Security researcher Mohamed Shahat has disclosed three critical vulnerabilities affecting GatesAir Maxiva UAXT and VAXT transmitters. These widely deployed transmitters are used in various industries, including broadcasting, transportation, and public safety. The vulnerabilities, if exploited, could have severe consequences, ranging from session hijacking and data breaches to full system compromise.
The vulnerabilities are:
- CVE-2025-22960 (Session Hijacking): This vulnerability allows unauthenticated attackers to access exposed log files, potentially revealing sensitive session-related information such as session IDs and authentication tokens. Attackers could exploit this flaw to hijack active sessions, gain unauthorized access, and escalate privileges on affected devices.
- CVE-2025-22961 (Data Breach): An attacker can directly access sensitive database backup files (snapshot_users.db) via publicly exposed URLs. This vulnerability could lead to the retrieval of sensitive user data, including login credentials, potentially leading to full system compromise.
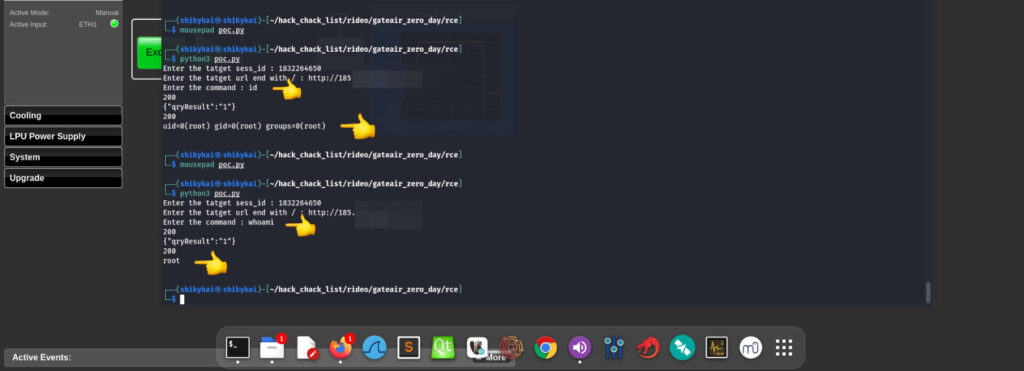
- CVE-2025-22962 (Remote Code Execution): When debugging mode is enabled, an attacker with a valid session ID can send specially crafted POST requests to execute arbitrary commands on the underlying system. This critical vulnerability can lead to full system compromise, including unauthorized access, privilege escalation, and potentially full device takeover.
Proof-of-Concept Exploit Published:
Adding to the severity of these vulnerabilities, Shahat has published proof-of-concept exploit code, making it easier for malicious actors to exploit these flaws. This underscores the urgent need for immediate action to mitigate the risk.
Mitigation:
GatesAir has yet to release patches for these vulnerabilities. In the meantime, organizations using affected transmitters are advised to take the following defensive measures:
- Restrict access to sensitive log files and directories.
- Apply strict file permissions on log and backup files.
- Avoid logging sensitive session-related data.
- Encrypt sensitive data before storage.
- Disable debugging mode in production environments.
- Implement stronger authentication and session management.
- Conduct regular security audits of the system and its file handling processes.
Organizations using GatesAir Maxiva UAXT and VAXT transmitters are strongly encouraged to take immediate action to protect their critical infrastructure from potential attacks.