Image: Netskope Threat Labs
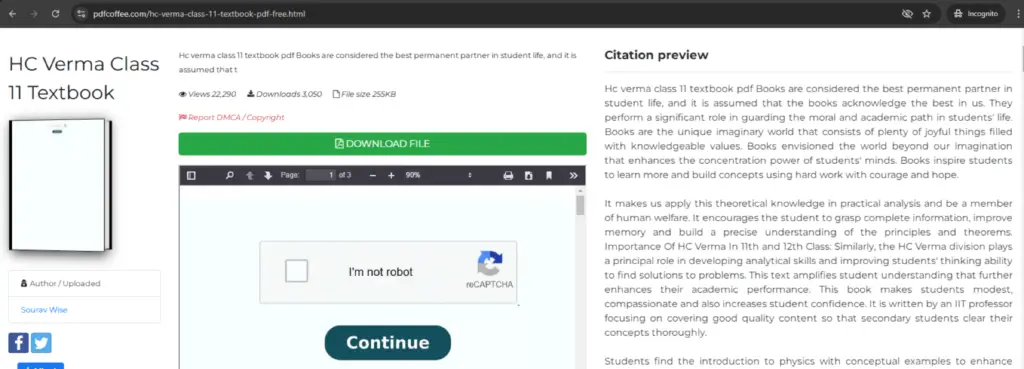
Netskope Threat Labs has uncovered a widespread phishing campaign that uses fake CAPTCHA images embedded in PDF documents to steal credit card information and distribute malware. The campaign has affected over 1,150 organizations and 7,000 users since the second half of 2024.
The attackers use search engine optimization (SEO) techniques to lure victims to malicious websites hosting the phishing PDFs. These PDFs often masquerade as user guides, manuals, templates, and forms, using keywords like “pdf,” “free,” “download,” and “printable.” When a victim opens the PDF, they are presented with a fake CAPTCHA image and instructed to copy and paste a command into a run window. This command executes a malicious PowerShell script that downloads and installs the Lumma Stealer malware.
The phishing campaign targets organizations in various sectors, with a significant concentration in:
- Technology
- Financial services
- Manufacturing
The malware enables attackers to:
- Exfiltrate stored browser credentials
- Steal cryptocurrency wallets
- Intercept banking credentials
- Capture screenshots and keystrokes
Given its wide distribution and stealthy infection chain, Lumma Stealer poses a major risk to both individual users and corporate networks.
The campaign has been observed across 260 unique domains, including popular content delivery networks like Webflow, GoDaddy, Strikingly, Wix, and Fastly. Some of the phishing PDFs have also been uploaded to online libraries and PDF repositories, further expanding the attack surface.
Netskope Threat Labs emphasizes the importance of being cautious when downloading PDF files from the internet, even from seemingly trustworthy sources. Users should avoid clicking on links or opening attachments from unknown senders and should always scrutinize website URLs before entering personal information.
