
In a joint advisory, the Five Eyes intelligence alliance has warned of a widespread and ongoing cyberattack campaign attributed to the Chinese state-sponsored group, Flax Typhoon. This campaign leverages a botnet constructed by exploiting 66 known vulnerabilities in routers, IoT devices, and web applications, posing a significant risk to critical infrastructure globally.
Flax Typhoon is zeroing in on devices from several prominent manufacturers. The vulnerabilities exploited are spread across products from the following companies:
- Apache: 10 vulnerabilities
- Cisco: 5 vulnerabilities
- Zyxel: 3 vulnerabilities
- QNAP: 3 vulnerabilities
- Fortinet: 3 vulnerabilities
- Draytek: 3 vulnerabilities
- WordPress: 2 vulnerabilities
- IBM: 2 vulnerabilities
- F5 Networks: 2 vulnerabilities
Organizations utilizing equipment from these manufacturers are strongly advised to review their systems immediately and address any identified vulnerabilities.
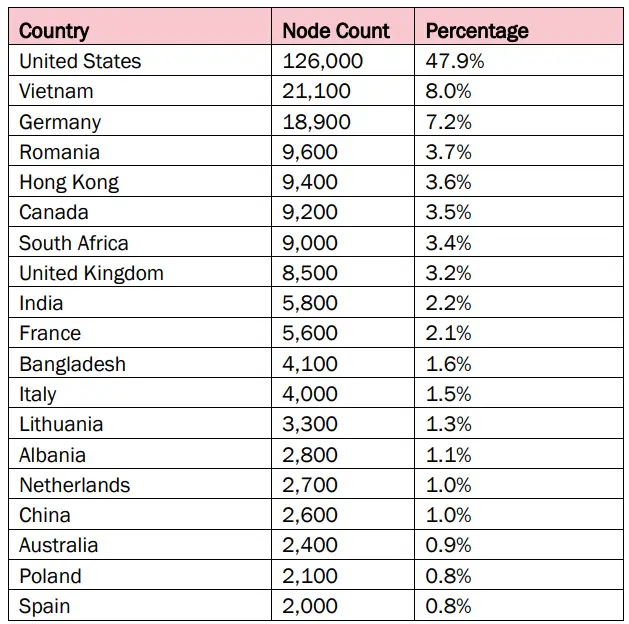
The analysis reveals a startling concentration of infected devices:
- United States: 47.9% of infected devices
- Vietnam: 8%
- Germany: 7.2%
- Other Affected Countries: Canada, the United Kingdom, India, and more
The high percentage of infected devices in the United States underscores a significant threat to the nation’s critical infrastructure sectors, including energy, healthcare, and finance.
At the time the warning was issued:
- 41 out of 66 vulnerabilities were already listed in the VulnCheck Known Exploited Vulnerabilities (KEV) database.
- 27 vulnerabilities were included in the Cybersecurity and Infrastructure Security Agency’s (CISA) KEV catalog.
Following the alert, VulnCheck updated its database to include all 66 vulnerabilities exploited by Flax Typhoon botnet. CISA is expected to update its catalog imminently.
To protect against the Flax Typhoon botnet and similar threats, the FBI strongly recommends organizations implement the following measures:
- Reduce attack surface: Disable unused services and ports.
- Implement network segmentation: Contain potential breaches and limit lateral movement.
- Monitor network traffic: Watch for unusual traffic patterns indicative of botnet activity.
- Apply patches and updates: Address known vulnerabilities promptly.
- Replace default passwords: Use strong, unique passwords for all devices.
- Regularly reboot devices: This can help remove malware from memory.
- Replace outdated equipment: Phase out devices that are no longer supported by the manufacturer.
The Flax Typhoon campaign underscores the importance of adopting a comprehensive and proactive approach to vulnerability management. Organizations are urged to move beyond mere vulnerability identification and prioritize remediation efforts based on evidence of active exploitation, environmental context, and other risk factors. The use of up-to-date threat intelligence is vital for effective risk mitigation.
Related Posts:
- Security flaws in critical infrastructure software could have meant disaster
- US/UK warn Russia to hack into global routers