Malicious application workflow. | Image: Check Point
In a recent investigation by Check Point Research (CPR), a sophisticated crypto scam was uncovered, leveraging a fake app impersonating the popular Web3 protocol, WalletConnect, to drain users’ cryptocurrency wallets. This malicious application, available on Google Play, remained undetected for over five months, victimizing more than 150 users and leading to financial losses exceeding $70,000.
Crypto drainers are a class of malicious tools designed to steal digital assets like tokens and NFTs from cryptocurrency wallets. These tools typically rely on phishing techniques to trick users into visiting fraudulent websites that mimic legitimate crypto platforms. Once the user is lured in, the drainers initiate unauthorized transactions and prompt victims to sign them, thereby transferring funds directly to the attacker.
As cryptocurrency wallets become increasingly secure and Web3 users grow more knowledgeable about such attacks, scammers have had to evolve their tactics. The latest scam uncovered by CPR marks the first time drainers have exclusively targeted mobile users, with a malicious app masquerading as WalletConnect to deceive unsuspecting users.
WalletConnect is an open-source protocol designed to bridge decentralized applications (dApps) and cryptocurrency wallets, using QR codes or deep links to enable secure transactions. It allows users to interact with dApps from their mobile wallets without exposing their private keys, making it an essential tool in decentralized finance (DeFi).
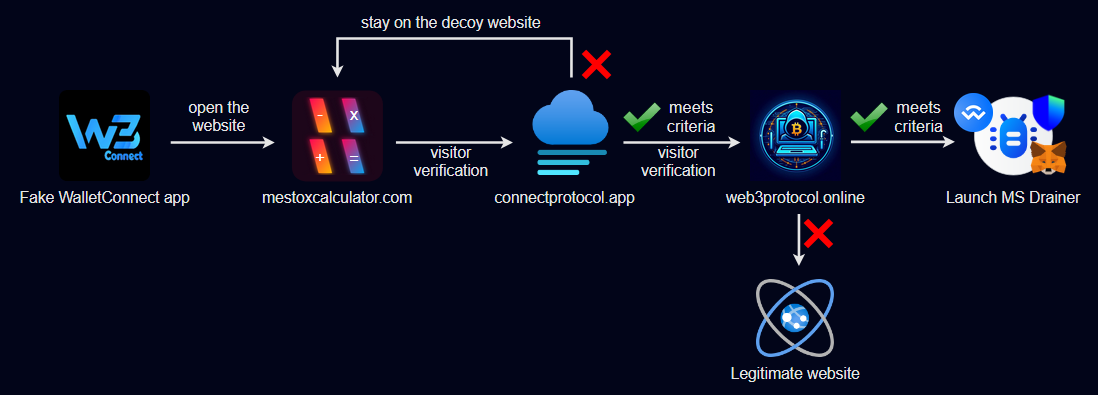
However, attackers exploited the reputation of WalletConnect, launching a fake app called “WalletConnect – Crypto Wallet” on Google Play. With high ratings and fake reviews, this app was able to deceive users into downloading it, especially when the legitimate WalletConnect name appeared at the top of search results.

Once downloaded, the malicious app mimicked the real WalletConnect workflow. When users attempted to connect their wallets to Web3 applications, the fake app prompted them to verify their wallets and sign several fraudulent transactions. Each of these interactions secretly sent encrypted messages to a command-and-control (C2) server, feeding the attackers with information about the user’s assets, wallet addresses, and blockchain networks.
The C2 server, hosted on cakeserver[.]online, then used this information to generate malicious transactions designed to drain the victim’s assets. The app cleverly utilized deep links and smart contracts to silently withdraw funds from users’ wallets, transferring the stolen tokens to the attackers’ wallets without raising any alarms.
The fake WalletConnect app went to great lengths to evade detection. It leveraged obfuscation and anti-analysis techniques to remain hidden from security tools like VirusTotal. Moreover, the app used user-agent checking and IP-based redirection to display harmless content, such as a multifunctional calculator, when accessed by security researchers or app store reviewers. This allowed it to bypass automated checks and remain on Google Play for an extended period.
Additionally, the app relied on external smart contracts and deep links to carry out its malicious activities. The use of smart contracts enabled the attackers to siphon off the most valuable assets from the victims’ wallets while optimizing transaction fees. This design also made the scam harder to detect since traditional permissions and keylogging methods were not used.
Through their analysis, CPR tracked the attackers’ wallet addresses and found that over 150 victims had been affected. The stolen funds, scattered across various Ethereum Virtual Machine (EVM) networks such as Ethereum, Binance Smart Chain (BSC), and Polygon, amounted to over $70,000. Most of the stolen assets were still sitting in the attackers’ wallets at the time of the report.
Interestingly, despite the scale of the scam, only around twenty victims left negative reviews on Google Play, indicating that many may still be unaware of how their funds were stolen. The app developers used fake positive reviews to drown out complaints, further complicating efforts to warn potential victims.