Execution Trace Viewer: viewing, editing and analyzing execution traces
Execution Trace Viewer
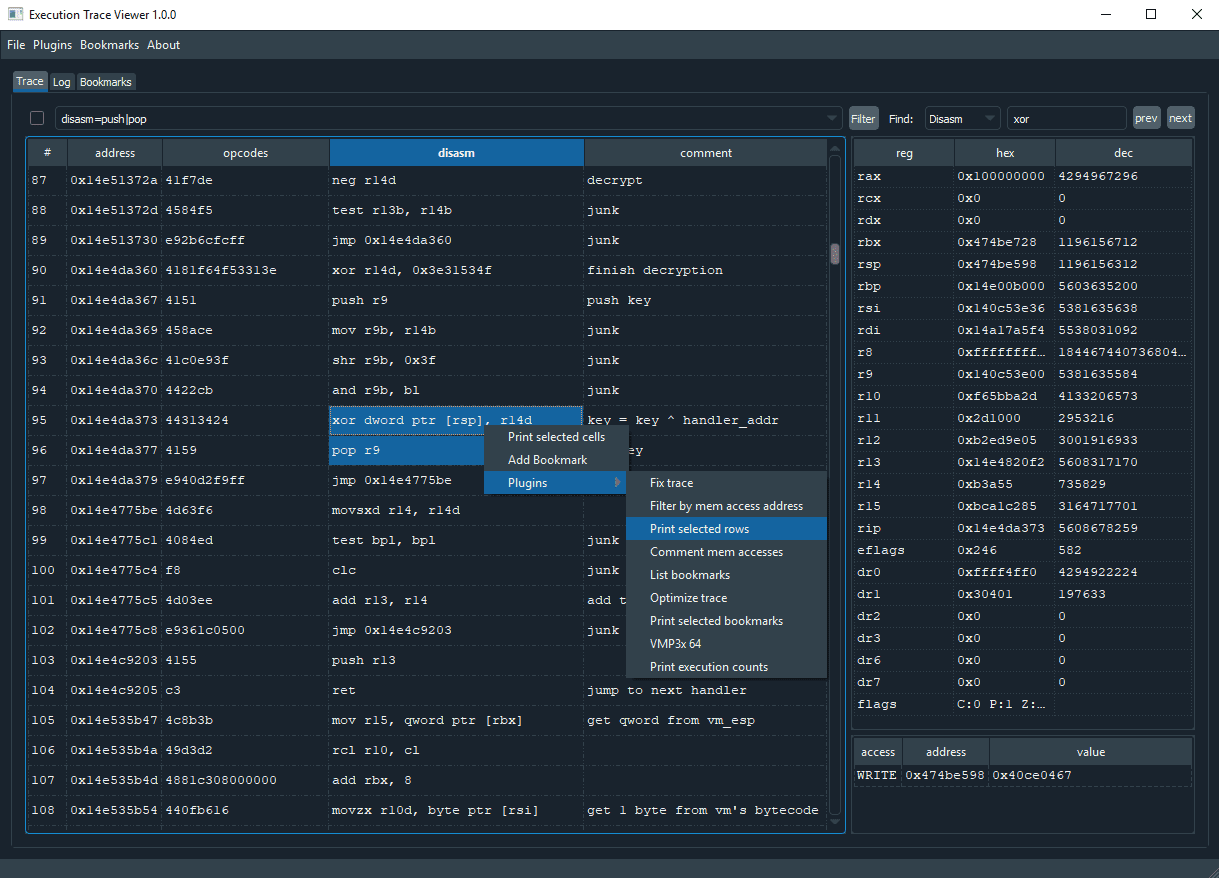
Execution Trace Viewer is an application for viewing, editing and analyzing execution traces. It was originally made for reverse engineering obfuscated code, but it can be used to analyze any kind of execution trace.
Features
- open, edit and save execution traces
- search & filter trace by disasm, reg values, memory address/value, etc
- add comments and bookmarks
- write python plugins
- supports x64dbg traces
Trace file formats
Following file formats are supported:
- .tvt – Default file format. Developed from x64dbg trace format. 3 differences with the x64dbg format: comments, disasm and bookmarks added.
- .trace32 / .trace64 – x64dbg file format. Only reading supported. Loading x64dbg traces is slow because the code needs to be disassembled.
- json – Traces can be saved and loaded from json text files.
Traces folder contains one sample trace. It is ~11k lines of obfuscated code (by VMProtect3). All the handlers are disassembled and added to bookmarks.
Plugins
Execution Trace Viewer can be extended by Python3 plugins. Plugins are launched from the plugins menu or from the right-click menu on the trace table.
Check the example plugins and core/api.py for more info.
Install
git clone https://github.com/teemu-l/execution-trace-viewer.git
pip install pyqt5 yapsy qdarkstyle capstone
Use
Copyright (c) 2019 Teemu Laurila





