Image: Nextron Threat Research Team
Crafted by the notorious Peach Sandstorm APT group, the FalseFont backdoor has been specifically targeting defense contractors across the globe. Initially brought to light by Microsoft, FalseFont poses a significant threat due to its capabilities for data exfiltration and remote access. Its deceptive nature, disguised as a legitimate application from U.S. Defense and Intelligence Contractor Maxar Technologies, raises alarm bells for security experts and defense organizations alike.
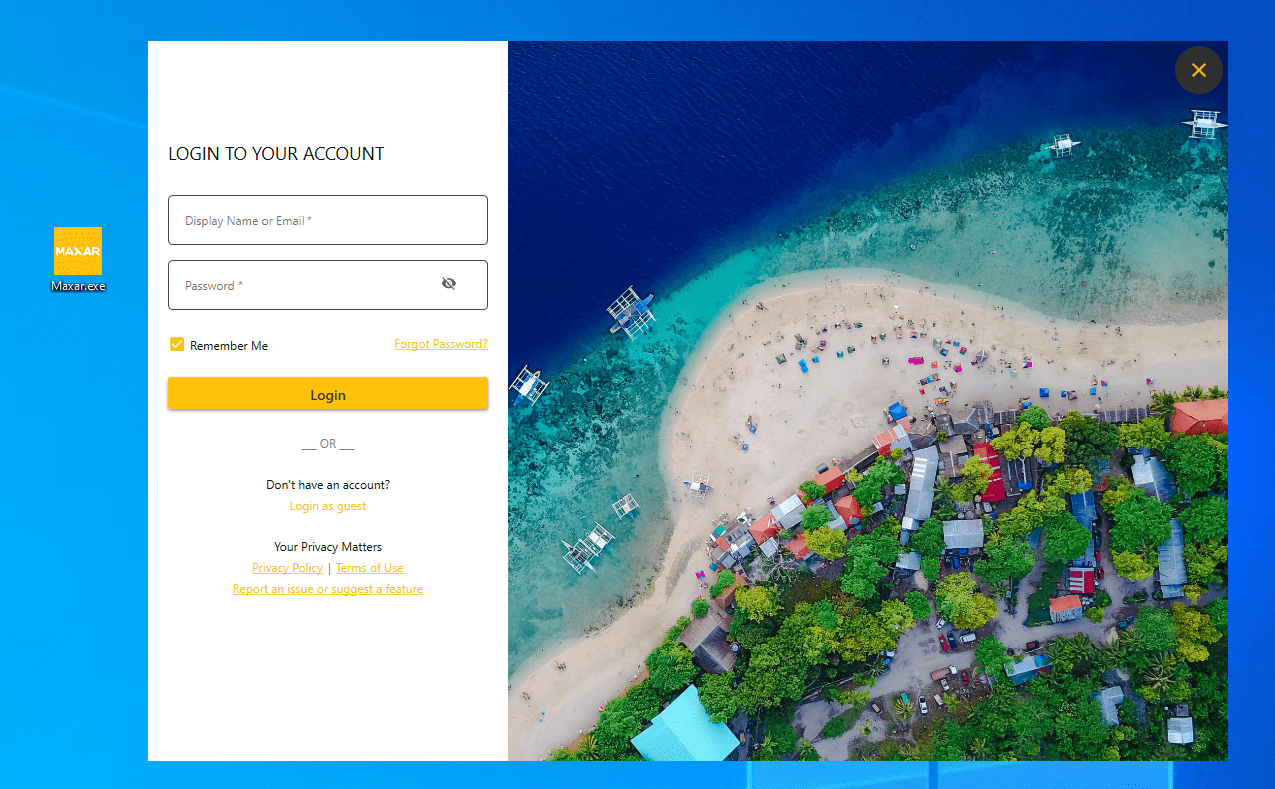
At first glance, the FalseFont backdoor appears as an innocuous login screen, convincingly mimicking the style and branding of Maxar Technologies’ website. Victims are prompted to log in or register as guests, entering their personal data. However, this facade is just the tip of the iceberg.

The meticulous analysis by the Nextron Threat Research Team revealed a more sinister agenda. An attempt to log in with random credentials leads to an infinite loading screen, a deliberate distraction as the malware begins its covert operations.
The Aurora Agent, a vigilant watchdog running on the system, detected multiple suspicious activities. It flagged several warning-level events typically associated with malware establishing persistence. However, the more subtle notice events were what unearthed the malware’s true intentions, revealing the first Command and Control (C2) server responsible for credential theft.
The FalseFont backdoor is coded in .NET, using the self-contained single-file host feature. This means the managed code is encapsulated within a native bootstrapping application. The Nextron team’s reverse engineering efforts began with the extraction of this managed code, leading to the discovery of the payload, Maxar.dll.
Further scrutiny in dnSpy exposed unobfuscated and lightly packed code. This included Windows Presentation Foundation (WPF) code responsible for the deceiving user interface.
FalseFont’s UI offered two login options: a standard and a guest login. The guest login, a facade for data collection, instructed users to await feedback from Maxar’s team, likely a ruse by the threat actor. It then directed the entered credentials to a hardcoded IP, hinting at espionage or identity theft purposes.
A key component of FalseFont is the SignalRHub class, utilizing Microsoft’s SignalR protocol for C2 communication. This allowed the malware to employ an array of commands, including reverse shells, browser credential theft, and real-time screen monitoring.
FalseFont employs various persistence mechanisms, with the Core.Agent.Utilities.Prerequisite class managing the replication and update of the agent. The Constants class houses config values and encrypted strings, decrypted using the same hardcoded key as the C2 communication, a potential weak point for detection.
FalseFont is not just a backdoor; it’s a multifaceted tool for remote access and data exfiltration, with a focus on monitoring user machines. Its primary target seems to be extracting confidential information related to U.S. Defense and Intelligence. While its complexity is daunting, its simplistic string encryption offers a glimmer of hope for cybersecurity professionals. Understanding FalseFont’s intricacies is crucial for bolstering defenses against such sophisticated threats. The battle against cyber threats like FalseFont is ongoing, demanding constant vigilance and innovation in cybersecurity measures.