
ErrorFather Telegram bot | Image: CRIL
A recent report from Cyble Research and Intelligence Labs (CRIL) has unveiled a dangerous new campaign called ErrorFather, which utilizes a previously undetected version of the infamous Cerberus Android Banking Trojan to target Android users. The ErrorFather campaign demonstrates the persistent threat posed by Cerberus, even years after its initial discovery in 2019.
Originally gaining notoriety in 2019, Cerberus was a banking Trojan that terrorized users by stealing credentials from financial and social media apps through keylogging, overlay attacks, and VNC functionalities. Following the leak of Cerberus’ source code, it gave rise to other banking trojans, including Alien, ERMAC, and Phoenix. Now, ErrorFather is the latest in this long line of threats, leveraging the same dangerous code to launch a new wave of attacks.
As stated in the report, “The ErrorFather campaign exemplifies how cybercriminals continue to repurpose and exploit leaked malware source code, underscoring the persistent threat of Cerberus-based attacks even years after the original malware’s discovery“.
The ErrorFather campaign employs a sophisticated infection chain involving multiple stages, starting with session-based droppers and ending with an encrypted payload that deploys Cerberus. This multi-step process makes detection and removal efforts far more complex, as the malware evolves with each stage.
CRIL researchers identified the campaign in September and October 2024, noting a surge in activity during these months. “The campaign ramped up in activity in September and October 2024, with more samples and ongoing campaigns suggesting active targeting and scaling by the Threat Actors (TAs) behind the ErrorFather campaign“. With more samples and active Command & Control (C&C) servers, it is clear that ErrorFather’s operators are ramping up their efforts to target Android users worldwide.
The final payload of the ErrorFather campaign is packed with malicious features, including keylogging, overlay attacks, and VNC access, allowing attackers to monitor and control infected devices. One of the more sophisticated aspects of the malware is its use of a Domain Generation Algorithm (DGA), which helps it stay operational even if the primary C&C servers are taken down.
“The campaign highlights how repurposed malware from leaks can continue to pose significant threats years after its original appearance.” By incorporating a DGA, the attackers behind ErrorFather have built a resilient infrastructure capable of dynamically updating C&C servers, ensuring that the malware can continue to function even under pressure from cybersecurity defenders.
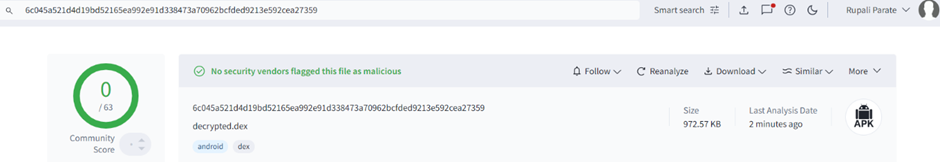
Perhaps the most troubling aspect of the ErrorFather campaign is its ability to evade detection. “When submitted to VirusTotal, the decrypted.dex file was not flagged by any antivirus engine,” the report explains. This underscores how even well-known malware strains can resurface with slight modifications to bypass modern security defenses.
One unique aspect of ErrorFather is its use of a Telegram Bot for communication, marking a departure from traditional C&C channels. Researchers noted that the malware communicates with a Telegram bot named “ErrorFather,” which further obfuscates the operation and makes detection more challenging for defenders.
The ErrorFather campaign demonstrates the evolving nature of cyber threats, especially as attackers repurpose old malware with new techniques to evade detection. “The Cerberus malware used in the ErrorFather campaign can carry out financial fraud through VNC, keylogging, and overlay attacks“, making it a serious threat to Android users and their financial data.
For users and organizations, staying vigilant and keeping devices updated with the latest security patches is crucial to minimizing the risk posed by campaigns like ErrorFather. Additionally, adopting more sophisticated detection tools that can identify obfuscated and repurposed malware strains will be key in combating these threats in the future.
For more details on the technical analysis of this campaign, visit Cyble’s full report on ErrorFather.
Related Posts:
- Urgent Security Alert for Siemens Fire Protection Systems: Critical Vulnerabilities Discovered
- Attackers Turn Digital Analytics Tools into Weapons, Experts Warn
- Massive Android SMS Stealer Campaign Uncovered: Over 100,000 Malicious Apps Targeting Global Users
- Fake Palo Alto Tool Delivers Sophisticated Malware in Middle East Cyberattack
- North Korea’s Cyber Shadow War: Unmasking RustBucket and KandyKorn