Europol Leads Global Crackdown on LockBit Ransomware Syndicate
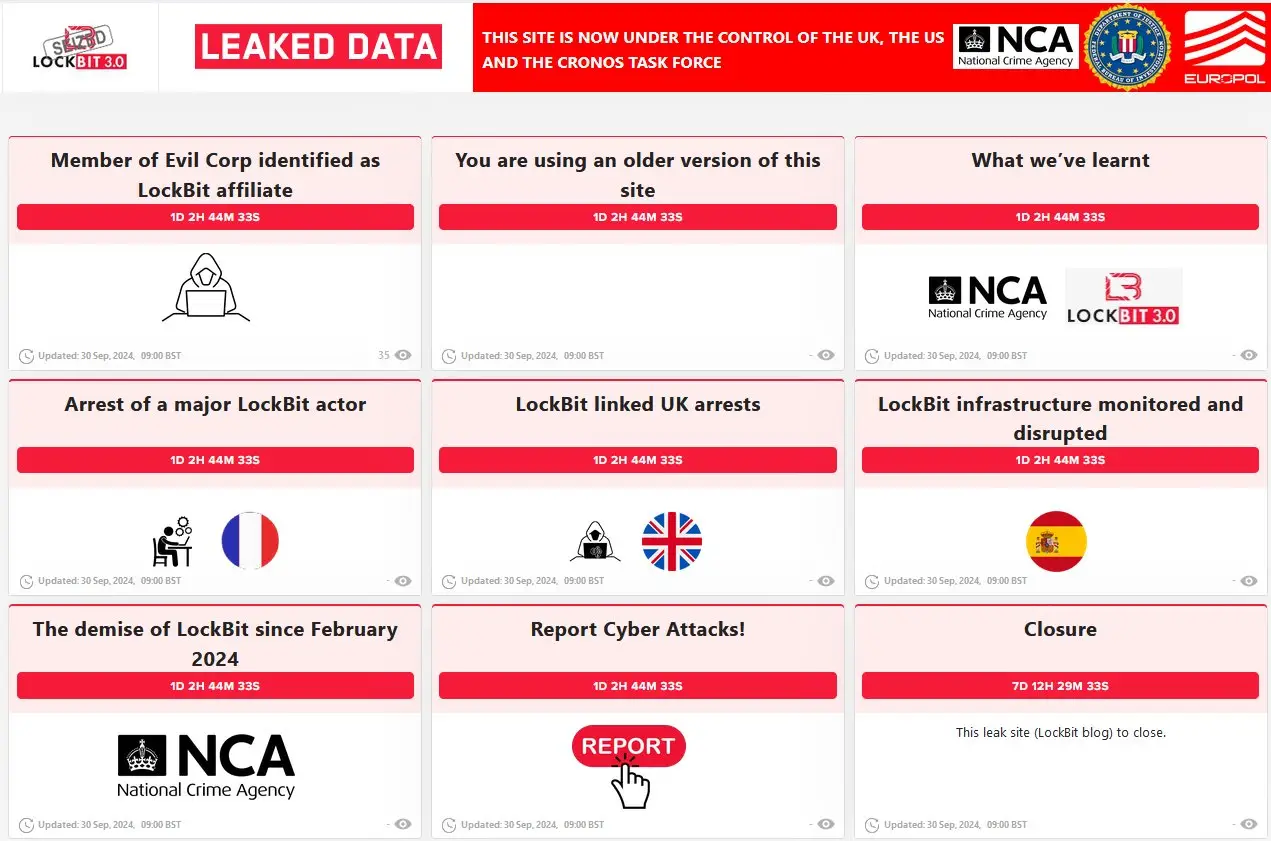
In a landmark operation against cybercrime, Europol, in collaboration with law enforcement agencies from 12 countries and Eurojust, has executed a series of coordinated actions targeting the infamous LockBit ransomware group. This extensive crackdown has led to the arrest of four key individuals and the seizure of critical servers integral to LockBit’s operations.
Arrests Span Across Europe
- France: A suspected developer associated with LockBit was apprehended at the request of French authorities, marking a significant breakthrough in dismantling the group’s core technical team.
- United Kingdom: British authorities arrested two individuals accused of supporting the activities of a LockBit affiliate. These arrests underscore the global footprint of ransomware affiliates and their networks.
- Spain: In a decisive move, Spanish officers seized nine servers forming part of LockBit’s infrastructure. Additionally, an administrator of a bulletproof hosting service used by the group was taken into custody, disrupting their secure communication channels.
Sanctions Targeting Collaborators
Further intensifying the pressure on cybercriminal networks, Australia, the United Kingdom, and the United States have implemented sanctions against an individual identified by the UK’s National Crime Agency as a prolific LockBit affiliate with strong ties to Evil Corp—a notorious Russian cybercrime syndicate. This move comes amidst LockBit’s claims denying any collaboration with Evil Corp.
- United Kingdom: Sanctioned 15 Russian nationals for their involvement in Evil Corp’s criminal activities.
- United States: Imposed sanctions on six individuals linked to these cyber operations.
- Australia: Enforced sanctions against two citizens implicated in the network.
Operation Cronos: A Multinational Effort
These actions represent the third phase of Operation Cronos, a prolonged and collaborative effort to dismantle LockBit’s criminal enterprise at every level. The operation has seen significant milestones:
- February 2024: A massive disruption of LockBit’s infrastructure hampered their ability to launch new attacks.
- May 2024 and Beyond: A series of sanctions and operational actions targeted LockBit administrators, further crippling their operations.
LockBit’s Reign of Cyber Terror
Between 2021 and 2023, LockBit became the most widely deployed ransomware variant globally. Operating on a Ransomware-as-a-Service (RaaS) model, the core group profited by selling access to affiliates and taking a cut from ransom payments. Their attacks targeted organizations of all sizes across critical sectors, including:
- Financial Services
- Food and Agriculture
- Education
- Energy
- Government and Emergency Services
- Healthcare
- Manufacturing
- Transportation
The involvement of numerous independent affiliates resulted in a diverse range of tactics, techniques, and procedures, making LockBit attacks particularly challenging to predict and prevent.
Decrypting the Threat: No More Ransom Initiative
In a bid to mitigate the damage caused by LockBit’s ransomware, Europol has supported efforts to develop decryption tools:
- Collaboration: The Japanese Police, the UK’s National Crime Agency, and the FBI pooled their technical expertise to create solutions for recovering files encrypted by LockBit ransomware.
- No More Ransom Portal: These decryption tools are freely available on the No More Ransom website, a platform offering over 120 solutions capable of decrypting more than 150 different ransomware types. Available in 37 languages, the portal has assisted over 6 million victims worldwide, highlighting the critical role of cybersecurity partnerships in combating ransomware.
Related Posts:
- Europol took down a largest DDoS-for-hire website
- A report says Iran may launch cyber attacks against sanctions
- LockBit Ransomware: The Hidden Threat in Resume Word Files
- Europol arrested hacker that used malware to steal $1.2 billion from the bank
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities





