ElevenPaths researchers discovered Evrial, a malicious software that specifically steals cryptocurrencies, which controls the “easy money” on the clipboard.
In 2017, researchers found a malware called CryptoShuffle, a malware sample that reads the contents of a clipboard and modifies the cryptocurrency address. Since then, criminals have realized that it is profitable to provide these features, name it “Evrial” and start selling it outside.
Evrial, a .NET malware sample, can steal passwords from browsers, FTP clients, and Pidgin and can also modify the contents of the clipboard to allow attackers to manipulate it through the control panel. When buying this app, an attacker could set up a “name” login panel that would be hard-coded into the code to make the Evrial version available for purchase unique.
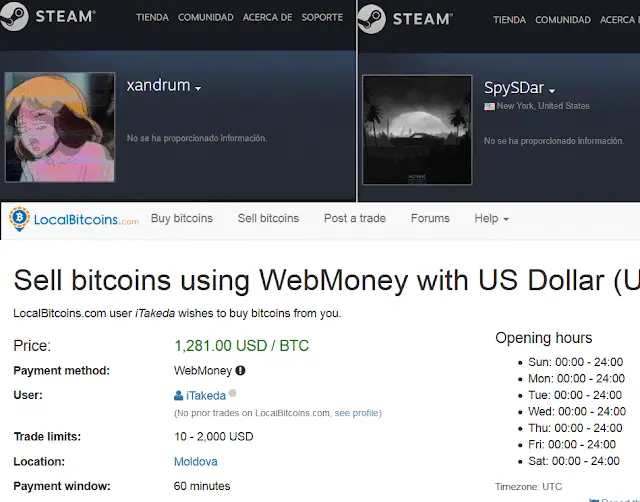
When a user makes a bitcoin transfer, the destination is usually copied and pasted. Users usually trust the clipboard’s operation, will send new transactions to the copied address, but do not know the receiving address has been attacked “sneak peek.” Malware Evrial performs address replacement tasks in the background, including Bitcoin, Ether, Monroe, Litecoin, Steam, and Webmoney WMR and WMZ.
According to MalwareHunterTeam survey, Evrial now in the Russian forum on crime can be priced at Rs1500, equivalent to about $27.
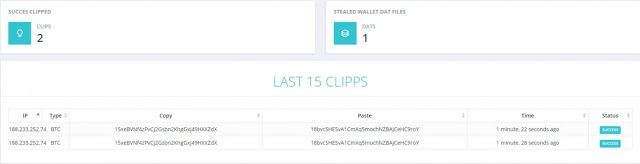
In a promotional advertisement, the seller states that after purchasing the product, the user can access a web panel and generate an executable file. The web panel also keeps track of what has changed on the clipboard, and the attacker decides what replacement string to use.
Developers at Telegram open their own username: @Qutrachka. The developer opened the social account in the source code to get in touch with those who are interested. This information and some other examples of analyzes may be identified in different dark web forums under the name “Qutra”. At the researchers’ discretion, the developer’s main goal is to sell the malware. There is also evidence that CryptoSuffer malware is related to this threat attacker.
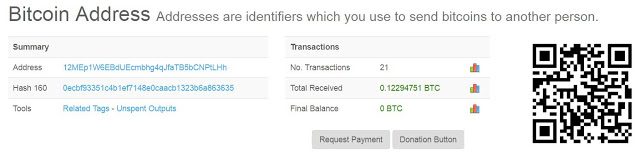
The attacker’s bitcoin wallet received 21 trades and gained nearly 0.122 bitcoins. The attacker has all the funds transferred to other addresses in an attempt to blur the transfer of traces. In addition, the attacker received 0.0131 Litecoin, which is still in his wallet.
Source & Image: elevenpaths