Fnord v0.6 releases: Pattern Extractor for Obfuscated Code
Fnord
Fnord is a pattern extractor for obfuscated code
Fnord has two main functions:
- Extract byte sequences and create some statistics
- Use these statistics, combined length, number of occurrences, similarity and keywords to create a YARA rule
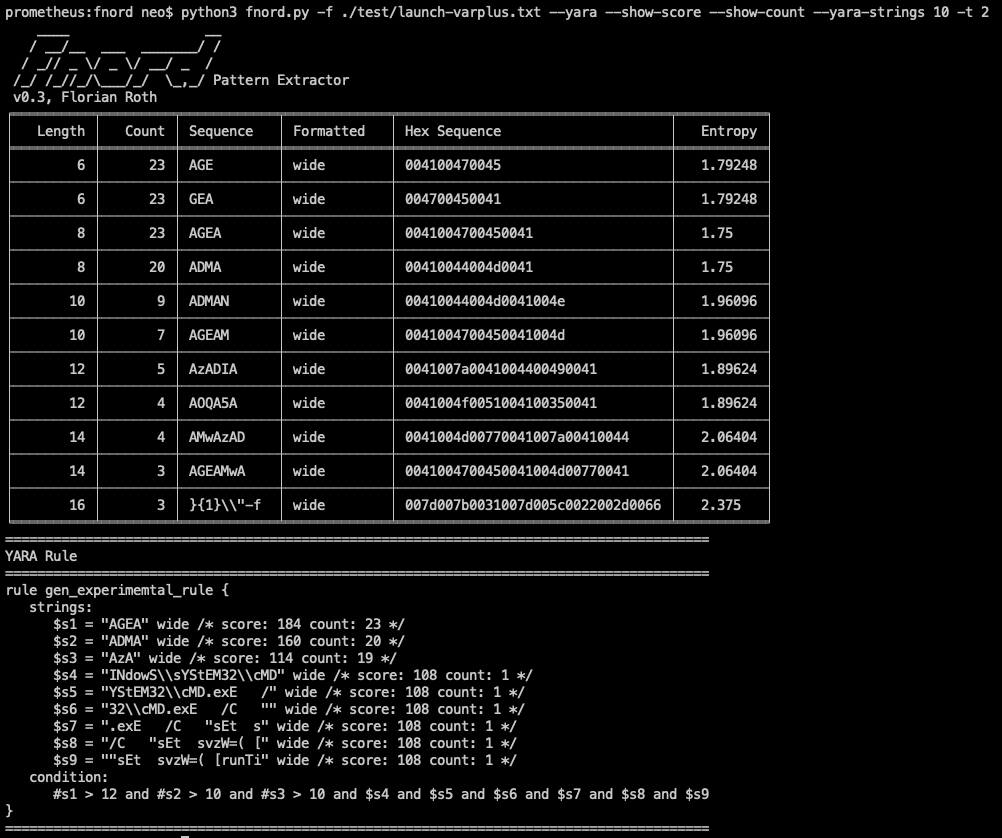
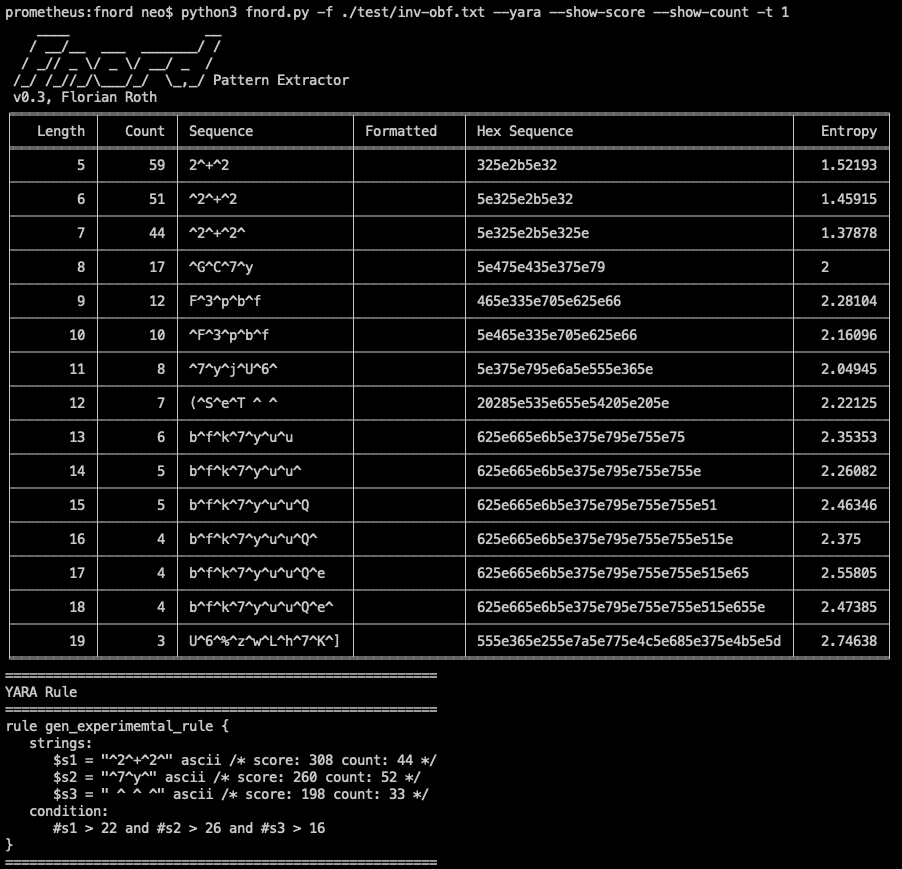
1. Statistics
Fnord processes the file with a sliding window of varying size to extract all sequences of with a minimum length -m X (default: 4) up to a maximum length -x X (default: 40). For each length, Fnord will present the most frequently occurring sequences -t X (default: 3) in a table.
Each line in the table contains:
- Length
- Number of occurrences
- Sequence (string)
- Formatted (ascii/wide/hex)
- Hex encoded form
- Entropy
2. YARA Rule Creation
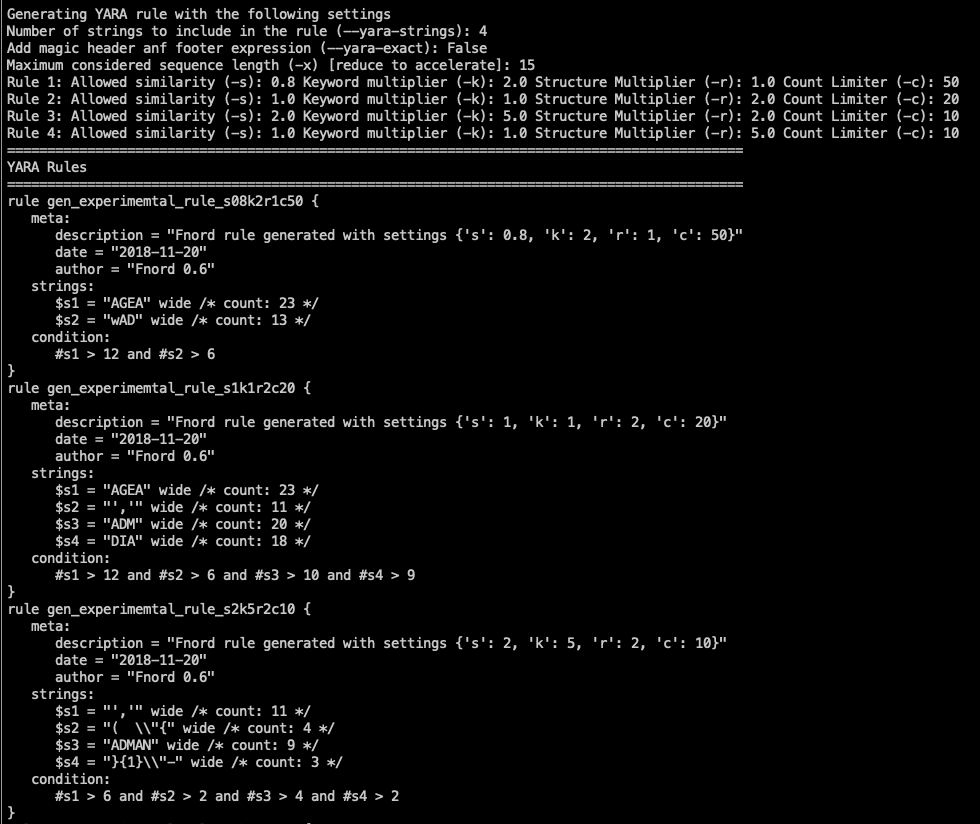
By using the –yara flag, Fnord generates an experimental YARA rule. During YARA rule creation it will calculate a score based in the length of the sequence and the number of occurrences (length * occurrences). It will then process each sequence by removing all non-letter characters and comparing them with a list of keywords (case-insensitive) to detect sequences that are more interesting than others. Before writing each string to the rule Fnord calculates a Levenshtein distance and skips sequences that are too similar to sequences that have already been integrated in the rule.
Status
[Experimental] Fnord was created a few days ago and I have tested it with a handful of samples. My guess is that I’ll adjust the defaults in the coming weeks and add some more keywords, filters, scoring options.
Improve the Results
If you’ve found obfuscated code in a sample, use a hex editor to extract the obfuscated section of the sample and save to a new file. Use that new file for the analysis.
Play with the flags -m, –yara-strings and -e.
Please send me samples that produce weak YARA rules that could be better.
Changelog v0.6
- The flag –yara is the default now, use –noyara to deactivate the YARA output
- different presets are used to generate a set of possible YARA rules
- fine tuning with -s, -k, -r, -c command line flags
Install
git clone https://github.com/Neo23x0/Fnord.git and cd Fnord pip3 install -r ./requirements.txt python3 ./fnord.py --help
Usage

Example
Copyright (C) 2018 Neo23x0
Source: https://github.com/Neo23x0/