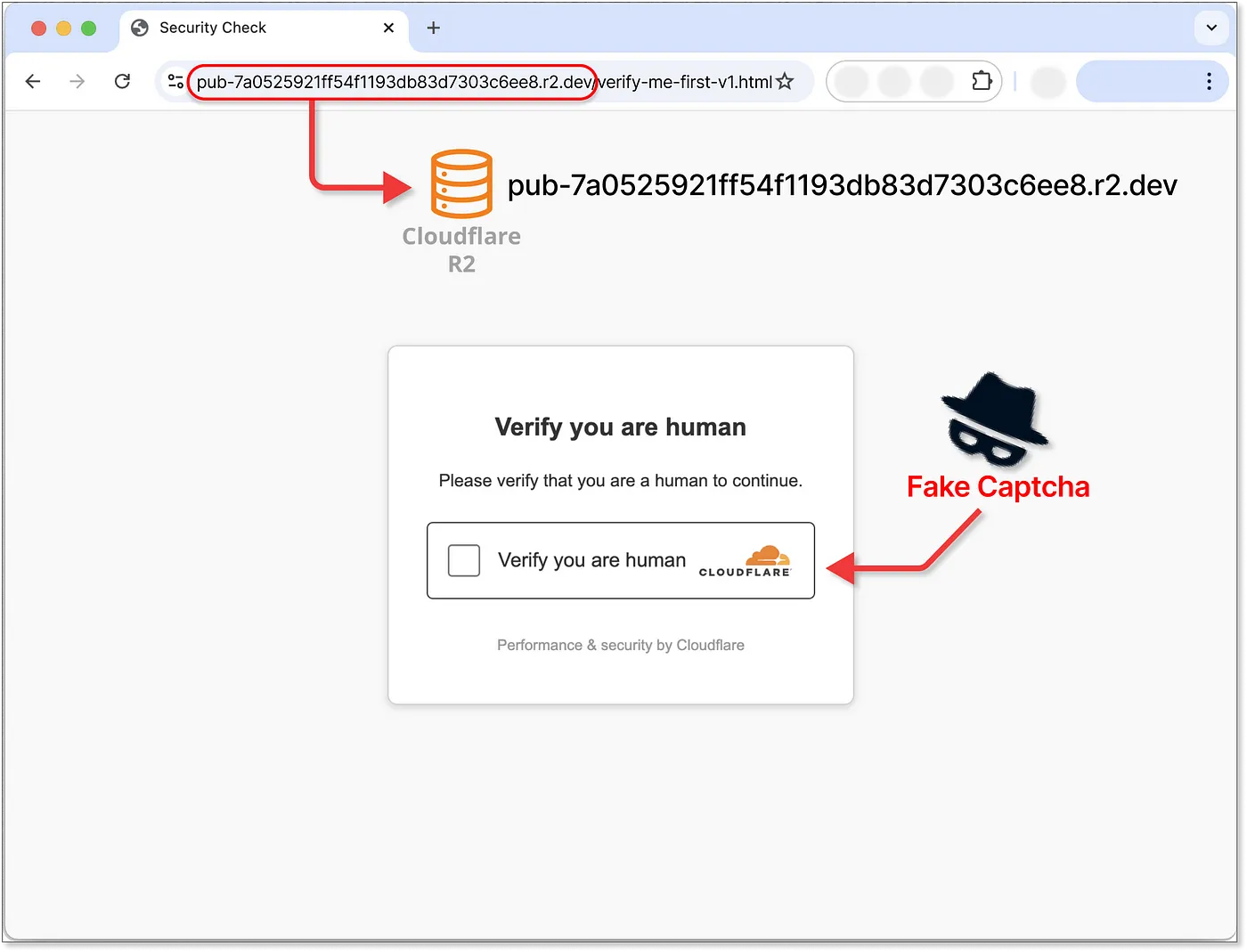
A Cloudflare-themed fake captcha page hosted on… Cloudflare R2 storage | Source: Guardio Labs
A large-scale malvertising campaign analyzed by Guardio Labs exposes how fake CAPTCHA prompts are used to deliver the Lumma infostealer malware. This sophisticated operation highlights the dark side of Internet advertising, leveraging ad networks to reach millions of victims daily.
For several weeks, Guardio Labs tracked a deceptive campaign distributing the Lumma infostealer malware through fake CAPTCHA prompts. Users browsing seemingly harmless content sites are tricked into performing actions that execute malicious PowerShell commands on their systems.
The process is cunningly simple:
- Users encounter a CAPTCHA-like page prompting them to confirm they are human.
- The page mimics a legitimate verification process but secretly copies and executes a PowerShell command.
- The command installs Lumma, an infostealer that exfiltrates social accounts, banking credentials, passwords, and personal files.
Guardio Labs explains the method’s effectiveness: “This seemingly legitimate captcha page appears unexpectedly as you browse a content site, perfectly mimicking a real verification process. It asks you to confirm you’re human through a series of keyboard clicks, which ultimately trigger the Run dialog on your Windows system.”
At the main of this campaign lies malvertising—a malicious twist on digital advertising. Guardio’s analysis revealed that the fake CAPTCHA traffic comes entirely from clicks on ads propagated through a single ad network: Monetag, a subsidiary of PropellerAds.
Guardio notes: “All the traffic directed to fake captcha pages came from ad clicks—thus, this entire campaign is based on malvertising.”
Key findings from the report include:
- 1 million daily ad impressions linked to fake CAPTCHAs.
- Traffic funneled through 3,000+ compromised or deceptive content sites, often hosting pirated or clickbait material.
- Malicious ads leveraging services like BeMob for cloaking, making moderation nearly impossible.
Threat actors cleverly abuse ad tracking platforms, such as BeMob, to evade detection. Instead of directly linking to malicious pages, they supply benign-looking URLs that redirect to fake CAPTCHA prompts. This allows them to bypass moderation efforts by ad networks.
Guardio describes this method: “By supplying a benign BeMob URL to Monetag’s ad management system instead of the direct fake captcha page, the attackers leveraged BeMob’s reputation, complicating Monetag’s content moderation efforts.”
The final payload—often hosted on cloud storage services like Oracle Cloud, Cloudflare R2, and Bunny CDN—adds another layer of obfuscation.
The scale of this campaign is staggering:
- Over 1 million ad impressions per day.
- 3000+ publisher sites actively distributing malicious ads.
- High-traffic sites, such as pirated streaming platforms, serving as distribution hubs.
Guardio Labs found that popular sites like “hianime.to” amassed over 100,000 unique visits per month, with aggressive SEO tactics ensuring they rank high in Google search results.
Upon Guardio’s disclosure, Monetag acted to ban over 200 fraudulent accounts linked to the threat actors. BeMob also responded by disabling cloaking accounts. However, the eight-day delay in enforcement highlights the reactive nature of current defenses.
Monetag stated: “We remain committed to strengthening our defenses, working collaboratively with researchers… The safety and integrity of our ecosystem are paramount.”
The fake CAPTCHA campaign underscores how legitimate ad networks can be weaponized for malicious purposes. While advertising is central to the internet’s economy, Guardio Labs warns that the lack of oversight creates a security gap that leaves users vulnerable.
Guardio concludes: “This fake captcha campaign is just one example that exposes the darker side of the internet’s advertising ecosystem. While advertising is a cornerstone of the modern internet, the same ecosystem now faces a significant conflict of interest — creating a security gap that leaves users vulnerable..”
To defend against such threats, users are advised to exercise caution when encountering CAPTCHA prompts, avoid clicking suspicious ads, and maintain updated security protections.
Related Posts:
- CrossBarking Vulnerability in Opera Browser Allows Malicious Extensions to Hijack User Accounts
- EchoSpoofing: Millions Targeted in Proofpoint Email Breach
- Cybercriminals Exploit CAPTCHA to Deliver Malware: Experts Issue Warning
- Artificial Intelligence will become a hacker artifact
- MaaS in Action: How Lumma Stealer Employs Advanced Delivery Techniques
