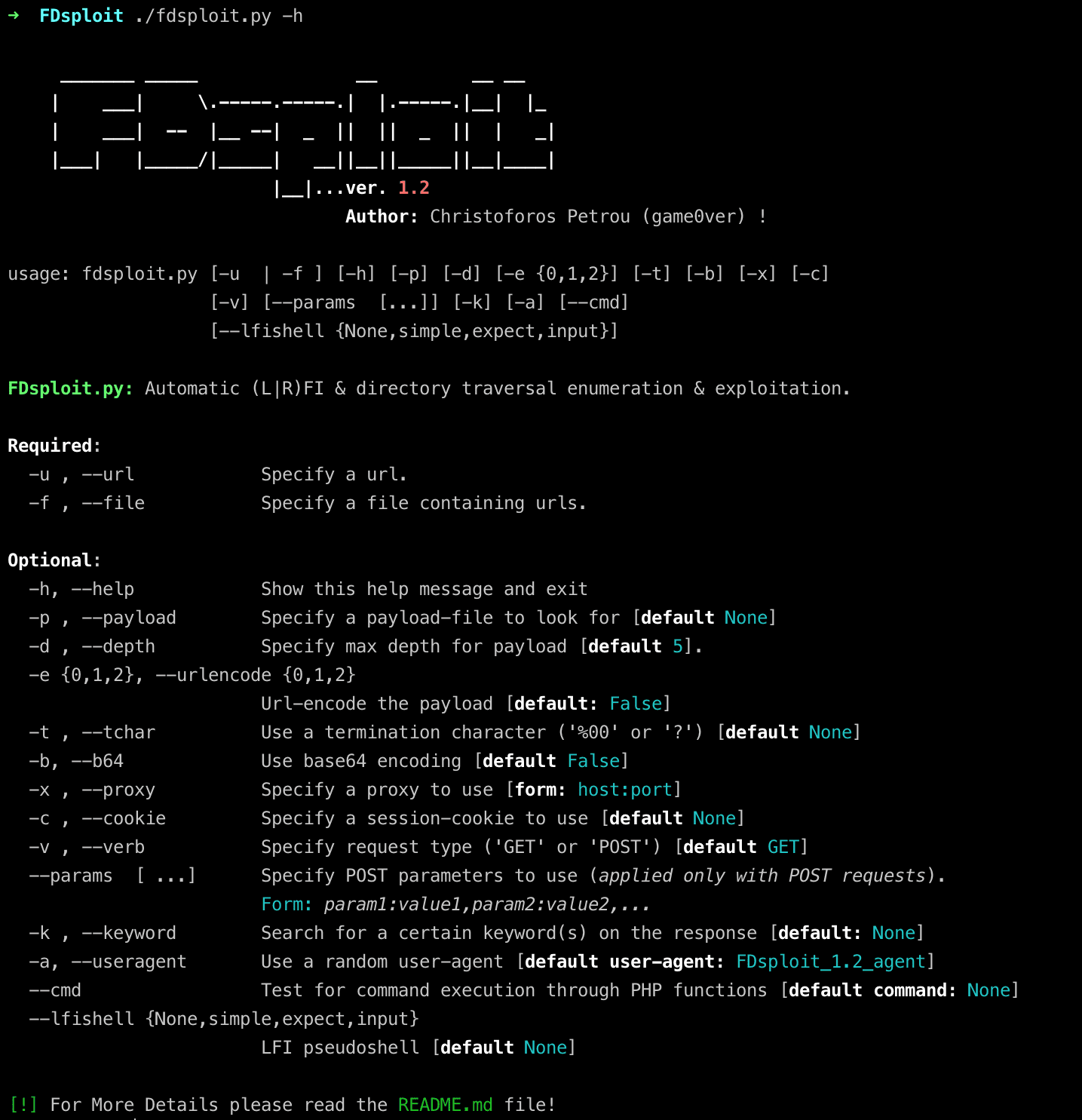
FDsploit: File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool
FDsploit
FDsploit is a File inclusion & Directory Traversal fuzzer, enumeration & exploitation tool.
Features
- The LFI-shell interface provides only the output of the file read or the command issued and not all the html code.
- 3 different types of LFI-shells can be specified.
- Both GET/POST requests are supported.
- Automatic detection of GET parameters.
- Certain parameters can be specified for testing using wildcards (
*). - Optional session cookies can be specified and used.
- Automatic check for RCE using PHP functions can be performed.
- Additional use of a sha-256 hash is used to identify potential vulnerabilities.
- base64/urlencoding support.
FDsploit can be used to discover and exploit Local/Remote File Inclusion and directory traversal vulnerabilities automatically. In case an LFI vulnerability is found, –lfishell option can be used to exploit it. For now, 3 different types of LFI shells are supported:
- simple: This type of shell allows a user to read files easily without having to type the url every time. Also, it only provides the output of the file and not the whole html-source code of the page which makes it very useful.
- expect: This type of shell is a semi-interactive shell which allows a user to execute commands through PHP’s expect://wrapper.
- input: This type of shell is a semi-interactive shell which also allows a user to execute commands through PHP’s php://input stream.
So far, there are only two lfi-shell built-in commands:
- clear and
- exit.
Download
git clone https://github.com/chrispetrou/FDsploit.git
pip install -r requirements.txt –upgrade –user
Use

Copyright (C) 2018 chrispetrou





