whodunnit: powershell tool for filtering windows event logs
Whodunnit
Parse, Filter and Present Windows Event Logs with ease, from the comfort and familiarity of a PowerShell Environment.
Whodunnit is a forensic tool initially created with the intention of allowing the user to quickly sort windows event logs based solely on the user that was responsible for the generation of that log. Over time, this has evolved to allow for filtering on far more criteria than simply a username. The overreaching goal of this project was to reduce the time at the keyboard for a forensic investigator, by allowing for an automatable sorting process, and that is still the end goal. However, currently the command line interface is not operational, and the GUI is fully functional.

Whodunnit allows for a user to read windows event logs either from a previously exported dump or from the local machine. At the time, it reads all the logs that it has access to, meaning that in order to acquire the Security Logs, it must be run with proper permissions. Following reading in logs, the user has the option to load a filter from a previously exported filter, or create a custom filter.
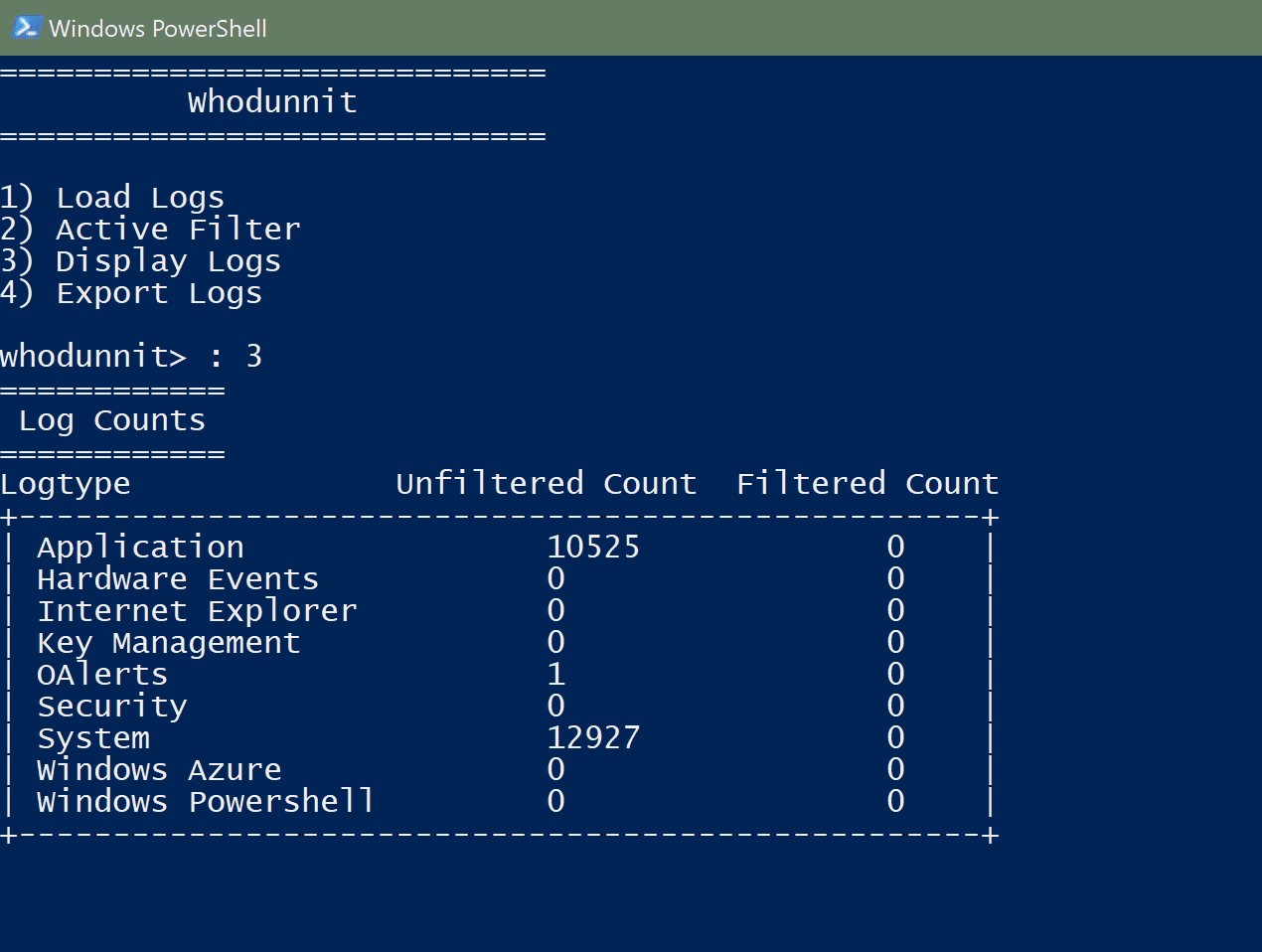
Currently, there are 6 properties that can be used to filter the logs loaded, including usernames, both a starting and ending date and time, event codes, event types, and event sources. The list of usernames entered is a negative search list, meaning all usernames included in that list will not be included in the final list of logs matching this filter. The time window filter selects only logs that fall between both of the times specified. If the start time is omitted, all logs before the end time are selected, and if the end time is omitted, all logs after the start time are selected. The list of event codes is a positive search list, with a default value of ‘*’. If ‘*’ is anywhere in the list of specified codes, all event codes are accepted. The ‘event types’ criteria allow the user to select event types to include, from a list. Available options are Error, Warning, Information, Success Audit, and Failure Audit. Finally, the ‘event sources’ criteria allow the user to select which sources to include in the final set of logs. Available sources are Application logs, Hardware Event logs, Internet Explorer logs, Key Management logs, OAlerts logs, Security logs (requires administrative rights), System logs, Windows Azure logs, and Windows PowerShell logs.
The active filter is applied immediately after backing out of the editing menu, or immediately after loading a filter from a file. This may take a significant amount of time, especially if system logs are included, or if a significant number of logs are being sorted through. The filtering algorithm is O(n * (j + k + l)), where ‘n’ is the number of logs to filter through, note that the sources are stored independently, and only sources in the current filter are looked at. ‘j’, k’, and ‘l’ are the lengths of usernames, event codes and event types lists.
Interactive mode Menu Options
+ Read In Log Files
- + Read from File
- + Read from Local Machine
- ? Read from Remote Machine
- ?Requires PSRemoting
- ?Requires Admin Creds to box
+ Set Active Filter
- + Export Active Filter to File
- + Load Filter From File
- + Filter Options
- + Username
- +Negative Selection
- + Username
-
- + Time Window
- +Start time
- +End time
- + Event Types
- +Positive Selection
- + Type
- +Positive Selection
- + Source
- +Positive Selection
- + Time Window
+ Display Log Files
- + Log files which match the active filter+ Export Log Files
- + Export all Read Log files
- + Export all Log files that match active filter
Download
git clone https://github.com/1cysw0rdk0/whodunnit.git
Use
Source: https://github.com/1cysw0rdk0/





