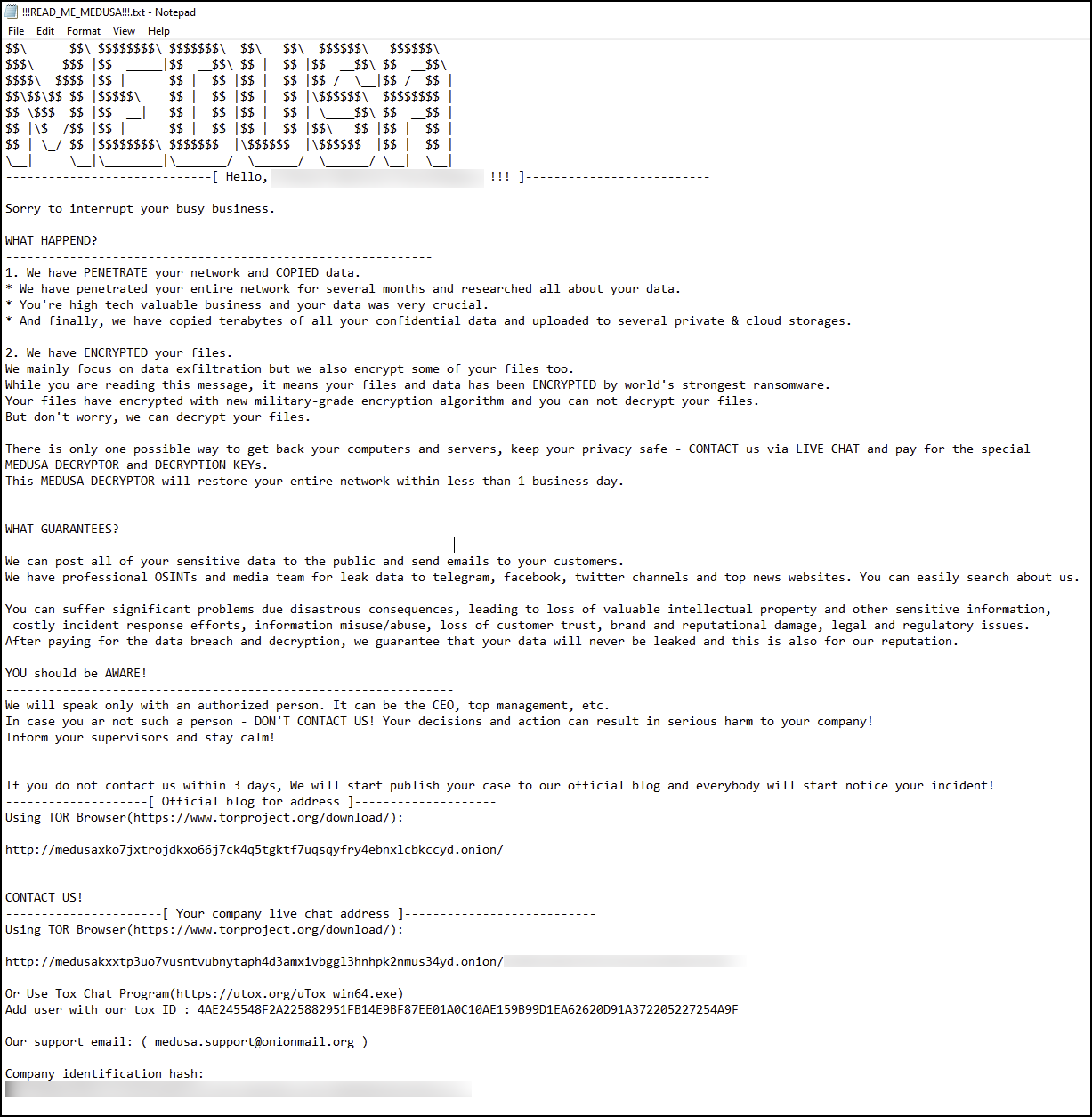
Medusa ransomware ransom note | Image: Unit 42
In a joint cybersecurity advisory, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) have issued a warning to organizations about the ongoing threat of Medusa ransomware. The advisory, released on March 12, 2025, details the tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with Medusa ransomware, urging organizations to take immediate action to protect themselves.
Medusa, a ransomware-as-a-service (RaaS) variant, was first identified in June 2021. Since then, it has evolved, and as of February 2025, Medusa developers and affiliates have impacted over 300 victims across various critical infrastructure sectors. The affected industries include medical, education, legal, insurance, technology, and manufacturing. This ransomware variant is not related to the MedusaLocker variant or the Medusa mobile malware variant.
The advisory highlights that Medusa actors employ a double extortion model. “Medusa actors…employ a double extortion model, where they encrypt victim data and threaten to publicly release exfiltrated data if a ransom is not paid,” the report states. This tactic increases pressure on victims to pay the ransom, as they face not only the loss of their data but also the potential for public exposure.
The advisory provides a comprehensive overview of the TTPs used by Medusa actors, including:
- Initial Access: Medusa developers often recruit initial access brokers (IABs) to gain entry into victim networks. These IABs may use various methods, such as phishing campaigns to steal victim credentials or exploiting unpatched software vulnerabilities.
- Defense Evasion: Medusa actors employ various techniques to avoid detection. This includes using living off the land (LOTL) tactics and legitimate tools, as well as deleting PowerShell command line history. In some cases, they have also attempted to use vulnerable or signed drivers to disable endpoint detection and response (EDR) tools.
- Lateral Movement and Execution: Medusa actors use legitimate remote access software and tools like Remote Desktop Protocol (RDP) and PsExec to move laterally through the network. “Medusa uses these tools—in combination with Remote Desktop Protocol (RDP) and PsExec—to move laterally through the network and identify files for exfiltration and encryption,” the advisory explains.
- Exfiltration and Encryption: To exfiltrate data, Medusa actors install and use Rclone. They then deploy the encryptor, often disabling Windows Defender and other antivirus services, to encrypt files with a .medusa extension.
The advisory provides several recommendations for organizations to mitigate the risk of Medusa ransomware attacks. These include:
- Patching and Updating Systems: Mitigating known vulnerabilities by ensuring operating systems, software, and firmware are patched and up to date is crucial. “Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats,” the advisory emphasizes.
- Network Segmentation: Segmenting networks to restrict lateral movement from initial infected devices and other devices in the same organization can help prevent the spread of ransomware.
- Filtering Network Traffic: Filtering network traffic by preventing unknown or untrusted origins from accessing remote services on internal systems can also enhance security.
- Implementing a Recovery Plan: The advisory recommends implementing a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location.
The FBI, CISA, and MS-ISAC strongly urge organizations to implement these mitigations to reduce the likelihood and impact of Medusa ransomware incidents.