Moonstone Sleet PuTTY attack flow | Image: Microsoft
Microsoft’s Threat Intelligence team has uncovered a newly identified North Korean cyber threat actor dubbed “Moonstone Sleet” (previously known as Storm-1789). This group is a chameleon in the cyber realm, combining established North Korean tactics with inventive methods to pursue financial gain and cyberespionage.

Moonstone Sleet’s operations are characterized by a combination of well-established methodologies and unique attack strategies. The group’s activities range from setting up fake companies and job opportunities to deploying trojanized tools and creating malicious software. Notably, Moonstone Sleet has been involved in the following activities:
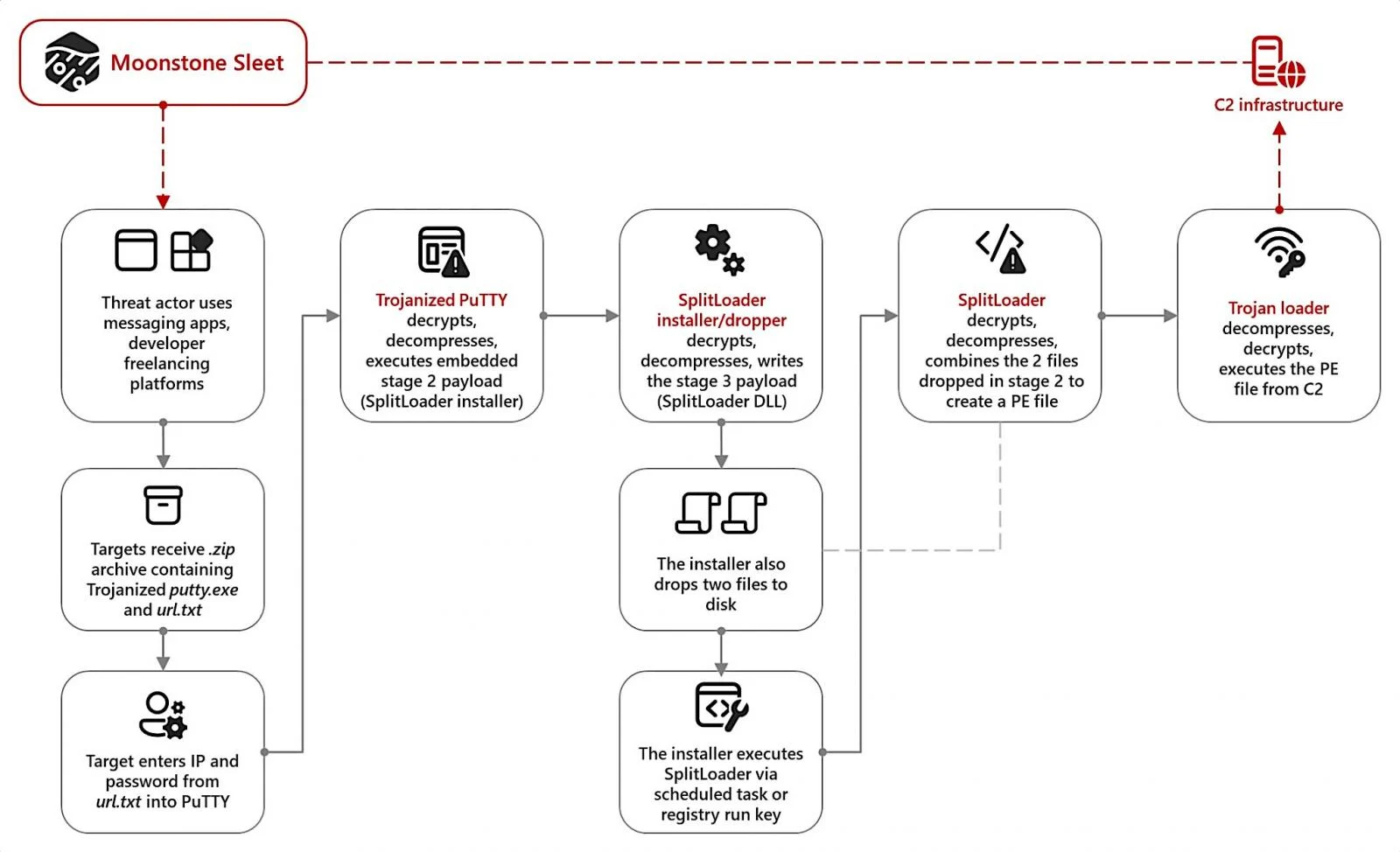
- Trojanized PuTTY Distribution:
- In August 2023, Moonstone Sleet distributed a trojanized version of PuTTY, an open-source terminal emulator, through platforms like LinkedIn, Telegram, and developer freelancing sites. The trojanized PuTTY executed a multi-stage malware deployment process, ultimately leading to the execution of a custom payload.
- Malicious npm Packages:
- The group targeted potential victims with projects containing malicious npm packages, often delivered through freelancing websites or social media platforms. These packages were designed to establish a connection to actor-controlled IPs and deploy additional malicious payloads.
- Malicious Game Deployment:
- Since February 2024, Moonstone Sleet has been using a malicious tank game called DeTankWar to infect devices. The group approached targets under the guise of a game developer seeking investment or collaboration, often using fake companies and robust public campaigns to lend legitimacy to their operations.
- Custom Ransomware – FakePenny:
- In April 2024, Moonstone Sleet deployed a new ransomware variant named FakePenny. This ransomware was used to target a company previously compromised in February, demanding a ransom of $6.6 million in Bitcoin.
Initially, Moonstone Sleet’s activities showed significant overlaps with those of Diamond Sleet, another North Korean threat actor. However, Moonstone Sleet has since developed its own infrastructure and attack methodologies, establishing itself as a distinct and well-resourced entity. This evolution includes the use of techniques and procedures shared among North Korean threat actors, such as social engineering and trojanized software, but with its unique implementations.
Moonstone Sleet has demonstrated a sophisticated approach to deception by creating fake companies and personas to lure targets. Examples include:
- StarGlow Ventures:
- From January to April 2024, Moonstone Sleet operated under the guise of StarGlow Ventures, a fake software development company. The group targeted educational and software development organizations with emails designed to establish relationships and potentially gain access to valuable information.
- C.C. Waterfall:
- Another fake company, C.C. Waterfall, was used to contact targets and distribute the malicious tank game DeTankWar. This campaign aimed to build trust and exploit relationships for malicious purposes.
Microsoft urges organizations and individuals to exercise heightened vigilance against social engineering attacks, particularly those involving unsolicited job offers or software downloads. Maintaining up-to-date security patches and utilizing robust antivirus and anti-malware solutions are essential for mitigating the risk posed by Moonstone Sleet and similar threats.