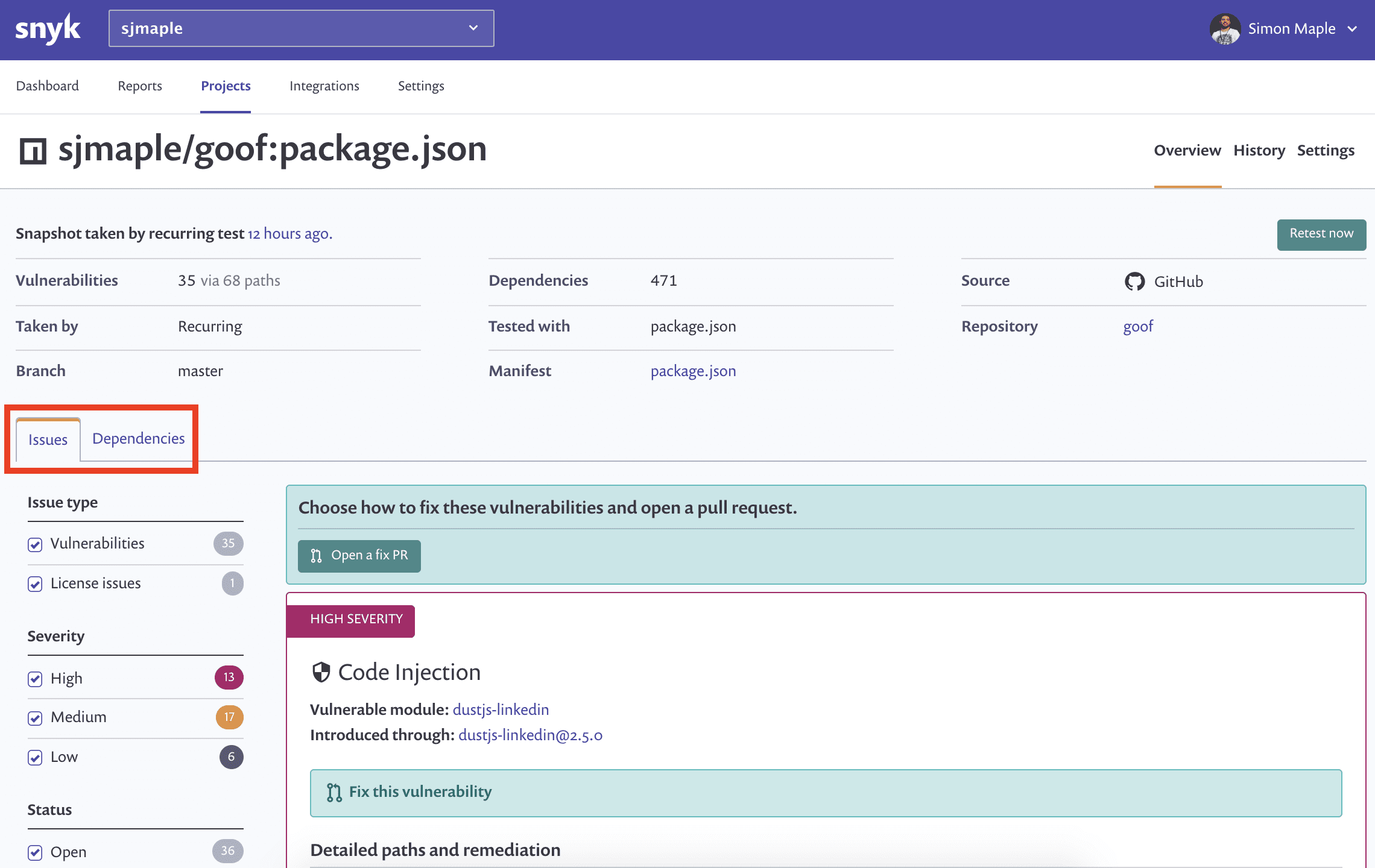
exploit-workshop
In this step by step workshop, you’ll learn how to exploit various real-world vulnerabilities existing in vulnerable versions of packages in a Node.js and Java application.
An introduction to this workshop
This workshop will lead you through installing and exploiting a number of intentionally vulnerable applications. The applications will use real-world packages with know vulnerabilities, including:
- Directory traversal
- Regular expression denial of service (ReDoS)
- Cross-site scripting (XSS)
- Remote code execution (RCE)
- Arbitrary file overwrite (Zip Slip)
These exploits exist in a number of applications, most of which you will need to install either locally or on a cloud instance. The instructions below will walk you through the local installations, but you are more than welcome to try them out on remote cloud instances also.
For each vulnerability section in this workshop, you’ll be given information about the vulnerability as well as the package it exists in. You are encouraged to attempt to hack the application by trial and error without reading any hints at first. Try to think about how you can trick the application sanitization and get into the mind of a hacker. The hints are there for when you get stuck so read them in order as and when you need a helping hand. If you can complete the hack without hints, that’s great! However, it can be good to read the hints afterward to make sure you broke in the same way we did! Plus there could be little tips in there to learn from also.