EXCELntDonut: XLM (Excel 4.0) macro generator
EXCELntDonut
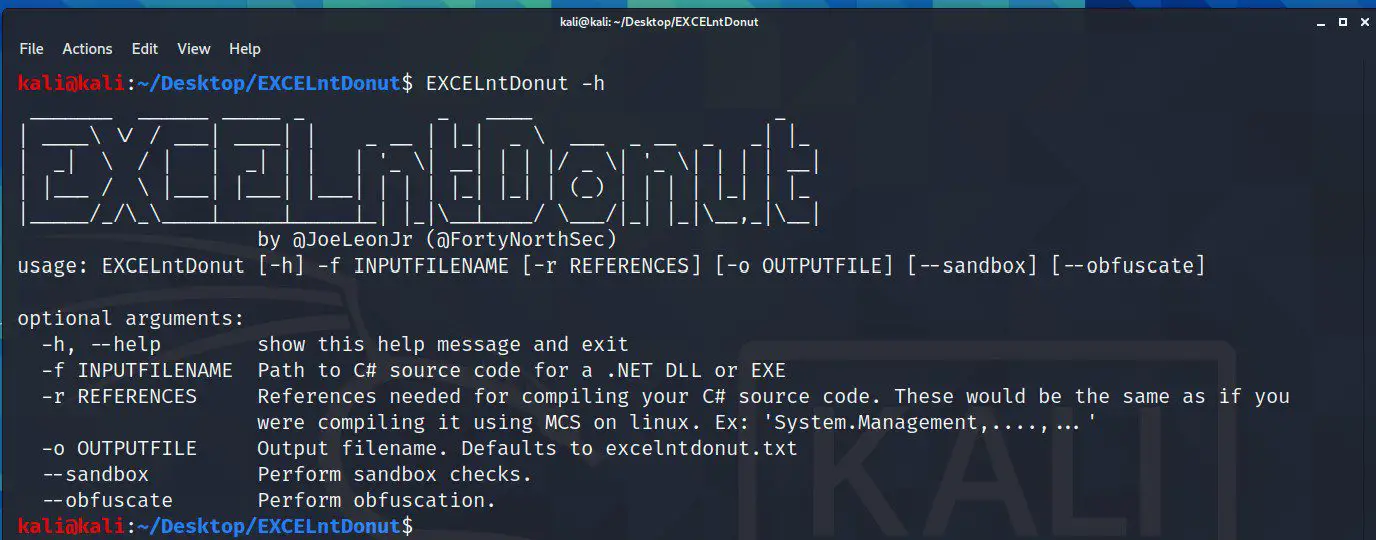
EXCELntDonut is an XLM (Excel 4.0) macro generator. Start with C# source code (EXE) and end with an XLM (Excel 4.0) macro that will execute your code in memory. XLM (Excel 4.0) macros can be saved in .XLS files.
How it works
You provide a C# file containing your payload (like an EXE with the main method that executes a cobalt strike beacon payload). That C# file is compiled using MCS into two .NET assemblies: x86 and x64. After compilation, the awesome tools Donut (for x86) and CLRvoyance (for x64) convert each assembly into position independent shellcode. Next, all null bytes are removed, since XLM (Excel 4.0) macros don’t play nicely with null bytes and the payload is chunked into lines with no more than 255 characters (for x86) or 10 characters (for x64).
Once the shellcode is prepared, it’s combined with basic process injection functions (VirtualAlloc, WriteProcessMemory, and CreateThread) as well as an architecture check function to determine which payload (x86 or x64) to run on the target system. If you elect to execute sandbox checks or basic obfuscation, then those functions will update your macro. Finally, the output is placed in a CSV file (saved as .txt).
Install
git clone https://github.com/FortyNorthSecurity/EXCELntDonut.git
chmod +x install.sh
./install.sh
Use
How to create an XLM (Excel 4.0) Macro
Once you have the output file from EXCELntDonut, open the output file in a text editor, and copy the entirety of it (Ctrl-A, Ctrl-S). Open up Excel on a Windows VM, right-click on “Sheet 1” and select “Insert”. Choose “MS Excel 4.0 Macro”. Go to cell A1 and paste the EXCELntDonut output. All the data will likely be pasted in one column. The data is a semi-colon separated “;”. Go to the “Data” tab and then click “Text-to-columns”. Select “Delimited” and on the next screen select “Semicolon” and then click “Finish”. The macro will spread across the appropriate columns and rows.
(Note – if you selected the “–obfuscate” flag, you’ll need to scroll horizontally quite a bit to find your actual code since part of the obfuscation logic moves the macro into a random section of the worksheet).
We recommend two things at this point:
- Find the starting cell (will be the top-left cell of your macro code, likely A1). Right-click and select “Run”. Test out your macro to make sure it works.
- Once you verify that the macro works, select that same top-left cell again. On the left side of the screen, there should be a dropdown that says the cell you’re in (likely “A1”). Click in the dropdown and change the text value to “Auto_open”. That will produce the same automatic execution functionality that you’re used to in VBA macros.
Save the file (.xls) and try opening it up. It should automatically execute your payload.
Sandbox Checks
These checks are based on what actual threat actors are using in their malware.
- Is there a mouse active?
- Is the screen size greater than 770 width and 381 height?
- Can the host play sounds?
- Is this a Windows machine?
Obfuscation
- For the process injection instructions (VirtuaAlloc, WriteProcessMemory, CreateThread) and sandbox checks, all macro functions will turn into the following structure:
=FORMULA(D3&D23&D54&D23&D44,E45)
The FORMULA function allows us to place a formula, which can later be executed, into another cell. So in this case, we put the process injection instructions and then use the FORMULA function to place the actual function into another cell to be executed. This avoids defenders conducting static analysis from seeing things like “VirtualAlloc”.
- The entire macro will shift some value to the right so that when you initially open up the sheet with the macros, it appears blank.
Things to know
- Less sophisticated payloads just uses the =EXEC() command to execute commands. Some also use URLMON to download files. Other files even include the word “SHELL”. All of that seemed like a bad idea to us. This tool doesn’t include any of that. Instead, it injects your C# source code into the Excel process (either 32-bit or 64-bit) and then executes. From there, it’s up to your payload on what it does next.
Tips
- Your C# source code could do anything you want it to. We recommend your source code break the Parent > Child relationship between Excel and whatever you spawn into.
- There’s a lot of good blog posts about “Very Hidden” excel sheets. Consider using that.
- Don’t forget to make your Excel file look real.
Copyright (C) 2020 FortyNorthSecurity