issues with our cve-search integration we decided to rewrite it by ourself. This process took us some time to get the CVE identification feature fully working again. Thanks for all your testing and feedback during this process. With the new integration EMBA is faster, more stable and the installation is not that error prone anymore.
- UEFI analysis integration was massively improved – see here
- A lot of code cleanup was done by @HoxhaEndri
- A new update check functionality by @HoxhaEndri
- Improved firmware diffing environment – see here
- Updated and new reporting templates by @413×8
- Your great feedback is now collected in our wiki
- Further public online resources are available and collected here
- New support possibilities via patreon or buymeacoffee
- More…
Install & Tutorial
Copyright (C) 2020 emba