fingerprintx v1.1.10 releases: rapidly fingerprint the service running on all the discovered ports
fingerprintx
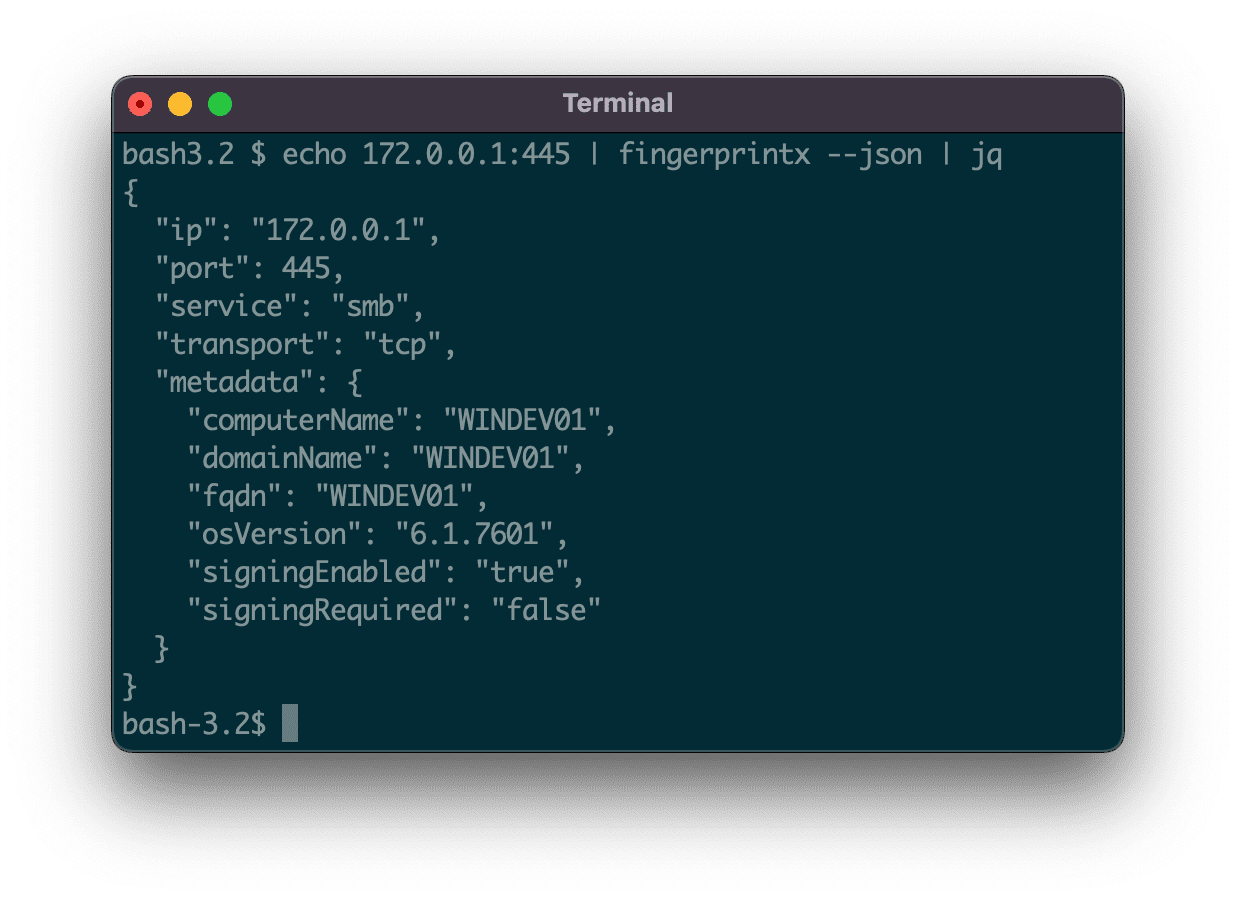
fingerprintx is a utility similar to httpx that also supports fingerprinting services like as RDP, SSH, MySQL, PostgreSQL, Kafka, etc. fingerprintx can be used alongside port scanners like Naabu to fingerprint a set of ports identified during a port scan. For example, an engineer may wish to scan an IP range and then rapidly fingerprint the service running on all the discovered ports.

Features
- Fast fingerprinting of exposed services
- Application layer service discovery
- Plays nicely with other command-line tools
- Automatic metadata collection from identified services
Supported Protocols:
| SERVICE | TRANSPORT | SERVICE | TRANSPORT |
|---|---|---|---|
| HTTP | TCP | REDIS | TCP |
| SSH | TCP | MQTT3 | TCP |
| MODBUS | TCP | VNC | TCP |
| TELNET | TCP | MQTT5 | TCP |
| FTP | TCP | RSYNC | TCP |
| SMB | TCP | RPC | TCP |
| DNS | TCP | OracleDB | TCP |
| SMTP | TCP | RTSP | TCP |
| PostgreSQL | TCP | MQTT5 | TCP (TLS) |
| RDP | TCP | HTTPS | TCP (TLS) |
| POP3 | TCP | SMTP | TCP (TLS) |
| KAFKA | TCP | MQTT3 | TCP (TLS) |
| MySQL | TCP | RDP | TCP (TLS) |
| MSSQL | TCP | POP3S | TCP (TLS) |
| LDAP | TCP | LDAPS | TCP (TLS) |
| IMAP | TCP | IMAPS | TCP (TLS) |
| SNMP | UDP | Kafka | TCP (TLS) |
| OPENVPN | UDP | NETBIOS-NS | UDP |
| IPSEC | UDP | DHCP | UDP |
| STUN | UDP | NTP | UDP |
| DNS | UDP |
Why Not Nmap?
Nmap is the standard for network scanning. Why use fingerprintx instead of nmap? The main two reasons are:
- fingerprintx works smarter, not harder: the first plugin run against a server with port 8080 open is the http plugin. The default service approach cuts down scanning time in the best case. Most of the time the services running on ports 80, 443, and 22 are http, https, and ssh — so that’s what fingerprintx checks first.
- fingerprintx supports json output with the –json flag. Nmap supports numerous output options (normal, xml, grep), but they are often hard to parse and script appropriately. fingerprintx supports json output which eases integration with other tools in processing pipelines.
Changelog v1.1.10
- Bug fix: #22
Install & Use
Copyright (C) 2023 praetorian-inc





