Evolving Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters
In a recent investigation by cybersecurity researchers Avigayil Mechtinger, Shay Berkovich, and Gili Tikochinski at Wiz Research, a new variant of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters has been uncovered. This campaign exploits anonymous access to internet-facing clusters, deploying malicious container images hosted on Docker Hub to mine the cryptocurrency DERO.
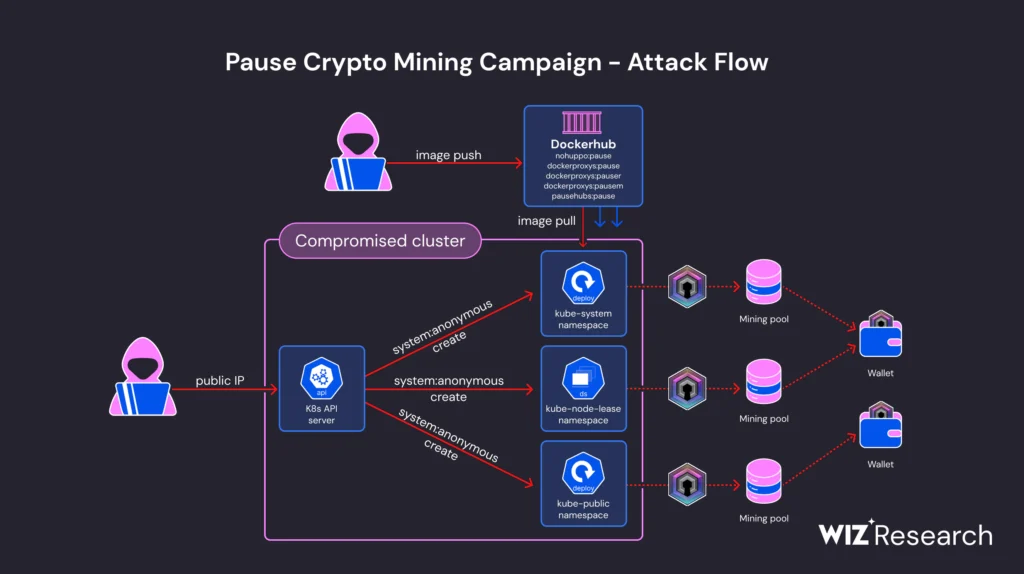
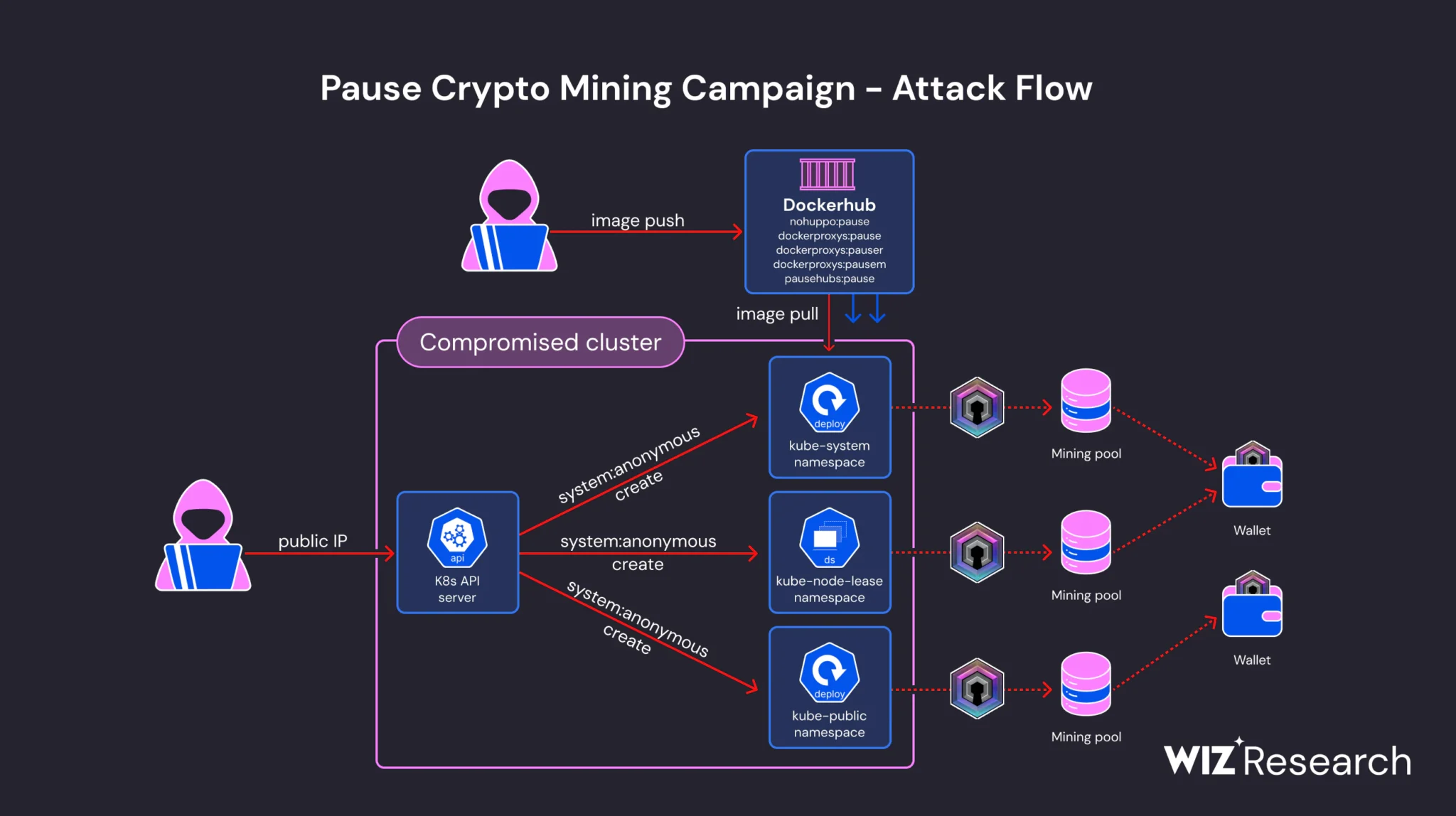
Attack flow
The attackers gained initial access through an externally accessible Kubernetes API server with anonymous authentication enabled. While this configuration typically provides minimal permissions, improper configuration of these permissions allowed the attackers to exploit the system. This misconfiguration led to the anonymous user gaining access to resources beyond their intended scope, ultimately resulting in unauthorized control over the cluster.
Once inside, the threat actor deployed various cryptominer workloads across different namespaces in the Kubernetes cluster. The malicious container images, disguised with benign-looking names such as k8s-device-plugin and pytorch-container, contained a UPX-packed DERO miner named “pause.” This miner was cleverly named to mimic the legitimate “pause” container used in Kubernetes, making it harder to detect.
The threat actor has shown significant adaptability since the campaign was first documented in March 2023. They have updated their Docker Hub repository images, indicating ongoing activity and refinement of their tactics. The miner executable had hard-coded wallet and pool information, allowing it to run without flags, which helped evade detection.
The malicious images contained the DERO miner located under /var/tmp or /usr/local/bin, with an entrypoint script that executed the miner. The use of UPX packing further obfuscated the binary, complicating detection efforts. By hardcoding encrypted wallet addresses and custom mining pool URLs into the binary, the attackers bypassed traditional detection methods that monitor for suspicious command-line arguments.
The attackers employed various methods to propagate within the target cloud environments, deploying miners across different namespaces to blend in with legitimate workloads. They used masquerading techniques to confuse manual inspections and evade automated detection systems. These included mimicking legitimate Kubernetes components and spreading their workloads across multiple namespaces to avoid raising suspicion.
To protect against such cryptojacking attacks, organizations should implement the following best practices:
- Disable External Cluster Access: Unless absolutely necessary, create private clusters without public internet exposure. This significantly reduces the attack surface.
- Disable Anonymous Cluster Access: For managed EKS and GKE clusters, ensure no additional roles are associated with
system:anonymousorsystem:unauthenticated. For unmanaged clusters, disable anonymous authentication mode if possible, or limit roles to minimal permissions. - Regular Monitoring and Auditing: Continuously monitor and audit Kubernetes cluster configurations and deployments for suspicious activity. Implement comprehensive detection solutions to identify and mitigate potential threats.
For more detailed technical analysis and defense strategies, visit the Wiz Research blog post by Avigayil Mechtinger, Shay Berkovich, and Gili Tikochinski.





