Image: Ebryx
Cybersecurity researchers at Ebryx have identified two vulnerabilities in Fluent Bit, a widely used open-source log processor and forwarder. These vulnerabilities, tracked as CVE-2024-50608 and CVE-2024-50609, could allow attackers to launch denial-of-service (DoS) attacks, potentially disrupting operations for millions of users.
Fluent Bit is a lightweight, high-performance log processor and forwarder that integrates with cloud services, security platforms, and monitoring tools such as Elasticsearch, AWS, Azure, Google Cloud, and Kubernetes. The software sees over 15 billion downloads and is deployed 10 million times daily, making it a critical component of enterprise logging infrastructure.
Both CVE-2024-50608 and CVE-2024-50609 reside in Fluent Bit’s Prometheus Remote Write and OpenTelemetry plugins, which are used for collecting and forwarding monitoring data.
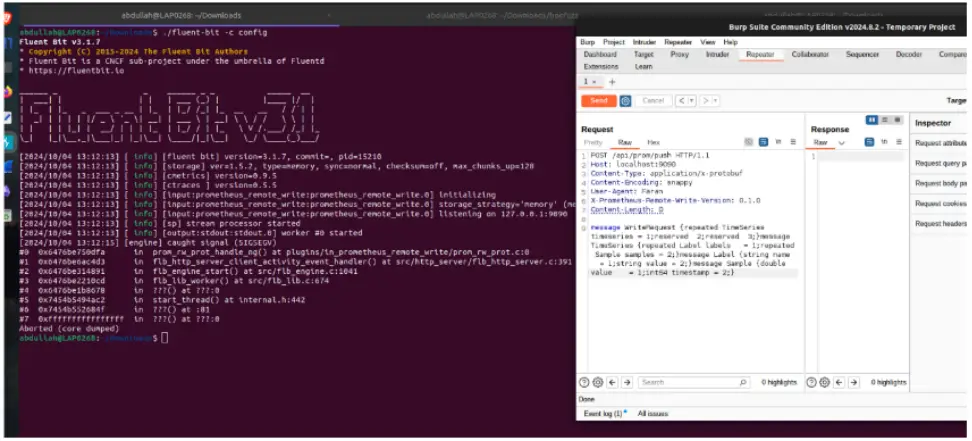
“An attacker can send a packet with Content-Length: 0 , causing the server to crash. The improper handling of the Content-Length value being zero allows any user with access to the endpoint to execute a remote denial of service attack,” Ebryx explained.
Ebryx researchers successfully exploited the flaws using a simple cURL command, demonstrating how attackers can remotely crash a vulnerable Fluent Bit server.
Ebryx has responsibly disclosed the vulnerabilities to the Fluent Bit maintainers, who have released patches to address the issues. Users of Fluent Bit are strongly urged to update their installations to the latest version to mitigate the risk of DoS attacks.
Related Posts:
- Linguistic Lumberjack (CVE-2024-4323): Critical Vulnerability Shakes Cloud Logging Infrastructure
- Unauthenticated Attackers Can Hijack 400K+ WordPress Sites via Fluent Forms Bug (CVE-2024-2771)
- Hacker forged Windows 11 upgrade website to trick users to download the virus