Image: Malwarebytes Labs
Search-based malvertising attacks escalated significantly in February, with Malwarebytes Labs reporting a near-doubling of incidents. Although some familiar payloads were observed, the emergence of new, evasion-focused malware underscores the dynamic nature of these attacks. One such threat, FakeBat malware, is actively being investigated by Malwarebytes Labs.
Inside the FakeBat Attack Strategy
The FakeBat threat actors have refined a multi-pronged approach designed to deceive users and bypass security measures:
-
Cloaked Redirects: Leveraging a mix of URL shorteners and compromised legitimate websites, attackers redirect unsuspecting users through a maze of sites before delivering malicious payloads. This obfuscation makes it difficult for traditional security tools to identify the true destination.
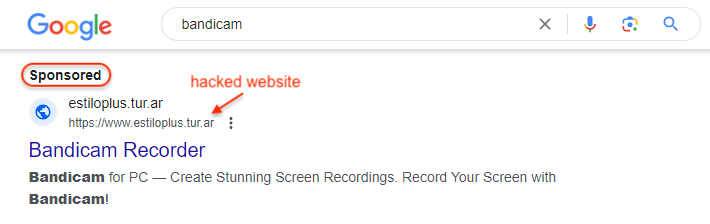
Image: Malwarebytes Labs -
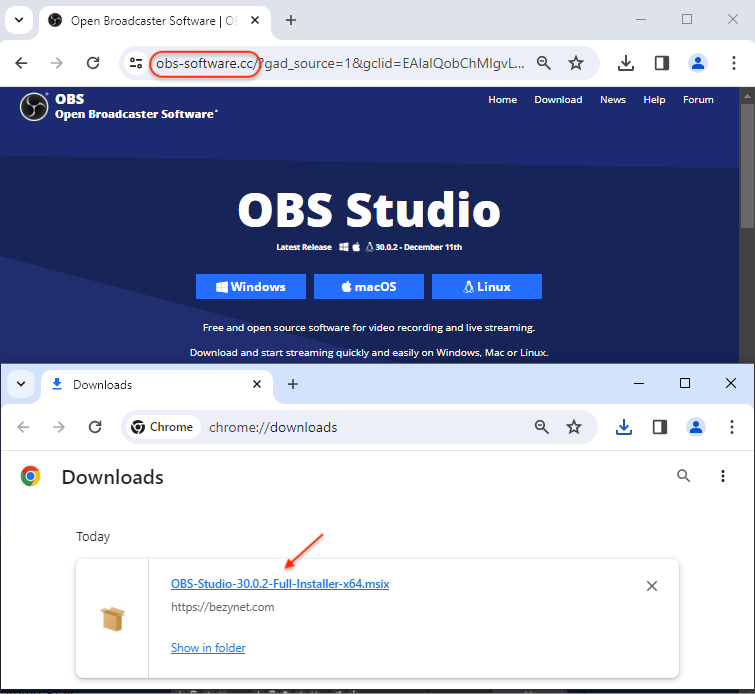
Deceptive Installers: FakeBat malware is often hidden within seemingly innocuous MSI installers. These installers are laced with heavily obfuscated PowerShell code, further hindering detection.

Image: Malwarebytes Labs -
Exploiting Trust with Code-Signing: To increase their success rate, attackers are abusing valid code-signing certificates, adding a false sense of legitimacy to their malware. This tactic can bypass initial security checks.
-
Target Diversification: FakeBat operators continuously expand their target range, impersonating a wide array of popular brands. This includes productivity software like OneNote, gaming platforms like Epic Games, financial tools, and even cryptocurrency applications like the Braavos wallet.
Defensive Measures: Protect Yourself and Your Organization
Staying ahead of evolving malvertising threats requires proactive measures and constant vigilance:
-
Scrutinize Search-Based Downloads: Exercise extreme caution when downloading software promoted through search ads. Double-check the publisher’s website directly and research any unfamiliar programs thoroughly before installing.
-
Ad-Blocking as a First Line of Defense: Ad-blocking tools, while not bulletproof, can significantly reduce your risk profile by minimizing exposure to malicious advertisements.
-
Prioritize Patches and Updates: Ensure that your operating systems, browsers, and all installed software are up-to-date with the latest security patches. Attackers often exploit known vulnerabilities, making patching critical.
-
Employee Awareness is Key: Conduct regular security training covering malvertising risks. Empower your team to identify and report suspicious ads or unexpected download prompts.
-
DNS Filtering for Network-Level Protection: Invest in specialized DNS filtering solutions to block known malicious domains and redirect chains, adding another layer of defense to your organization’s network.
The Importance of Adaptability
The FakeBat malvertising campaigns underscore how quickly the threat landscape evolves. Attackers relentlessly refine their techniques to exploit new opportunities and deceive users. To combat these threats, individuals and organizations alike must prioritize adaptability, maintain robust security posture, and invest in proactive defense strategies.