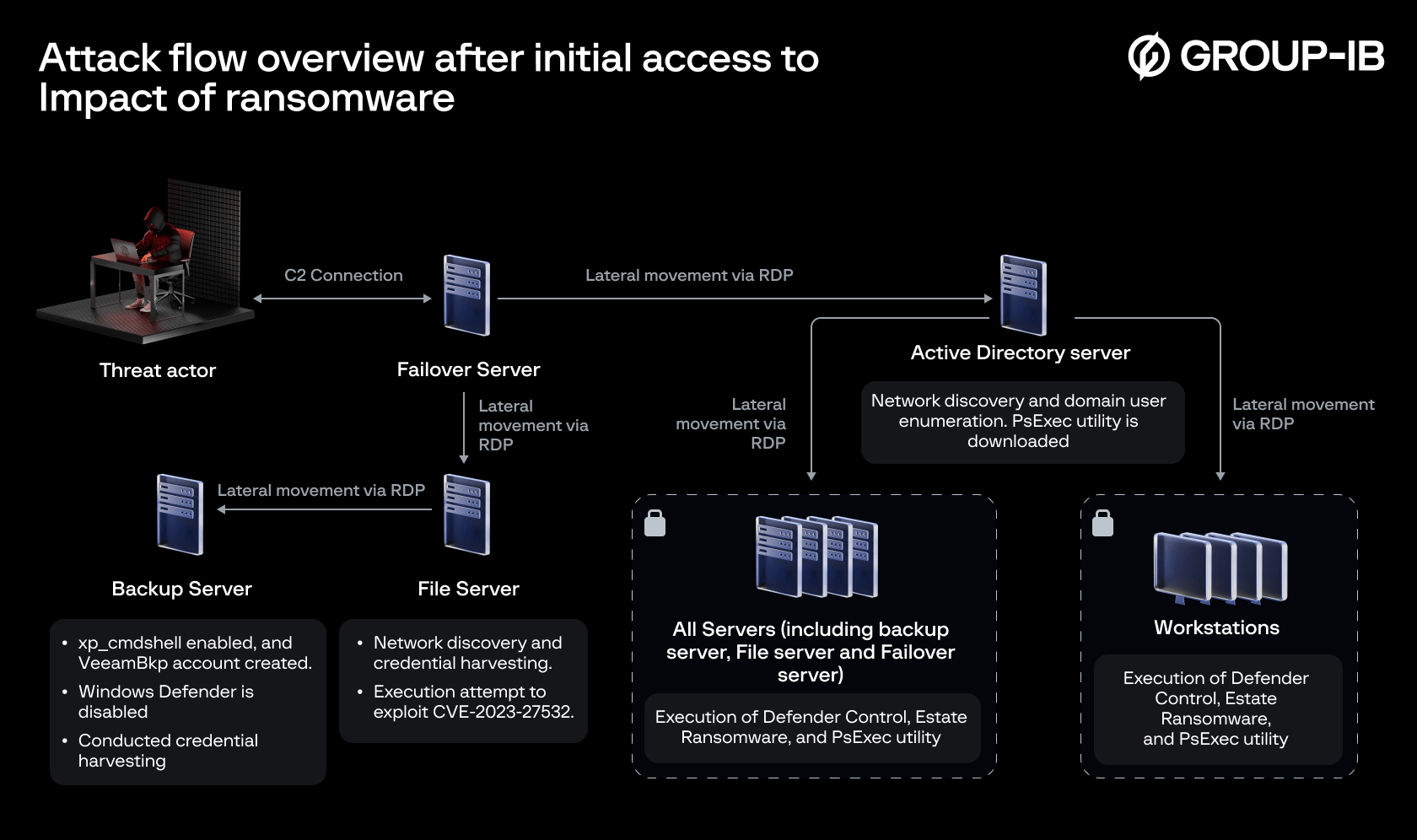
Attack flow overview after initial access to Impact of ransomware | Image: Group-IB
A recently disclosed vulnerability in Veeam Backup & Replication software has culminated in a significant ransomware incident. Yeo Zi Wei, a Junior Incident Response and Digital Forensics Analyst at Group-IB, provides a detailed examination of this breach, shedding light on the tactics employed by the emerging threat actor known as EstateRansomware.
The vulnerability in question, CVE-2023-27532, was publicly disclosed and patched by Veeam in March 2023 for versions 12/11a and later. Despite this, many systems remained unpatched, leaving them vulnerable to exploitation. Group-IB’s Digital Forensics and Incident Response (DFIR) team has recently observed a ransomware incident exploiting this very vulnerability.

The attackers gained initial access through a brute-force attack on a FortiGate SSL VPN, utilizing a dormant account. They then established a persistent backdoor, allowing them to maintain access even after their initial intrusion was discovered. This allowed them to pivot to vulnerable Veeam servers, using tools designed to exploit the CVE-2023-27532 vulnerability and harvest credentials.
Once inside, the threat actor established RDP connections from the firewall to the failover server, deploying a persistent backdoor named “svchost.exe.” This backdoor was configured to run daily via a scheduled task. By embedding a backdoor disguised as a legitimate process and using scheduled tasks, the attackers ensured continued access to the compromised network.
The attackers then pivoted from the failover server to the file server, engaging in a series of malicious activities aimed at harvesting credentials and exploiting the Veeam Backup & Replication software vulnerability. Files such as “veeam-creds-main” and “CVE-2023-27532.exe” were accessed, suggesting the attackers’ intent to exploit the vulnerability to obtain passwords from Veeam’s credential manager.
The attackers executed a sequence of steps that included deploying various tools to gather information and further exploit the network:
- Initial Exploitation: They used the “veeam-creds-main” tool, likely linked to Proof of Concept (PoC) scripts available on GitHub, to extract credentials from vulnerable versions of Veeam Backup & Replication software.
- Credential Harvesting: Using tools like SoftPerfect Netscan and Nirsoft’s password recovery tools, they harvested credentials and network information.
- Network Scanning and Lateral Movement: The attackers moved laterally to the Active Directory (AD) server, using tools like AdFind to enumerate domain users and gather additional intelligence.
With a strong foothold established, the attackers executed the final phase of their operation:
- Ransomware Deployment: Using compromised domain accounts, they deployed ransomware across the network. Tools such as DC.exe (Defender Control) and LB3.exe (EstateRansomware) were used to disable Windows Defender and execute the ransomware payload.
- Execution and Cleanup: The ransomware was deployed using PsExec, and upon execution, it created ransomware notes and cleared essential Windows event logs to hinder forensic investigation efforts.
For a detailed analysis of the attack, including the attackers’ tactics, techniques, and procedures (TTPs), please refer to Group-IB’s full report.