How Threat Actors Abuse URL Rewriting | Image: Perception Point
Perception Point security researchers have recently uncovered a disturbing trend in phishing attacks: the exploitation of URL rewriting features, a mechanism designed to protect users, is now being weaponized by cybercriminals. This tactic has led to a surge in sophisticated phishing campaigns that bypass traditional email security measures by hiding malicious links behind trusted domains of well-known security vendors.
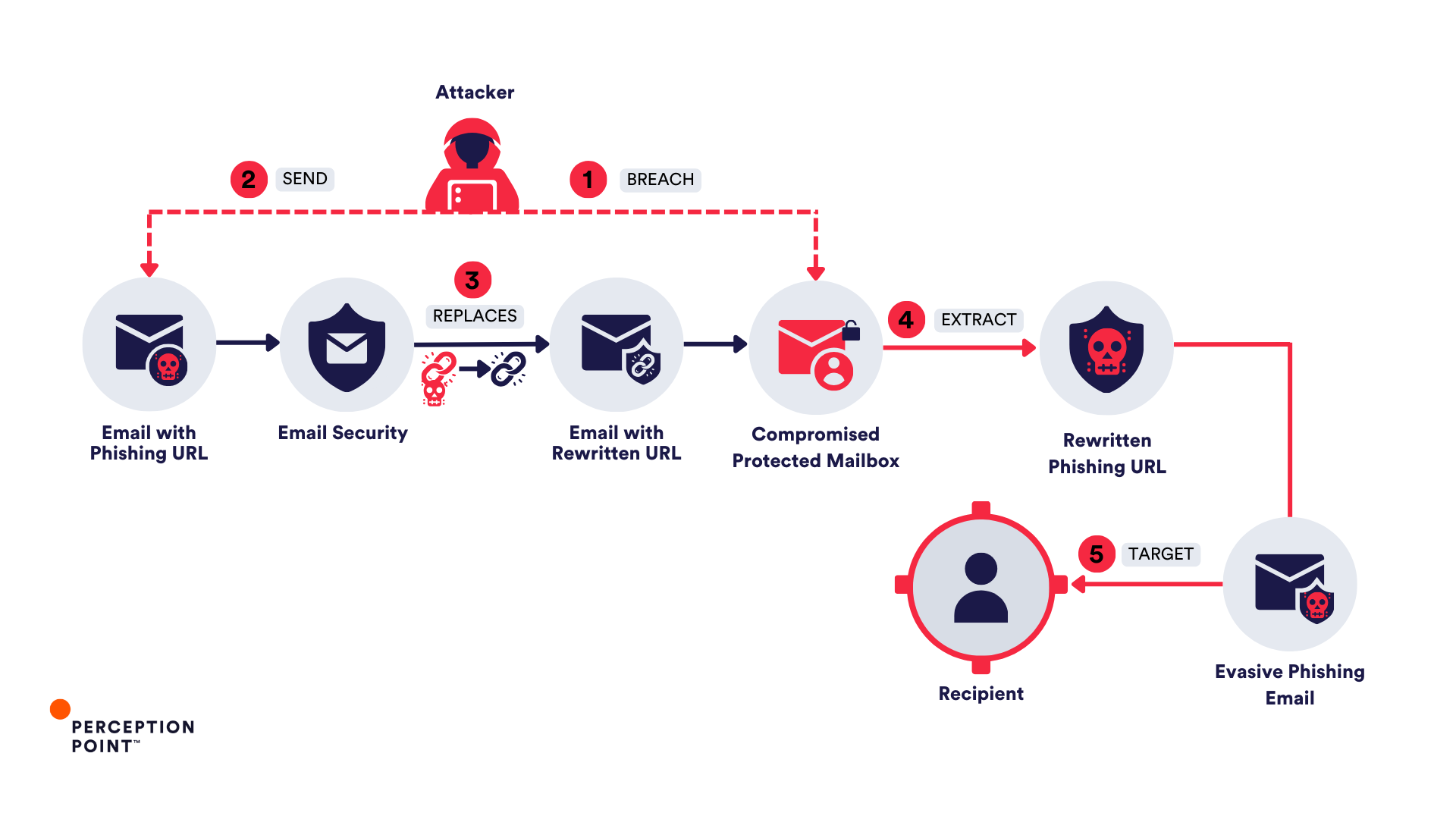
URL rewriting is a security feature used by many email security vendors, often referred to as “URL protection” or “click-time-protection.” The feature works by replacing original URLs in emails with modified links that direct users first to the vendor’s servers, where the link is scanned for threats. If the link is deemed safe, the user is redirected to the intended web content. This mechanism is crucial for protecting users from malicious links embedded in emails.
However, since mid-June 2024, threat actors have begun to abuse this feature by manipulating these rewritten URLs. The attackers craft phishing emails containing links that initially pass through the URL rewriting process, gaining the appearance of legitimacy by bearing the domain of the security vendor. Once the email has been delivered and the link rewritten, the attackers then modify the URL to redirect users to phishing sites. This technique allows the malicious link to evade further security checks, exploiting the trust that users place in familiar security brands.
Over the past few months, Perception Point researchers have observed a dramatic increase in phishing attacks that leverage this abuse of URL rewriting. These well-crafted campaigns have already targeted hundreds of organizations worldwide, potentially impacting many more.
One of the most concerning aspects of this trend is the way attackers are turning email security tools against themselves. By manipulating the URL rewriting feature, attackers can bypass even the most advanced security solutions, including those that use machine learning and real-time threat detection.
Perception Point’s advanced email security detection capabilities have intercepted several sophisticated phishing attempts that exploited URL rewriting. Here are a few notable examples:
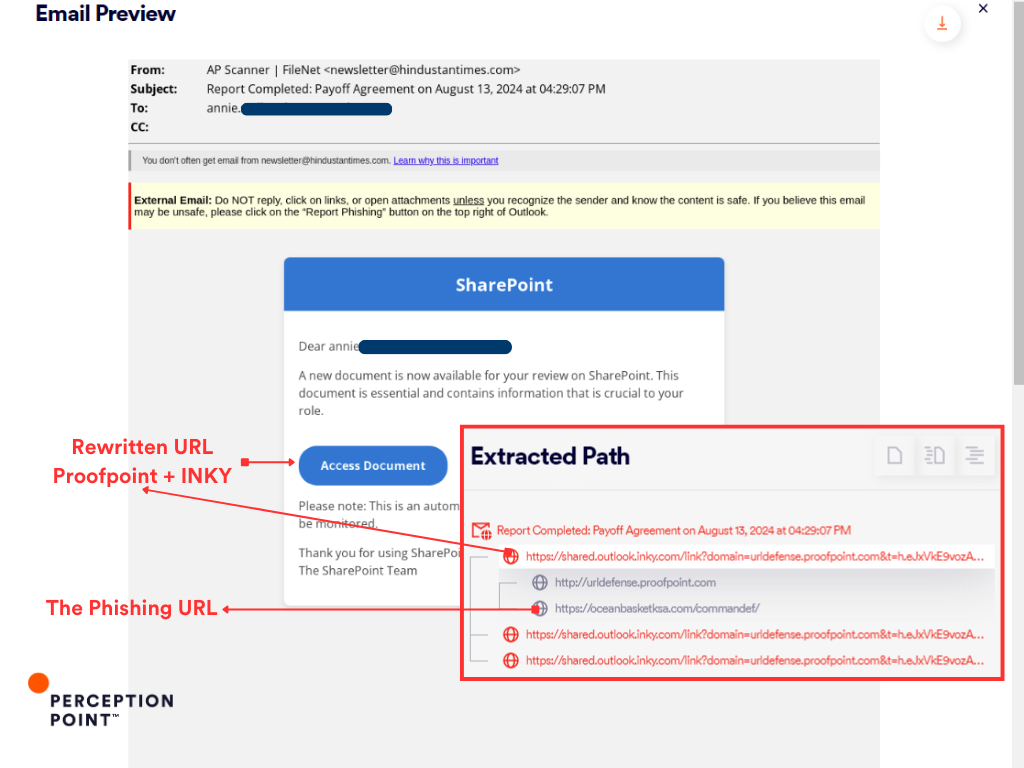
- Double Rewrite Attack: In one attack, the threat actors exploited both Proofpoint and INKY’s URL rewriting services. The attackers sent a phishing email disguised as a legitimate SharePoint document notification. The URL was first rewritten by Proofpoint’s system and then underwent a second rewriting by INKY, embedding its own protection link within the first rewrite. The attackers then used a CAPTCHA challenge to evade detection before redirecting the user to a fake Microsoft 365 login page designed to steal credentials.
- Multi-Target Exploitation: In another case, the attackers compromised an organization protected by INKY and Proofpoint. They generated a rewritten URL using the compromised account and then repurposed this link to target multiple other organizations. This approach allowed the attackers to extend their reach, turning a single point of compromise into a widespread phishing campaign.
- Mimecast and Sophos Exploitation: In separate incidents, phishing attacks exploited the URL rewriting services of Mimecast and Sophos. The attackers sent emails with rewritten URLs that appeared safe due to the presence of Mimecast and Sophos domains. However, clicking on these links redirected users to phishing sites designed to steal credentials or personal information.
The manipulation of URL rewriting is particularly dangerous because it takes advantage of the trust that users place in security brands. Even highly aware employees are more likely to click on a link that appears to come from a trusted domain. Additionally, the gap between the time a URL is rewritten and when it is weaponized creates an opportunity for attackers to bypass traditional security tools that rely on initial scans.