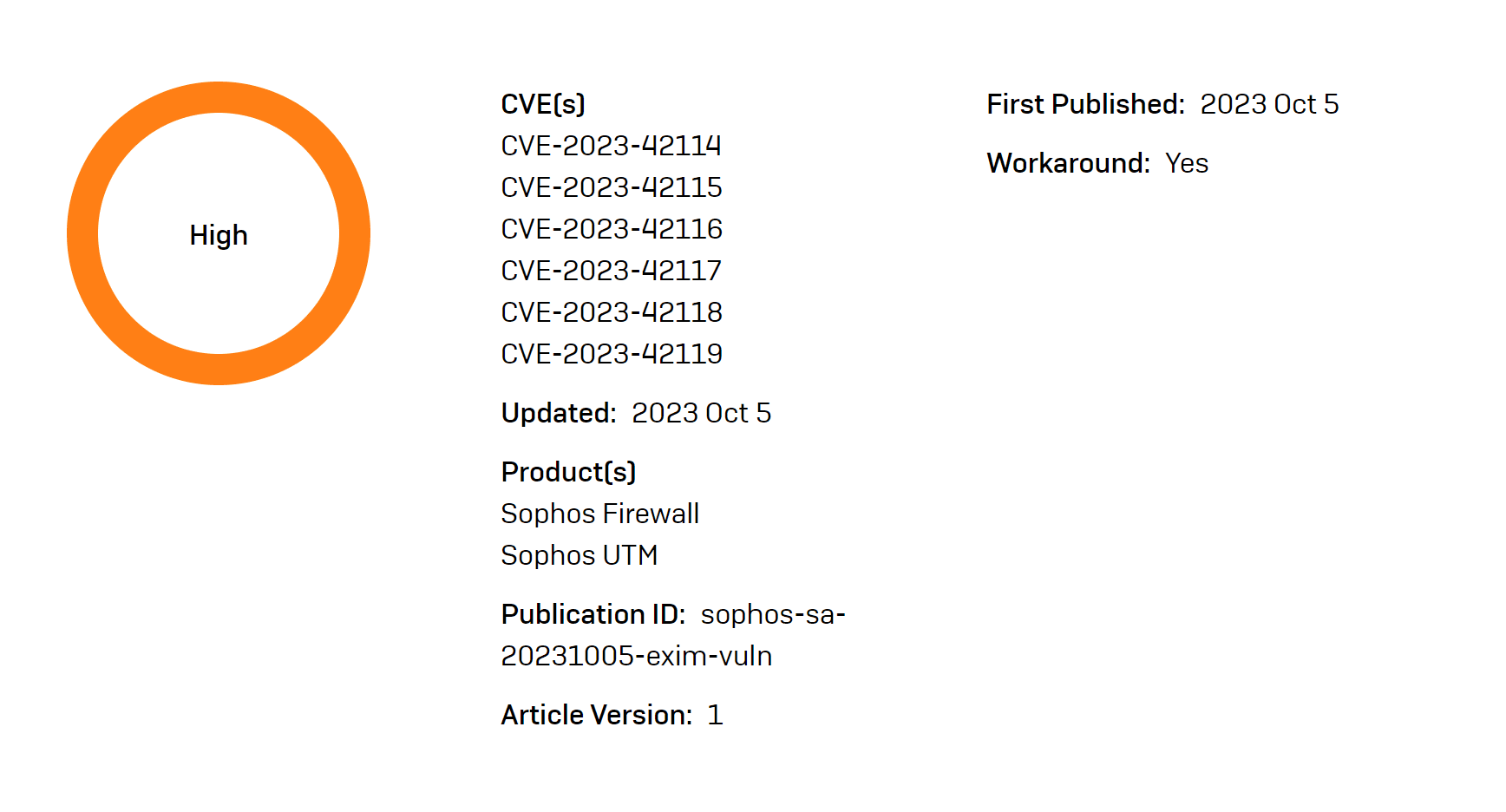
A critical vulnerability has been discovered in the Exim mailer software, which is widely used in Sophos Firewall and SG UTM products. The vulnerability tracked as CVE-2023-42118, could allow a remote attacker to execute arbitrary code on the system, which could in turn lead to a complete compromise of the device.
The vulnerability is caused by a flaw in the parsing of Sender Policy Framework (SPF) macros. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code on the system.
Sophos Firewall and SG UTM customers who are using email protection in MTA mode with SPF enabled are vulnerable to this attack. Customers who are not using email protection, or who are using legacy mode (transparent email proxy) for email, are not vulnerable.

On October 4, 2023, Sophos released a hotfix for Sophos Firewall to remediate CVE-2023-42118. The hotfix is available for the following versions:
- v20 EAP1
- v19.5 GA/MR1/MR2/MR3
- 19.0 GA/MR1/MR2/MR3
- 18.5 MR4/MR5
If you’re using SG UTM, circle October 17, 2023, on your calendar, as an update is poised for release then.
In the meantime, Sophos recommends that customers disable SPF on Sophos Firewall and SG UTM until the hotfix or patch is applied. To disable SPF on Sophos Firewall, follow these steps:
- Commence an SSH session with Sophos Firewall and navigate to options “5” and “3” to access the “Advanced Console”.
- Shift to the /log directory using the command: cd /log.
- Check for the HF filename in u2d.log by keying in: grep “sfsysupdate_NC-125369” u2d.log.
As we await updates and patches, there’s a temporary solution: disabling the SPF. This is a stop-gap measure until the hotfix or patch finds its way to your device, after which, SPF functionalities can be restored.
Here’s how:
For Sophos Firewall:
- Navigate to: “Email >> Policies & exceptions >> [edit policy] >> Spam protection >> Reject based on SPF” and deactivate SPF.
For SG UTM:
- Go to: “Email Protection >> SMTP >> Antispam >> Perform SPF check” and disable SPF check.
- In profiles mode, head to: “Email Protection >> SMTP Profiles >> [edit profile] >> BATV/RDNS/HELO/SPF/Greylisting >> Perform SPF check” and disable.