Following the assault by Hamas on Israel, cyber warfare ensued among the factions and their allies. Hacktivist factions have targeted SCADA and ICS systems in both Israel and Palestine, with other vulnerable systems in their crosshairs.
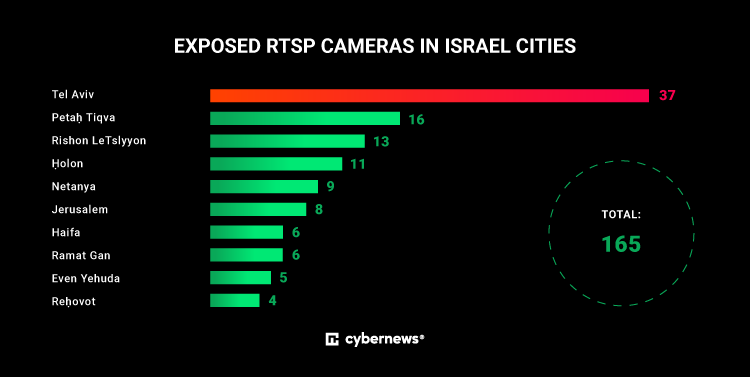
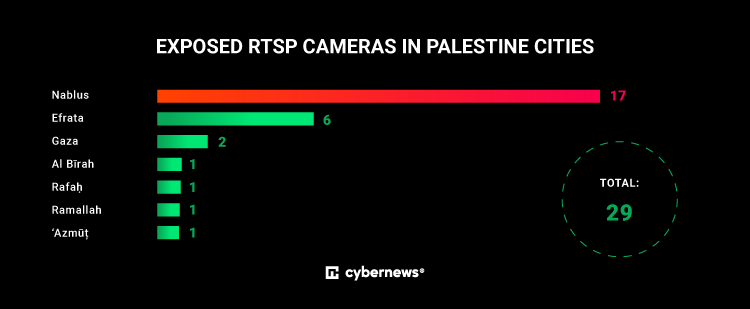
Researchers from Cybernews have identified at least 165 exposed networked RTSP cameras in Israel and 29 in Palestine, accessible to anyone. This potentially places many more individuals at risk.
RTSP stands for Real-Time Streaming Protocol. Though invaluable for transmitting live data, it neither offers encryption nor mechanisms to thwart password brute-forcing.
Malefactors, equipped with rudimentary skills, can locate these cameras and bruteforce their login credentials, given the ubiquity of known software tools and foundational tutorials. Scholars caution that these exposed RTSP cameras could pose myriad threats and dangers in the context of cyber warfare.
Tel Aviv has a minimum of 37 exposed RTSP cameras, Potah Tiqva has 16, and Rishon LeTslyyon has 13.

In Palestine, the preponderance of these exposed cameras is situated in the West Bank, possibly correlated with Israel’s power blockade in the Gaza Strip.
Militants might surveil and exploit these vulnerable cameras. The paramount risk of these exposed IP cameras is unauthorized access by hackers, granting them the capability to view live footage and record, potentially harnessing the content for surveillance, reconnaissance, or sensitive information gathering.
“The paramount importance of protecting critical infrastructure from potential threats posed by various actors cannot be overstated. These systems, if left vulnerable, could become the target of nefarious individuals or groups seeking to cause widespread disruption or harm. The consequences of such a breach could be catastrophic, with the potential for significant disruption to power grids, interference with chemical processes, or even the endangerment of public safety through the sabotage of transportation systems,” researchers opine.
While individuals are at risk, cyber adversaries are primarily intrigued by organizational or governmental infrastructures. Access to their RTSP cameras could provide attackers a foothold to infiltrate the interconnected network. Once entrenched, they could traverse laterally to compromise other systems or exfiltrate data.
Moreover, akin to other smart devices, exposed cameras might be commandeered by cybercriminals to construct botnets for Distributed Denial of Service (DDoS) onslaughts or other malicious endeavors.
Consequently, proprietors of these exposed devices bear not only the onus of their security but also the responsibility of safeguarding the community.
Securing cameras requires encrypted protocols and robust credentials. Isolation, encryption, and trustworthy credentials are Cybernews researchers’ recommended stratagems for safeguarding RTSP cameras.
- Ideally, all security or other IP cameras should be tethered to a distinct protected subnet boasting end-to-end encryption or WPA2 (Wi-Fi Protected Access 2) if the network is wireless.
- Employ encryption mechanisms to shield communication between cameras and viewing clients. Virtual Private Networks (VPNs) for remote access are preferable.
- Ascertain that RTSP cameras necessitate reliable and unique passwords for access. Utilizing default or feeble passwords is a prevalent oversight leading to unsanctioned access.
- Maintain up-to-date camera firmware to rectify security vulnerabilities and enhance overall system protection.
- Institute access controls to delimit who can view camera feeds, potentially employing IP whitelisting or VPNs for remote access.
- Consider pivoting to protocols offering encryption, such as HTTPS.