Image Credit: Cloudflare
Web service provider CloudFlare announced yesterday, through a blog post, the introduction of the ECH standard. ECH, or Encrypted Client Hello, is a newly proposed standard that has garnered the support of Google Chrome and Mozilla Firefox (experimental feature activation required, details below). Other browsers may take time to adopt this standard. However, enabling ECH on websites will not hinder user access. If a browser doesn’t support ECH, it can fall back to SNI/ESNI for continued access.
Sites hosted on CloudFlare’s free version have been defaulted to ECH and cannot be disabled. This can be found under Dashboard > Websites > SSL/TLS > Edge Certificates > Encrypted Client Greeting.
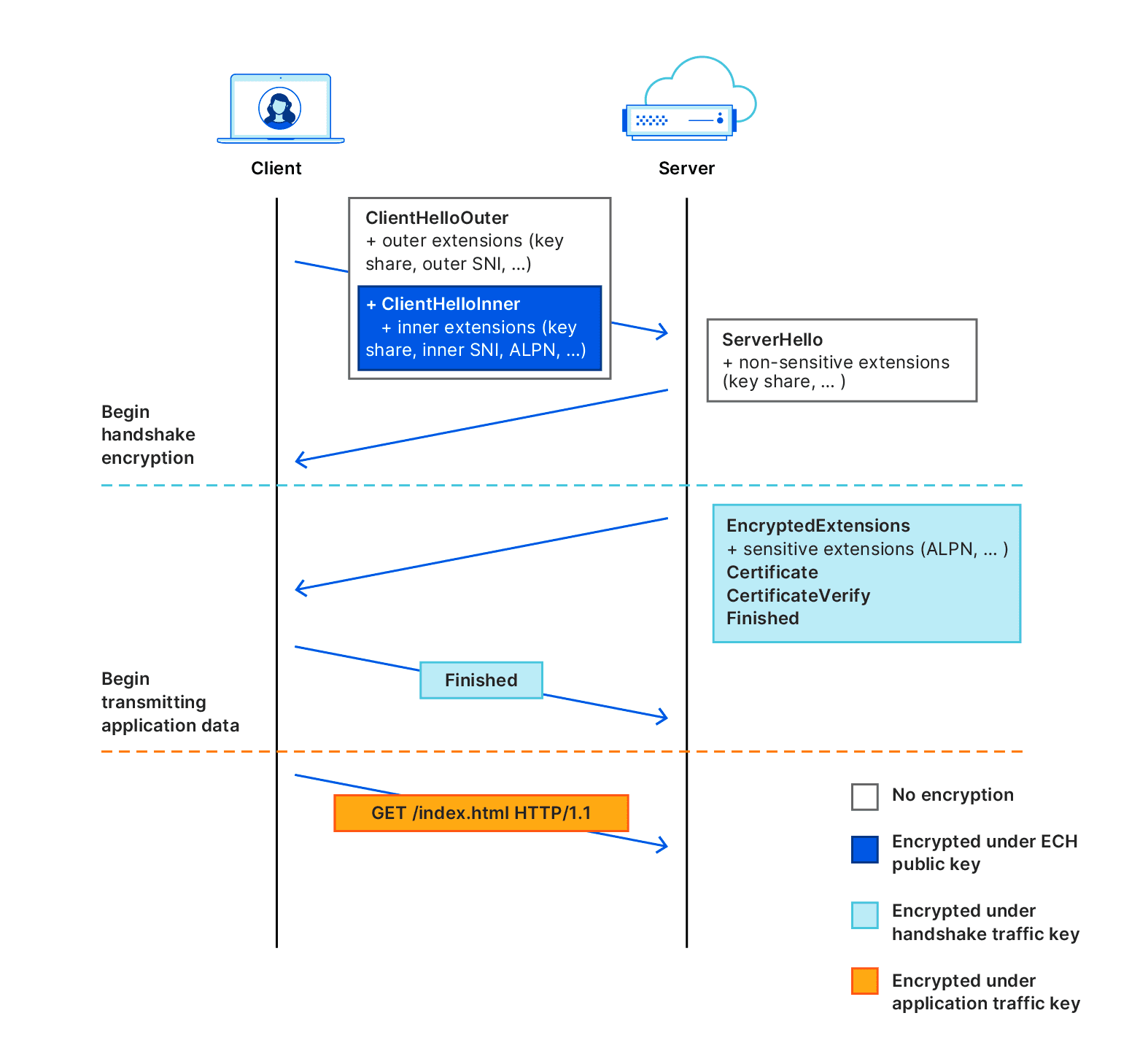
ECH, standing for Encrypted Client Hello, is the successor to ESNI. Its primary objective is to mask the Server Name Indication (SNI) used for negotiating TLS handshakes and serves as a replacement for the previous Encrypted Server Name Indication (ESNI).
During the HTTP era, network providers had numerous methods of snooping to track websites users visited, primarily because HTTP was unencrypted. This made it easy for them to hijack HTTP traffic and interject unwanted data, such as swapping downloaded apps with promotional ones or inserting traffic plans or ads into any website a user visited.
Over the past decade, there has been a swift transition from HTTP to HTTPS. With HTTPS encrypting website content, network providers can no longer arbitrarily intercept traffic. However, this doesn’t mean they can’t track which sites users visit.
When a browser accesses a specific address, the DNS request can leak the address, and the SNI reveals the domain. The industry thus introduced DNS over HTTPS/TLS to encrypt DNS query requests. However, the SNI issue remained unresolved, as SNI information could still be exposed to network providers.

ECH’s message is divided into two sections: an internal and an external segment. The external section contains non-sensitive data, such as encryption type and TLS version, while the internal segment contains the encrypted internal SNI.
On CloudFlare-hosted sites that activate ECH, the external segment uses “cloudflare-ech.com”, a shared SNI. This only allows providers to know that the user’s accessed site utilizes CloudFlare and the ECH standard, without revealing the specific website domain.
The internal segment, which houses the private SNI data, is encrypted and decrypted by CloudFlare, ensuring that the network provider remains uninformed.
Currently, ECH has been embraced by major browsers: Google Chrome and Mozilla Firefox. The support from Chromium implies that most browsers based on Chromium also back ECH, bolstering privacy and security across the internet.
Starting today, CloudFlare’s premium users can activate the ECH feature from their dashboard. In the coming weeks, this functionality will be expanded to free users, enabling all sites hosted on CloudFlare to utilize ECH.
- For Chrome, enable this experimental feature: chrome://flags/#encrypted-client-hello (Note: Chrome 117+ has it enabled by default)
- For Firefox, enable this experimental feature: about:config and turn on network.dns.echconfig.enabled
- For Safari: Support is forthcoming.