Previously, Cisco’s security labs discovered that malware named VPNFILTER has infected more than 500,000 routers worldwide. The malware is believed to be completed by the country’s own back-end hacking team, primarily for spy purposes rather than for broilers to launch traffic attacks.

Cisco claims that VPNFILTER is a very advanced modular malware system that infects routers to steal account passwords for websites and other services.
What needs to be mentioned is that the attack still spread through the loopholes, that is, these routers did not update the firmware to use the old version with known vulnerabilities.
VPNFILTER, on the other hand, uses a vulnerability to infect a device on the network and then madly infects other routers in the same network that use vulnerabilities.
Cisco analyzed that VPNFILTER infected at least 500,000 devices in 54 countries or regions, including routers and some NAS storage devices.
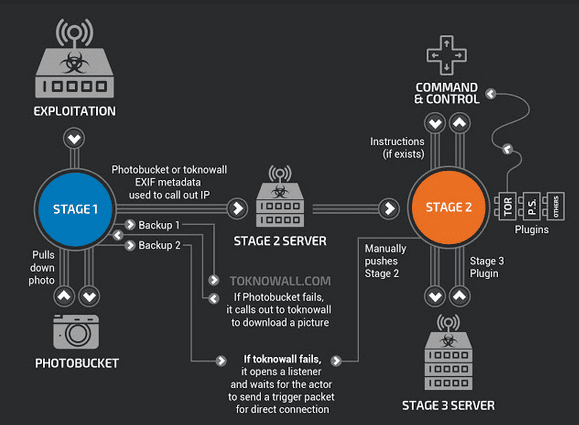
After a successful attack, VPNFILTER will sniff the network traffic to analyze the data, monitor the Modbus SCADA protocol, and steal other data.
The stolen data will be transmitted to the attacker’s server through the TOR onion network. Because TOR is private, it can avoid other people’s tracking.
VPNFILTER is not bootable and bootable as most route malware, so users only need to restart the device to stop the malware.
Due to a large amount of infection and harm, the U.S. Federal Bureau of Investigation issued an announcement to remind users to restart the device as soon as possible in order to remove the malware.
Affected equipment includes:
- Linksys E1200/E2500/WRVS4400N, Mikrotik RouterOS 1016/1036/1072 version, TPLink R600 VPN.
- Netgear DGN2200/R6400/R7000/R8000/WNR1000/WNR2000, QNAP TSNAP TS251/TS439Pro.