ESET’s Discovery: Blackwood’s AitM Attacks and the NSPX30 Implant
In the intricate and often shadowy world of cyber espionage, a new name has risen to prominence, sending ripples through the cybersecurity community: Blackwood. This newly identified China-aligned Advanced Persistent Threat (APT) group, operating since at least 2018, has been the focus of intensive research by ESET’s dedicated team of experts. Their findings reveal the use of a sophisticated implant known as NSPX30, marking a new era in cyber threat capabilities.
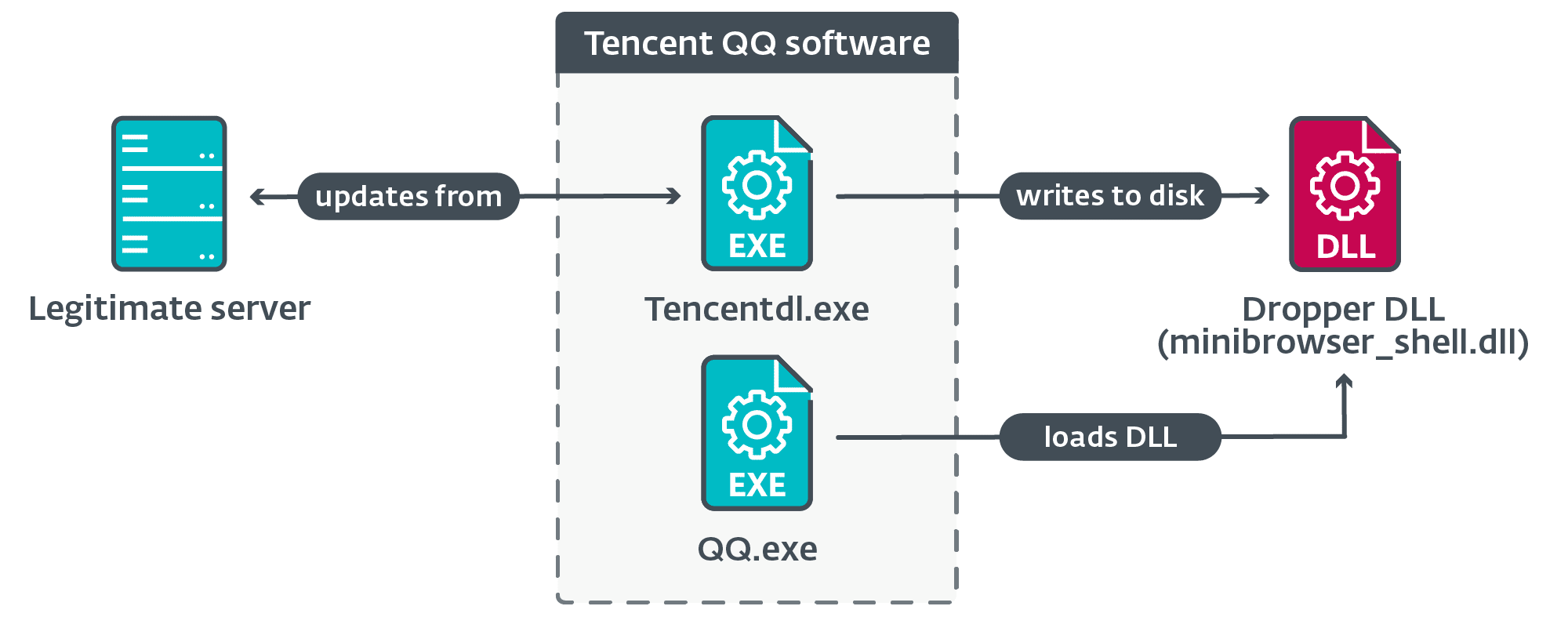
Blackwood emerges as a formidable actor in the realm of cyberespionage, targeting a diverse array of victims, including individuals and companies in China and Japan, a Chinese-speaking individual linked to a UK university’s network, and offices of a Japanese corporation in China. Their method of attack is as cunning as it is effective, employing adversary-in-the-middle (AitM) attacks to hijack update requests from legitimate software.

Illustration of the observed chain of execution | Image: ESET
NSPX30, the arsenal of Blackwood, is a testament to the group’s technical prowess. This implant is delivered through updates of legitimate software, cleverly hiding the location of its command and control servers by intercepting traffic generated by the implant. This method not only ensures the effectiveness of the attack but also significantly hampers detection and response efforts.
Tracing the roots of NSPX30 leads back to 2005, with its ancestor, a simple backdoor dubbed Project Wood. This evolution is marked by continuous development and refinement, with notable intermediate versions like DCM, which later evolved into the sophisticated NSPX30. The implant’s multifaceted architecture, from downloader shellcode to backdoor capabilities, demonstrates a disturbing trend towards more resilient and adaptable cyber threats.
Blackwood’s persistence is particularly alarming. The group has shown a relentless determination to re-compromise systems if access is lost, indicating a long-term strategic approach to their operations. NSPX30’s adaptability, coupled with Blackwood’s tenacity, poses a significant challenge to cybersecurity efforts.