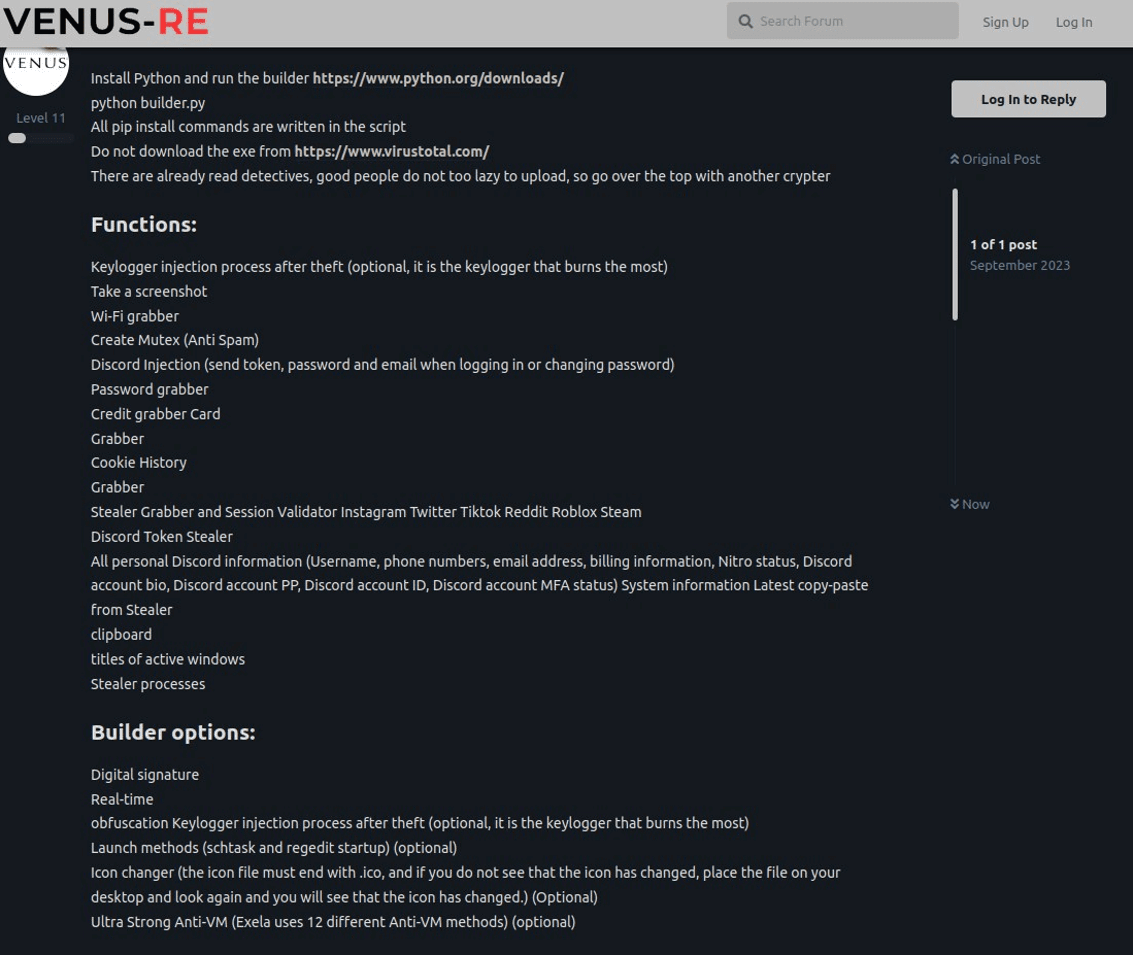
Advert detailing the malware’s major capabilities and some build options
The recent emergence of the ExelaStealer data pilferer has bolstered the hackers’ repertoire, aiming to purloin sensitive information from infected Windows systems. According to James Sloter, a researcher at FortiGuard Labs, ExelaStealer is an open-source info-stealer with premium configurations, actively backed by a cadre of cyber criminals.
The software, crafted in Python and bolstered by JavaScript, possesses the capability to abscond with passwords, Discord tokens, credit card details, cookie files, session data, keystrokes, clipboard content, and even to capture screenshots of active applications.
ExelaStealer is available for purchase on cybercrime forums and via a dedicated Telegram channel. Its creators operate under the pseudonym quicaxd. The premium version is priced at $20 for a single month, $45 for a quarterly subscription, or $120 for a perpetual license.

Its modest price point renders it an exemplary tool for novices in the realm of hacking, thereby lowering the threshold for executing malicious onslaughts.
There’s evidence to suggest that ExelaStealer infiltrates victims’ computers through an executable masquerading as a PDF document, though this is likely not its sole delivery method.
Researchers discerned that upon initiating the counterfeit PDF they studied, a document is prominently displayed – a Turkish registration certificate for a Dacia Duster vehicle – whilst the info-stealer operates surreptitiously in the background.
“Data has become a valuable currency, and because of this, attempts to gather it will likely never cease. InfoStealer malware exfiltrates data belonging to corporations and individuals that can be used for blackmail, espionage, or ransom. Despite the number of infostealers in the wild, ExelaStealer shows there is still room for new players to emerge and gain traction,” Sloter concluded.