etl-parser
Event Trace Log file reader in pure Python
etl-parser is a pure Python 3 parser library for ETL Windows log files. ETL is the default format for ETW as well as the default format for the Kernel logger.
etl-parser has no system dependencies and will work well on both Windows and Linux.
Since this format is not documented, we merged information from the blog of Geoff Chappel and reverse engineering activities conducted by the Airbus CERT team.
What is ETL and why is it a pain to work with? Consider ETL as a container, like AVI is for video files. Reading ETL is similarly frustrating as reading an AVI file without the right codec.
etl-parser tries to solve this problem by including parsers for the following well-known log formats:
- ETW manifest base provider
- TraceLogging
- MOF for kernel log
Why an ETL Parser?
The EVTX log format is fairly well documented, with lots of libraries and tools available today. This is not true for ETL: at the time of development, there is no significant open-source project that we know of and the ETL format is not well documented.
ETL is massively used by Windows system programmers to log useful artifacts:
- C:\Windows\System32\WDI\LogFiles\BootPerfDiagLogger.etl
- C:\Windows\System32\WDI\LogFiles\ShutdownPerfDiagLogger.etl
- NetTrace.etl via netsh
- C:\Windows\System32\WDI\<GUID>\<GUID>\snapshot.etl
- etc.
A lot of new APIs such as Tracelogging or WPP are based on ETW. These APIs are used extensively by Microsoft developers for Windows. Tracelogging is addressed by etl-parser, WPP will be addressed in a future release.
Microsoft offers a lot of consumers that create ETL traces, such as xperf.exe, logman.exe, netsh.exe, etc.
We believe it is a gold mine for DFIR analysts.
Changelog v1.0.1
Install
pip install etl-parser
Use
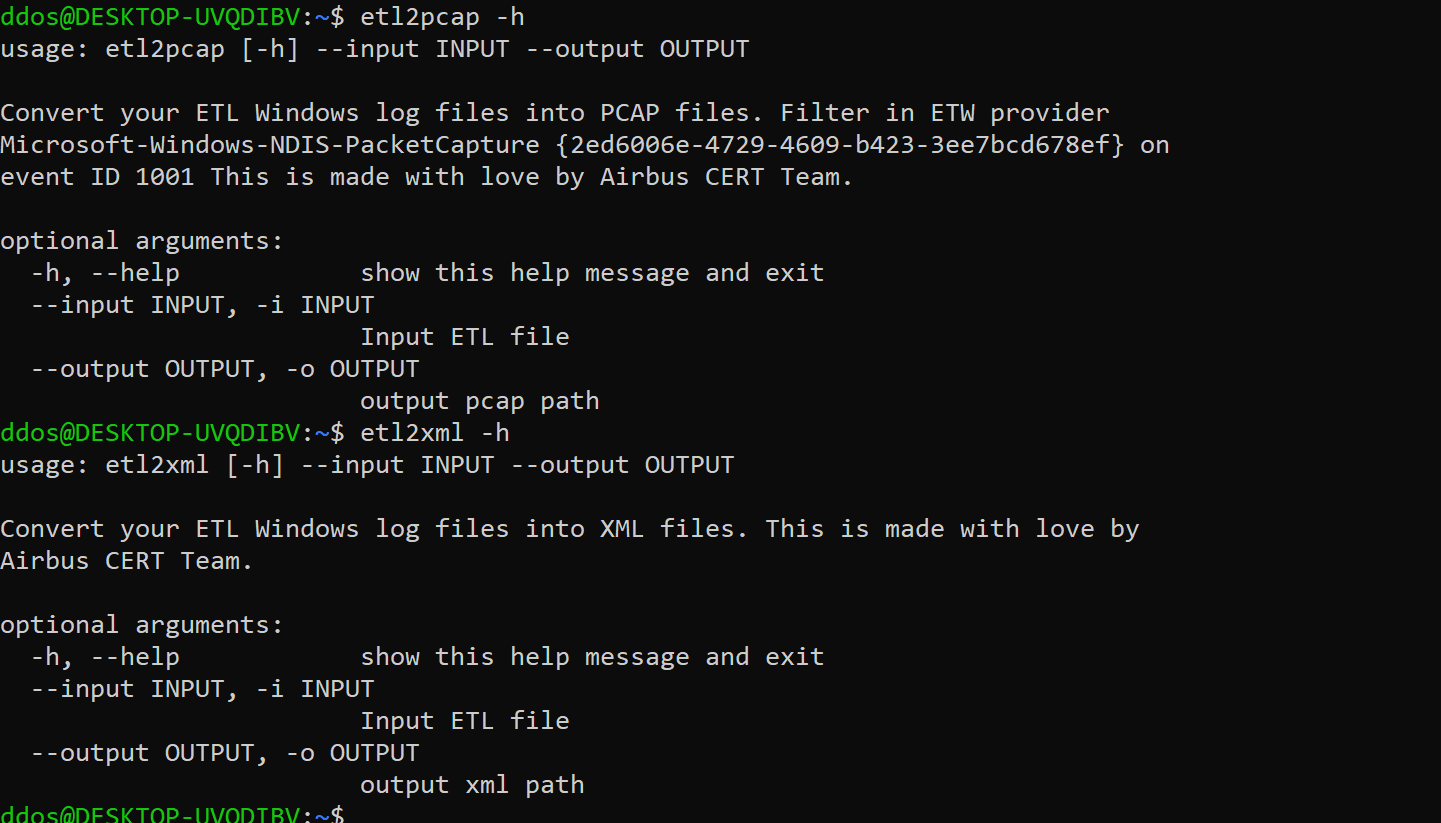
etl-parser offers two scripts. The first script, etl2xml transforms all known ETL events into XML:
etl2xml -i example.etl -o example.xml
The second script, etl2pcap transforms network captures created through netsh into the pcap file format:
netsh start trace capture=yes
netsh stop traceetl2pcap -i NetTrace.etl -o NetTrace.pcap
You can also use etl-parser as a library:
Copyright (C) 2020 airbus-cert
Source: https://github.com/airbus-cert/