Fiddler XSRF Inspector : Finding XSRF vulnerability
Finding and exploiting a cross-site request forgery using Fiddler XSRF Inspector is trivial. The first step is to identify a privileged action to replicate. Some commonly targeted actions are listed below.
- Create new administrative user
- Grant admin privileges to user
- Change password of user
=== Installation ===
Download
Copy FiddlerXSRF.dll to the Fiddler 2 Inspectors folder, generally %ProgramFiles%\Fiddler2\Inspectors
=== Instructions ===
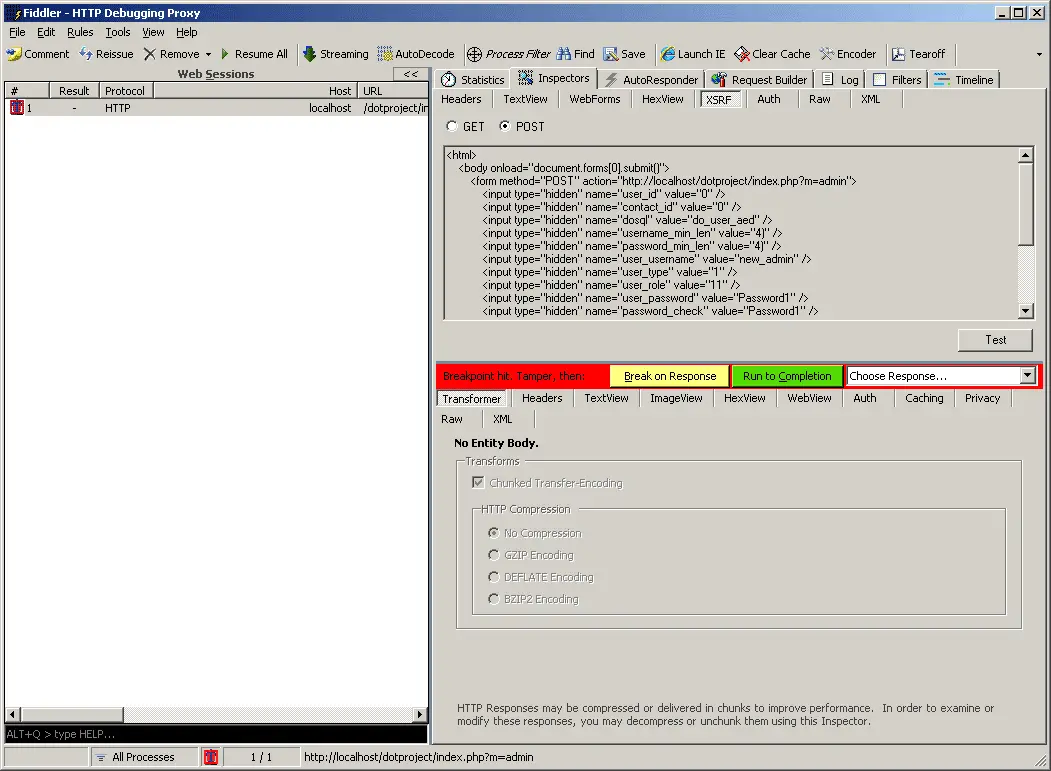
1) Capture the request that is going to be used to create a cross-site request forgery attack.
2) Navigate to the XSRF tab under inspectors to see the generated HTML. If the request uses the POST method, the option to convert it to GET will be available.
3) Click the Test button and observe the results.
Once a target has been selected, populate the appropriate form fields with data and set a breakpoint in Fiddler before submitting the form.
After submitting the form stop the request in the browser. In Fiddler disable the breakpoint or stop capturing but do not resume the captured request. Under the Inspectors tab select XSRF. If the request method is POST both GET and POST options will be available for testing, otherwise only GET is available.

Click the test button and observe the application to see if the desired effects have been achieved.
Source: https://www.autosectools.com/