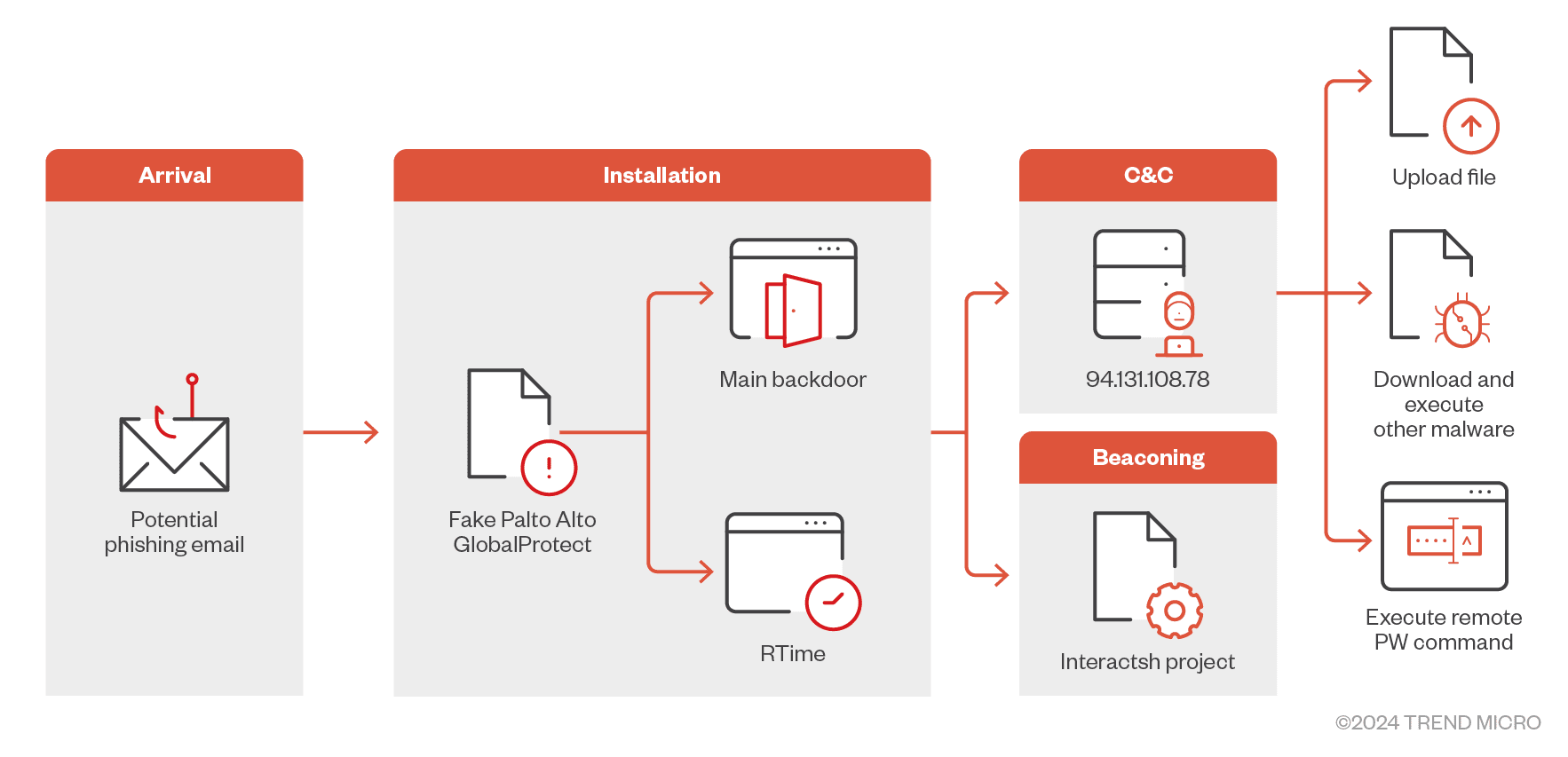
Infection chain of an attack | Image: TrendMicro
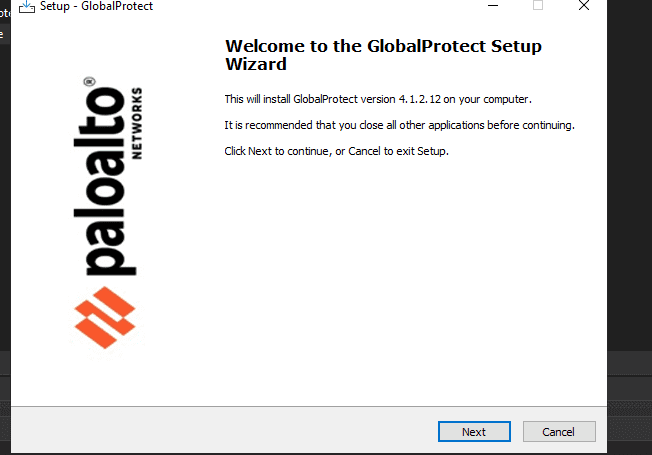
Trend Micro researchers have identified a sophisticated malware campaign specifically targeting organizations in the Middle East. This campaign leverages a meticulously crafted tool masquerading as the legitimate Palo Alto GlobalProtect VPN client to deceive victims into initiating the infection process.
The attack begins with the distribution of a malicious file named “setup.exe,” which masquerades as a legitimate installation package for Palo Alto Networks’ GlobalProtect VPN. Once executed, this file deploys “GlobalProtect.exe” along with configuration files “RTime.conf” and “ApProcessId.conf” into the victim’s system directory, specifically within the path C:\Users\(UserName)\AppData\Local\Programs\PaloAlto\.
This deception is further enhanced by the malware’s use of a command-and-control (C&C) infrastructure, which pivots to a newly registered URL, “sharjahconnect.” Named after Sharjah, one of the United Arab Emirates’ emirates, this domain is crafted to resemble a legitimate company VPN portal. This clever disguise not only aids in the initial infiltration but also allows the malware to maintain persistent access to compromised networks while blending seamlessly into regional network traffic.
A particularly notable aspect of this malware is its use of the Interactsh project, a tool typically used by penetration testers to verify exploit success, for beaconing purposes. By leveraging Interactsh, the malware sends DNS requests to domains within the oast[.]fun domain, such as step[1-6]-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun. These beaconing requests correspond to various stages of the infection process, from collecting machine information to executing commands received from the C&C server.
This method allows the threat actors to track the progress of their malware as it moves through the infection chain, providing them with real-time insights into which targets have been successfully compromised.
Written in C#, this malware can execute remote PowerShell commands, download and run additional payloads, and exfiltrate specific files from the infected machine. The malware’s command structure is versatile, allowing it to perform a variety of tasks, including:
- Executing PowerShell Scripts: The malware can run PowerShell commands and send the results back to the C&C server.
- Process Management: It can start new processes, download files from a specified URL, and upload stolen files to a remote server.
- Data Encryption: To secure its communications, the malware employs AES encryption, ensuring that data sent to the C&C server is protected from interception.
The combination of these capabilities makes the malware a potent tool for espionage and data theft, with the potential to cause significant damage to targeted organizations.
The malware also incorporates sophisticated evasion techniques designed to bypass behavior analysis tools and sandbox environments. By checking process file paths and specific files before executing its main code block, the malware can avoid detection in controlled analysis environments. Additionally, the use of newly registered domains for its C&C activities helps the malware evade detection by security blacklists, complicating efforts to attribute the attack to a specific threat actor.
Organizations in the Middle East, and indeed across the globe, must remain vigilant and take proactive steps to strengthen their defenses against such threats. This includes implementing robust endpoint protection solutions, regularly updating security protocols, and prioritizing employee education and awareness programs.
Related Posts:
- Palo Alto Networks Issues Security Advisories, Urges Updates Amidst 34 Vulnerabilities
- PAN-OS: PAN-OS Remote Code Execution Vulnerability
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Palo Alto Firewalls Under Attack: Critical Flaw Exploited to Deploy Cryptojacking Malware