Overview of the exploit’s control flow | Image: ESET
ESET researchers have identified two severe vulnerabilities in WPS Office for Windows, widely exploited by the APT-C-60 cyberespionage group, which is aligned with South Korea. The vulnerabilities, designated CVE-2024-7262 and CVE-2024-7263, pose significant threats as they enable arbitrary code execution, potentially compromising millions of users, particularly in East Asia.
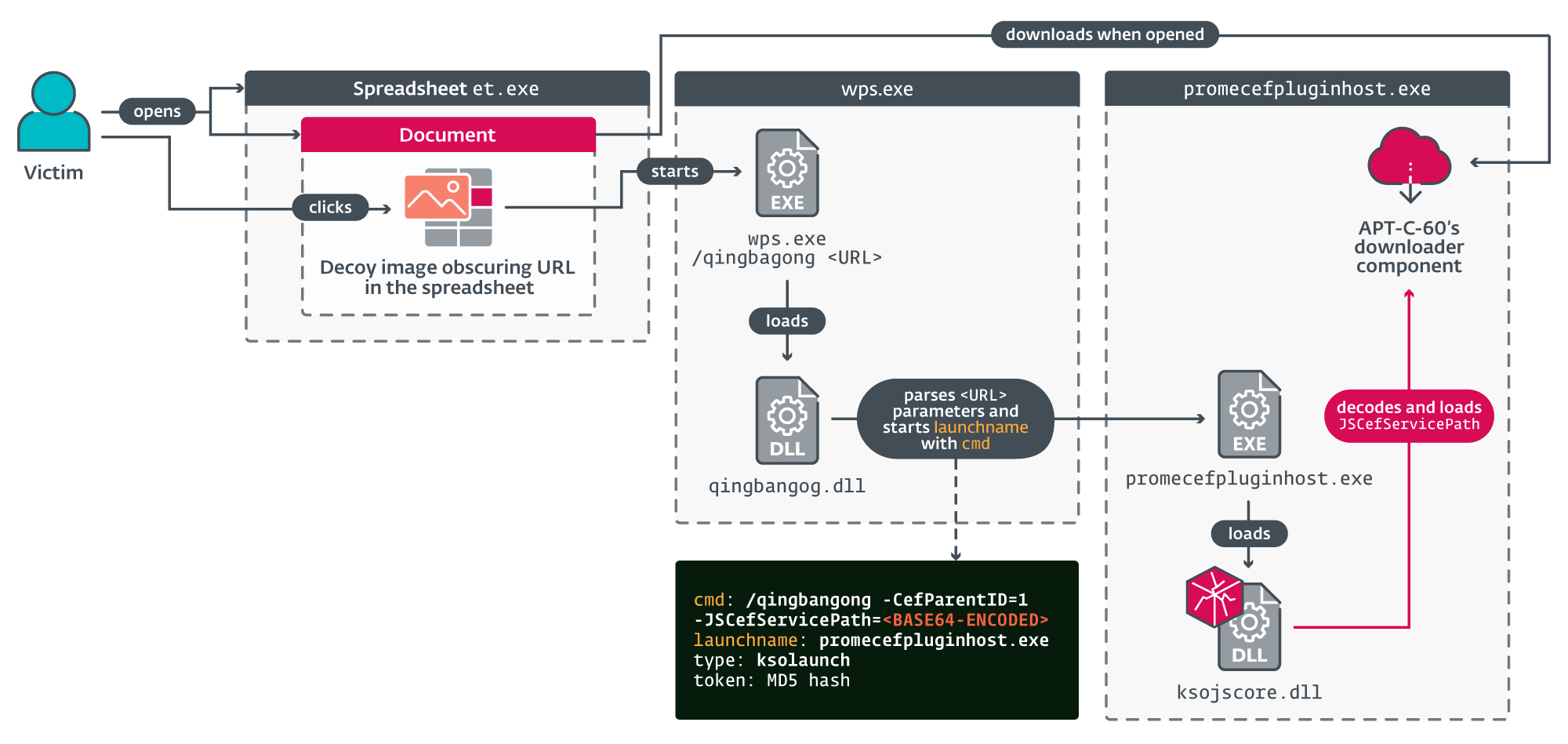
The initial discovery of CVE-2024-7262 occurred during an investigation into APT-C-60’s activities. Researchers stumbled upon a suspicious spreadsheet document linked to the group’s downloader components. Further analysis revealed that APT-C-60 had been exploiting this vulnerability in the wild, using WPS Office to deploy a custom backdoor, internally named SpyGlace, and publicly documented as TaskControler.dll.
This flaw stemmed from the improper sanitization of a file path within WPS Office’s plugin component, promecefpluginhost.exe. By leveraging this vulnerability, attackers could hijack the control flow of the software, leading to arbitrary code execution when users interacted with seemingly innocuous spreadsheet documents. The malicious documents, disguised as standard MHTML exports of Excel files, contained hidden hyperlinks capable of triggering remote code execution when clicked.
During the patch analysis for CVE-2024-7262, ESET researchers uncovered another related vulnerability, CVE-2024-7263. This flaw similarly allowed attackers to hijack the control flow of promecefpluginhost.exe by exploiting a logic bug that permitted the loading of a malicious library from a network share.
APT-C-60, known for its strategic focus on East Asian targets, exploited these vulnerabilities to infiltrate systems and deploy malware, particularly in China. The group’s use of the WPS Office suite, which has over 500 million active users globally, highlights their intent to maximize the reach of their cyberespionage efforts within the region.
Following a coordinated disclosure process, both vulnerabilities have now been patched by WPS Office. ESET strongly advises all WPS Office users to update their software to the latest version immediately to mitigate these risks.
Related Posts:
- Critical Remote Code Execution (RCE) Vulnerability Affects WPS Office
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger